Installing and configuring the 2004 ISA Server Firewall - Chapter 1
In fact today information security is playing an essential role, not a 'secondary' in all activities related to the application of information technology. I want to talk about the great role of IT application which has been happening in a dynamic way, not only purely as tools (Hardware, software), but really has been considered as a solution to many problems.
Starting from the early 90s, with a small number of IT experts, the knowledge is limited and the application of IT in production, transaction and management activities is still quite modest and only stops at the tool level, and sometimes I find these 'expensive' tools also cause some hindrance, not to bring practical effects to Organizations using it.

And those who are "most busy" ask themselves' what to buy the equipment to do atrium ?! it does not produce the product, and it does not help reduce the paperwork, how do we lose some useless money ?! Not far from regional neighbors like Thailand, Singapore, strong economies in the region and on the rise. Recognizing the superiority of IT application, and very soon they brought IT industry to apply to all activities, not only production, transaction, management but IT was brought to every home, everyone. And they also learn the skills to solve and control very creative work from these modern 'weapons'. Somewhere in Bill Gates' 'The Way Forward' excerpt refers to the tremendous value of information in the 21st century, an era of true information. This 'immaterial' precious entity, is gradually becoming a sought-after, rigorously controlled object, and a launching pad for all countries that want to develop strongly, quickly and 'lasting'. It is necessary to have the most powerful systems to control information, create information and bring this information into application effectively. The step-by-step world in technique 21 uses IT pedals to leverage and also to guide activities, bring people closer together, making Geographical differences no longer exist, easy to understand. each other and exchange with each other the most valuable, most special things.
Applying information technology in an effective and 'sustainable' way, is the top criteria of many countries today, Vietnam is no exception. In terms of an enterprise when applying IT to production, business always wants to have this. Efficiency is imperative, and 'sustainability' is also inevitable. From the perspective of a system security expert, when implementing an information system and building a tight and safe protection mechanism, this contributes to maintaining the system's 'sustainability'. information of that business. And we all understand that the value of corporate information is invaluable. Not only materially, what other values cannot be measured as their reputation with customers, if the information traded with customers is stolen, then be taken advantage of with the different purposes.Hacker, attacker, virus, worm, phishing, these concepts are now unfamiliar, and are really a top concern of all information systems (PCs, Enterprise Networks, Internet, etc .). And therefore, all these systems need to be equipped with powerful tools, knowledgeable about how to deal with those frightening black forces. Who created this powerful enough firewall to be able to 'burn' every intention to infiltrate ?! Please be aware that first of all, it is the awareness of all employees in the organization to use the secure computer, the knowledge of the Security Administrators in that Organization, and ultimately the most powerful tools. serve this 'war'. These are the Firewall, from Personal Firewall to protect each Computer to the Enterprise Firewall capable of protecting an organization's Network system. And Microsoft ISA Server 2004 is such an Enterprise Firewall! A good product and a trusted friend to secure information systems.
CHAPTER 1: Instructions for use
Chapter 2: Installing Certificate Services
CHAPTER 3: Install and configure Microsoft Internet Authentication Service
Chapter 4: Installing and configuring Micosoft DHCP and WINS Server Service
Chapter 5: Configuring DNS and DHCP to support Autodiscovery for Web Proxy and Firewall Client
Chapter 6: Installing and configuring the DNS Server with Caching-only feature on Perimeter Network
Chapter 7: Install ISA Server 2004 on Windows Server 2003
CHAPTER 8: Backup and restore Firewall configuration
Chapter 9: Simplify Network configuration with Network Templates
Chapter 10: Configuring ISA Clients: SecureNAT, Web Proxy and Firewall Client
Chapter 11: Configuring policies on the Firewall with the ISA Server 2004 Access Policy
Chapter 12: Publish Publish Services on Perimeter Network to outside: Web, Ftp Server
Chapter 13: Firewall Configuration acts as the Filtering SMTP Relay
Chapter 14: Proceed to publish Exchange Outlook Web Access, SMTP Server and POP3 Server Sites.
Chapter 15: Configuring VPN Server on ISA Server 2004
Chapter 16: Create a Site to Site VPN on ISA Server 2004 Firewalls
CHAPTER 1: Deploying Network infrastructure with essential Services
The book is presented according to the actual implementation of ISA Server 2004 in an organization's Network model. The content of the book encapsulates the ISA Server 2004 system configuration issues to become a powerful Firewall that still satisfies the requirements of using remote services, serving both internal ISA Clients to access the Service. external (Internet), and external clients (Internet Clients) need to access the Services within the Organization Network.
