Deploy Domain System On Windows Server 2003 Active Directory
System Model On Windows Server 2000/2003

I - Build Windows Server 2003 Active Directory And Create Objects By Command Line
Windows Server 2003 is the most complete network operating system available today, we can use Windows Server 2003 to deploy user and resource management domain systems for a company or build powerful Web Servers, organize File Server to store data, provide services for users .
If Windows Server 2003 can be considered as a good administrator of the network system, the Active Directory is its heart, almost all activities taking place on the system are controlled and controlled by Active. Directory.From Windows NT4.0 and later, Microsoft developed the Active Directory system used to store domain data such as user, computer, and group objects, providing search and control services (directory services). Access control, authorization, and especially authentication services built on the Keberos protocol support single sign-on mechanisms, allowing users to only authenticate once when logging into the domain and can access all shared system resources and services with valid permissions.
With its services and utilities, Active Directory mitigates management and improves operational efficiency, tasks that are almost impossible to implement on a distributed, peer-to-peer network. Now we can easily proceed through a centralized management model such as providing