Firewalls has always been one of the most complex configurable Network devices and maintaining its operation to protect the Network has faced many challenges for the Security Admin. Basic knowledge of TCP / IP and Network Services is needed to understand how a Firewall works. However, it is not necessary to become an expert on Network Infrastructure to use ISA Server 2004 as a Network Firewall.
This chapter will describe the following issues:
• Help you understand features available on ISA Server 2004
• Provide specific advice when using documents to configure ISA Server 2004 Firewall
• Describe detailed implementation practices (ISA SERVER 2004 Lab Configuration).
Understand the features on ISA Server 2004
ISA Server 2004 is designed to protect Network, prevent external intrusion and control access from within an organization's Internal Network. ISA Server 2004 Firewall does this through mechanisms that control what can be allowed through the Firewall and what will be blocked. We can imagine as simple as this: There is a rule imposed on the firewall to allow information to be transmitted through the firewall, then this information will be 'Passed', and vice versa without any rules. Which allows these information to pass, this information will be blocked by Firewall.
ISA Server 2004 Firewall contains many features that Security Administrators can use to secure Internet access, and also to ensure security for resources within the Network Internal. The book provides the Security Admin with an understanding of the general concepts and uses the most common, specific features on ISA Server 2004, through specific steps (Steps by Steps).
Firewalls do not work in a 'vacuum' environment, because we simply deploy the Firewall to protect something, be it a PC, a Server or a Network system with many services deployed. Web, Mail, Database .
We will have a complete guide on deploying the services needed for an organization's Network operation. How to install and configure these services. And the most important thing is that Network and Services must be properly configured before deploying Firewall. This helps us avoid the frustrating problems that arise when deploying ISA Server 2004.
Network Services and features on ISA Server 2004 will be installed and configured including:
• Install and configure Microsoft Certificate Services (Service provides Digital Documents for secure identification when dealing on the Network)
• Install and configure Microsoft Internet Authentication Services (RADIUS) Service for secure authentication of remote access via remote connections (Dial-up or VPN)
• Install and configure Microsoft DHCP Services (Service provides TCP / IP settings for nodes on Network) and WINS Services (Service provides the NETBIOS name query solution of the Networks on the Network)
• Configure the WPAD entries in DNS to support Autodiscovery and Autoconfiguration functions for Web Proxy and Firewall clients. Very convenient for ISA Clients (Web and Firewall clients) in an organization when they have to bring Computer from a Network (with an ISA Server) to another Network (with another ISA Server) and still automatically detect and work with Web Proxy Service and Firewall Service on this ISA Server.
• Install Microsoft DNS server on Perimeter Network server (The Network contains the Server provided online for external Clients, behind the Firewall, but also separate from LAN)
• Install ISA Server 2004 Firewall software
• Back up and restore ISA Server 2004 Firewall configuration information
• Use the ISA Server 2004 model (ISA Server 2004 Network Templates) to configure the Firewall
• Configure ISA Server 2004 clients types
• Create access policies on ISA Server 2004 Firewall
• Publish Web Server on a Perimeter Network
• Using the ISA Server 2004 Firewall acts as a Spam filtering SMTP relay (e-mails relay station, with the function of preventing Spam mails)
• Publish Microsoft Exchange Server services (Microsoft Mail and collaboration system, similar to IBM Lotus Notes)
• Configure ISA Server 2004 Firewall to act as a VPN server
• Create a site to site VPN connection between two Networks
Before implementing ISA Server 2004 Firewall configuration, be aware: This is a system to prevent attacks from the Internet and a Firewall with error configuration will facilitate Network intrusion. For these reasons, the most important thing that Security Administrators care about is How to configure the Firewall to ensure the safety of Internet access.
With its default configuration ISA Server 2004 prevents all incoming and outgoing traffic through the Firewall.
Obviously this is the most active and secure configuration that Admin can be assured from the start when operating ISA Server. And then to meet the legal requirements of accessing various Internet services (eg web, mail, chat, download, online games, etc.), the Security Admin will configure it to have ISA Server 2004 available. can meet the requirements allowed above.
The Securty Admin is always recommended: Create tests for configuring ISA Server 2004 in the Lab, before bringing these configurations into practice. We will be guided to configure the ISA Server 2004 Firewall properly and correctly through the ISA Server 2004 working interface. There may be mistakes in implementing the Lab, but the Admin is not worried because Make sure attackers can't take advantage of these vulnerabilities (unless the Lab Network is connected to the Internet .). On the Lab, the most important thing is to correctly understand the parameters configured, allow the offense and the Admin to draw the experience from these mistakes.
LAB instructs to configure ISA Server 2004 Firewall
We will use a Network Lab to describe the capabilities and features of ISA Server 2004. Administrators in practice should build a Test Lab similar to the model shown below (all parameters used). use). If the Admin Security does not have enough real devices like this Test Lab, it is possible to use the simulation model, from Virtual Software like
Microsoft's Virtual PC software (or VMWare) to create a virtual Lab model.
In this section, we will consider:
• How to configure Network for ISA Server 2004
• Install Windows Server 2003, and then upgrade (dcpromo) this Computer to a Domain controller (Domain's full control server)
• Install Exchange Server 2003 on this Domain controller and configure it as an Outlook
Web Access Site uses basic authentication (Basic authentication)
Network Diagram deploying ISA Server 2004
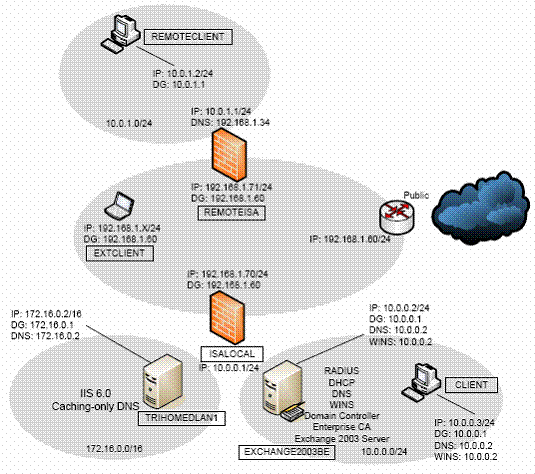
Model Network Lab - 7Computers.
However, Network Lab does not require all 7 Computers to run at the same time
This makes it easy for labs, especially virtual labs.
The Network model of this Organization has a Local Network ( Local Area Network LAN) and a Remote Network . Each Network has an ISA Server 2004 front panel that acts as a Firewall. All Computers on the Local Network are members of Domain MSFirewall.org , and this domain includes the ISA Server 2004 Firewall computer as well. All remaining Computers are not members of this Domain.
In the Network, Network Card (External interfaces) lab of ISA Server 2004 Firewalls have a connection that allows Internet access. Administrators should create the same configuration parameters to test the actual Internet connections from the client side after ISA Server 2004 Firewalls.
If we use the emulator, please note that we must set-up to 3 Virtual Networks on Test Lab. These are the Vitual Networks: The Domain Controller is located on the Internal Network , TRIHOMELAN1 Computer is on the third Perimeter Network and REMOTECLIENT virtual Network.
Pay attention to Virtual Lab : It is certain that on these Virtual Networks, computers are arranged on different Virtual Switches, to prevent information streaming Ethernet broadcast traffic, which can cause results. unwanted on virtual Lab .
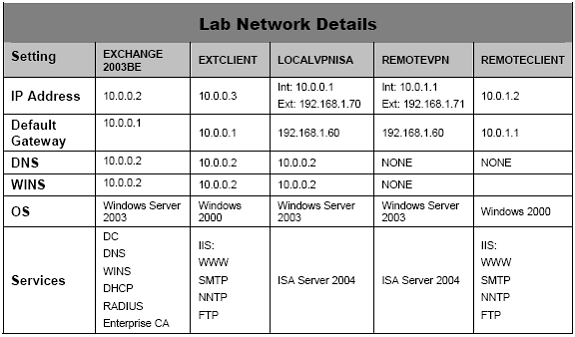
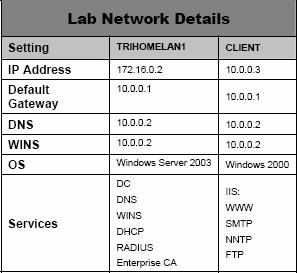
Install and configure the Domain Controller on the Internal Network
A Computer is different from the ISA Server 2004 Firewall computer, which has the power to administer the entire Domain that is Domain Controller. Microsoft built the Domain model under the control of the Active Directory Service and Domain Controller as a tool to control that Domain. (manage all Clients and Servers providing Services in the Domain such as Web, Mail, Database server and including Servers)
In this lab we will configure a Windows Server 2003 domain controller, and deploy services such as DNS, WINS, DHCP, RADIUS, Microsoft Exchange Server 2003 on this domain controller itself.
Stages of progress:
• Install Windows Server 2003
• Install and configure DNS service
• Upgrade this Computer to Domain controller
Install Windows Server 2003
Follow these steps on Computer to act as Domain Controller
1. Insert the installation CD into the CD-ROM, restart Computer. Allow booting from CD
2. Windows setup program starts to load the Files for the installation. Press Enter when the Welcome to Setup image appears
3. Read the License terms on the Windows Licensing Agreement , use the PAGE DOWN key to view it all, then press F8 to agree to the terms
4. On Windows Server 2003, Standard Edition Setup appears the screen to create logical partitions (Partition) on the hard disk, first creating the Partition for operating system installation. In this Test Lab, the entire hard disk will only make one partition. Press ENTER.
5. On Windows Server 2003, Standard Edition Setup , select Format the partition using the NTFS file system Press ENTER.
6. Windows Setup program proceeds to format the hard disk, will wait a few minutes for this process to complete
7. Computer will restart itself when the File copy process to the hard disk is completed
8. Computer will restart in graphic interface mode. Click Next on the Regional and Language Options page
9. On the Personalize Your Software page, enter your Name and Organization
For example:
Name : Nis.com.vn
Organization: Network Information Security Vietnam
10. On the Product Key page enter the 25 digits of the Product Key you have and click Next.
11. On the Licensing Modes page, select the correct option that is applied to the Windows version
Server 2003 that you installed. If installing License in per server licensing mode, include the number of connections that you have licensed. Click Next .
12. On the Computer Name and Administrator Password page, enter the name of Computer in the Computer Name text box. Following the steps in building this Test Lab, the Domain controller / Exchange Server on the same Server and named EXCHANGE2003BE , this name is filled in the Computer Name text box. Enter the Administrator password and confirm the password in Confirm password (remember the administrator password carefully, otherwise you cannot log on to the Server for the next operation). Click Next.
13. On the Date and Time Settings page, set the correct Vietnam Date, Time and Time Zone (if you are in Vietnam). Click Next .
14. On the Networking Settings page, select Custom settings option.
15. On the Network Components page , select Internet Protocol ( TCP / IP) entry in Components and click Properties .
16. In the Internet Protocol ( TCP / IP) Properties dialog box, set the following parameters:
IP address: 10.0.0.2.
Subnet mask: 255.255.255.0.
Default gateway: 10.0.0.1 ( note Default Gateway 10.0.0.1 is also the IP address of Internal Card on the Server).
Preferred DNS server: 10.0.0.2.
17. Click Advanced on the Internet Protocol ( TCP / IP) Properties dialog box. In the Advanced TCP / IP Settings dialog box, click the WINS tab. On the WINS tab, click Add. In the TCP / IP WINS Server dialog box, enter 10.0.0.2 and click Add.
18. Click OK in the Advanced TCP / IP Settings dialog box.
19. Click OK in the Internet Protocol ( TCP / IP) Properties dialog box.
20. Click Next on the Networking Components page.
21. Accept the default Network environment option as Workgroup (we will create the following Domain environment, make it a Domain controller and also a member of Domain (a member server, because this Server also installs Add more Server Service besides Active Directory Service. .Click Next .
22. The installation process continues and when Finish, C omputer will restart automatically
23. Log-on for the first time on Windows Server 2003 uses the password we created for the Administrator account during Setup.
24. First appearing on the screen is the Manage Your Server page , you should check the Don't display this page at logon checkbox and close the Window window.
Installing and configuring DNS
The next step is to install the Domain Naming System (DNS) server on this Computer itself ( EXCHANGE2003BE ). This is necessary because Active Directory Service operates on a Domain Controller, controlling the entire Domain requires DNS server service for querying the name -hostname, registering records (A, PTR, SRV records, etc.). ). We will install the DNS server and then upgrade this Computer role to a Domain Controller, and this DNS server will serve the entire Domain.
Perform the following steps to install DNS server:
1. Click Start, Control Panel . Click Add or Remove Programs.
2. In Add or Remove Programs , click Add / Remove Windows Components
3. In Windows Components , look at the Components list and click the Networking Services entry. Click Details .
4. Check the Domain Name System (DNS) checkbox and click OK.
5. Click Next in Windows Components .
6. Click Finish on the Completing the Windows Components Wizard .
7. Close Add or Remove Programs
The DNS server is installed, Admin needs to include specific DNS parameters for the name query operation, specifically creating two Forward and Reverse lookup zones . Perform the following steps to configure DNS server:
1. Click Start and then click Administrative Tools . Click DNS
2. In the working table of DNS (DNS console), expand server name ( EXCHANGE2003BE ), then click on Reverse Lookup Zones . Right click on Reverse Lookup Zones and click New Zone.
3. Click Next on Welcome to the New Zone Wizard.
4. On Zone Type , select Primary zone option and click Next.
5. On the Reverse Lookup Zone Name page, select Network ID option and Enter 10.0.0 in the text box. Click Next.
6. Accept the default selection on the Zone File page, and click Next .
7. On Dynamic Update page, select Allow both nonsecure and secure dynamic updates option. Click Next .
8. Click Finish on the Completing the New Zone Wizard page .
Next we create Forward lookup zone for the Domain that this Computer will be the Domain Controller.
Proceed with the following steps:
1. Right click Forward Lookup Zone and click New Zone.
2. Click Next on the Welcome to the New Zone Wizard page.
3. On the Zone Type page, select Primary zone option and click Next .
4. On the Zone Name page, enter the name of the forward lookup zone in the Zone name text box. In this example, the name of the zone is MSFirewall.org , which matches the name of the Domain that will be created later. Put MSFirewall.org into the text box. Click Next .
5. Accept the default settings on the Zone File page and click Next .
6. On Dynamic Update page, select Allow both nonsecure and secure dynamic updates . Click Next .
7. Click Finish on the Completing the New Zone Wizard page.
8. Expand the Forward Lookup Zones and click on MSFirewall.org zone. Right click on MSFirewall.org and Click New Host (A).
9. In the New Host dialog box, enter EXCHANGE2003BE correctly in Name (uses parent domain name if blank) text box. In the IP address text box, fill in 10.0.0.2. Check the Create associated pointer ( PTR ) record checkbox. Click Add Host . Click OK in the DNS dialog box to notify that (A) Record has been created. Click Done in the New Host text box.
10. Right click on MSFirewall.org to forward lookup zone and click Properties . Click Name Servers tab. Click exchange2003be entry and click Edit .
11. In the Server fully qualified domain name (FQDN ) text box, enter the full name of Domain controller computer is exchange2003be.MSFirewall.org . Click Resolve . Notice that the Server IP address appears in the IP address list . Click OK.
12. Click Apply and then click OK on the MSFirewall.org Properties dialog box.
13. Right click on DNS server name EXCHANGE2003BE , select All Tasks . Click Restart .
14. Close DNS console.
Now this Computer is ready to take on the role of a Domain Controller in Domain MSFirewall.org
Perform the following steps to create the Domain and upgrade this server to the first Domain Controller of the Domain (Primary Domain Controller).
Install Primary Domain Controller
1. Click Start and click Run .
2. In the Run dialog box, type dcpromo in the Open text box and click OK.
3. Click Next on the Welcome to the Active Directory Installation Wizard page.
4. Click Next on the Operating System Compatibility page.
5. On the Domain Controller Type page, select Domain controller for a new domain
option and click Next .
6 On the Create New Domain page, select Domain in a new forest option and click Next .
7. On the New Domain Name page, enter the full name of the MSFirewall.org Domain (Full DNS name) text box and click Next .
8. On the NetBIOS Domain Name page (NetBIOS name of the Domain to support Windows OS- like the old Windows NT and WINDOWS 9x series, when these clients want to transact with the Domain), accept the default NetBIOS name
In this example is MSFIREWALL . Click Next .
9. Accept the default settings on Database and Log Folders page and click Next .
10. On the Shared System Volume page, accept the default storage location and click Next .
11. On the DNS Registration Diagnostics page, select I will correct the problem later
by configuring DNS manually (Advanced). Click Next .
12. On the Permissions page, select Permissions compatible only with Windows
2000 or Windows Server 2003 operating system option. Click Next .
13. In Directory Services Restore Mode Administrator Password page (recovery mode for Domain Controller when this DC is having problems, When DC offline, enter this troubleshoot mode with 1 Restart Computer, select F8), fill in Restore Mode Password and then Confirm password . (Administrators should not confuse passwords in this mode with Domain Administrator Password, control the operation of DCs or Domains). Click Next .
14. On the Summary page, click Next .
15. Now it is time for Computer to need Restart so that the parameters have just installed Active
16. Click Finish on the Completing the Active Directory Installation Wizard page, completing the installation.
17. Click Restart Now on the Active Directory Installation Wizard page.
18. Log-on to the Domain Controller using Administrator account after Restart.
Installing and configuring Microsoft Exchange on the Domain Controller
Computer is ready for Microsoft Exchange installation. In this section we will take the following steps:
• Installing IIS World Wide Web Services, SMTP and NNTP services
• Install Microsoft Exchange Server 2003
• Configure Outlook Web Access WebSite
Follow these steps to install World Wide Web, SMTP and NNTP services :
1. Click Start , select Control Panel . Click Add or Remove Programs .
2. In Add or Remove Programs , click Add / Remove Windows Components
3. On the Windows Components page, select Application Server entry in the Components page. Click Details .
4. In the Application Server dialog box, check ASP. NET checkbox. Select Internet Information Services (IIS) entry and click Details.
5. In the Internet Information Services (IIS) dialog box, check NNTP Service checkbox. Check next SMTP Service checkbox. Click OK.
6. Click OK in the Application Server dialog box.
7. Click Next on the Windows Components page.
8. Click OK to Insert Disk dialog box.
9. In Files Needed dialog box, insert the path to the I386 Folder on the Windows Server 2003 installation CD in the copy file from the text box. Click OK.
10. Click Finish on the Completing the Windows Components Wizard page.
11. Close Add or Remove Programs .
Follow the steps below to install Microsoft Exchange :
1. Insert the Exchange Server 2003 CD into the CD-ROM, on the autorun page, click the Exchange Deployment Tools link under the Deployment heading .
2. On Welcome to the Exchange Server Deployment Tools page, click Deploy
the first Exchange 2003 server link.
3. On Deploy the First Exchange 2003 Server page, click New Exchange 2003
Tập tin liên kết
4. On the New Exchange 2003 Installation page, scroll down to the bottom of the page. Click Run Setup now link.
5. On Welcome to the Microsoft Exchange Installation Wizard page, click Next .
6. On the License Agreement page, select the I agree option and click Next .
7. Accept the default settings on the Component Selection page and click Next .
8. Chọn Create a New Exchange Organization option trên Installation Type page
và click Next .
9. Chấp nhận tên mặc định trong Organization Name text box trên Organization Name
page, và click Next .
10. Trên Licensing Agreement page, chọn I agree that I have read and will be
bound by the license agreement for this product và click Next .
11. Trên Installation Summary page, click Next .
12. Trong Microsoft Exchange Installation Wizard dialog box, click OK.
13. Click Finish trên on the Completing the Microsoft Exchange Wizard page khi cài đặt hoàn thành.
14. Đóng tất cả cửa sổ đang open.
Exchange Server đã được cài đặt và giờ đây Admin có thể tạo các mailboxes cho Users . Bước kế tiếp là cấu hình Outlook Web Access site và chỉ dùng phương thức xác thực duy nhất là Basic Authentication . Đối với các quản trị Mail Server thì đây là một cấu hình quan trọng (nhưng tất nhiên không bắt buộc) khi muốn cho phép truy cập từ xa (remote access) vào OWA site. Sau đó, chúng ta sẽ yêu cầu một Website Certificate (Chứng từ số Website) cho OWA site và publish OWA site dùng quy tắc Web Publishing Rule trênISA Server , thông qua rule này, sẽ cho phép remote users truy cập vào OWA site.
Tiến hành các bước sau để cấu hình OWA site dùng phương thức xác thực duy nhất Basic authentication:
1. Click Start , chọn Administrative Tools . Click Internet Information Services (IIS)
Manager .
2. Trong Internet Information Services (IIS) Manager console, mở rộng server name , mở rộng WebSites node
Và mở Default Web Site .
3. Click trên Public node và sau đó right click. Click Properties .
4. Trong Public Properties dialog box, click Directory Security tab.
5. Trên Directory Security tab, click Edit trong khung Authentication and access control .
6. Trong Authentication Methods dialog box, đảm bảo không check vào (remove) Integrated
Windows authentication checkbox. Click OK.
7. Click Apply và click OK.
8. Click trên Exchange node và right click. Click Properties.
9. Trên Exchange Properties dialog box, click Directory Security tab.
10. Trên Directory Security tab, click Edit trong Authentication and access control
11. Trong Authentication Methods dialog box, đảm bảo không check vào (remove) Integrated
Windows authentication checkbox. Click OK.
12. Click Apply , click OK trong Exchange Properties dialog box.
13. Click trên ExchWeb node,sau đó right click. Click Properties .
14. Trong ExchWeb Properties dialog box, click Directory Security tab.
15. Trên Directory Security tab, click Edit trong khung Authentication and access control
16. Trong Authentication Methods dialog box, không check (remove) vào Enable
anonymous access checkbox. Sau đó check vào Basic authentication (chú ý dùng phương thức xác thực này, password được gửi đi dưới dạng clear text) checkbox. Click Yes trong IIS Manager dialog box và Admin nhận được thông báo rằng
password được gửi đi hoàn toàn không mã hóa (clear). Trong Default domain text box, đưa vào tên Internal Network domain , chính là MSFIREWALL . Click OK.
17. Click Apply trong ExchWeb Properties dialog box. Click OK trong Inheritance
Overrides dialog box. Click OK trong ExchWeb Properties dialog box.
18. Right click Default Web Site và click Stop . Right click lại Default Web Site và click Start .
Kết luận :
Trong sách hướng dẫn cấu hình ISA Server 2004 này chúng ta đã thảo luận những mục tiêu và những phương thức, để có thể nắm bắt triển khai và cấu hình ISA sao cho hiệu quả nhất. Sách hướng dẫn cũng cung cấp cho các bạn phương pháp giải quyết vấn đề theo từng bước cụ thể. Chương một này tập trung vào việc xây dựng một cơ sở hạ tầng Network (Network Infrastructure) theo mô hình Microsoft Active Directory Domain trên máy chủ Winndows server 2003 Domain Controller, và triển khai các Service khác liên quan đến hạ tầng Network như WINS, DNS, và các Service gia tăng như Web, Mail. Chương kế tiếp trình bày cách thức cài đặt một Microsoft Certificate Services trên Domain Controller Computer .
(Hết chương 1 mời các bạn tiếp tục theo dõi chương 2 sẽ được phát hành trong vài ngày tới)
Ho Viet Ha Owner
Network Information Security Vietnam, Inc.
http://nis.com.vn
Email: networksecurity@nis.com.vn
You should read it
- Installing and configuring the 2004 ISA Server Firewall - Chapter 2 Installing Certificate Services
- Turn on / off concurrent connections to both Non-domain network and Domain on Windows 10
- How to Install, Configure, and Test Certificate Services in a Windows Server 2012 R2 Domain
- How to Configure CAWE in a Windows Server 2012 R2 Domain
- Install Windows Server 2003 and create a backup server
- The best top 10 Public DNS Server you should know now
 Installing and configuring the 2004 ISA Server Firewall - Chapter 2 Installing Certificate Services
Installing and configuring the 2004 ISA Server Firewall - Chapter 2 Installing Certificate Services Installing and configuring the 2004 ISA Server Firewall - Chapter 3
Installing and configuring the 2004 ISA Server Firewall - Chapter 3 Installing and configuring the 2004 ISA Server Firewall - Chapter 4
Installing and configuring the 2004 ISA Server Firewall - Chapter 4 Security with Online Banking
Security with Online Banking 7 categories to prevent denial of service attacks
7 categories to prevent denial of service attacks Nguyen Thanh Cong's Confidence (DanTruongX) And Some Methods to Prevent Denial of Service from xFlash
Nguyen Thanh Cong's Confidence (DanTruongX) And Some Methods to Prevent Denial of Service from xFlash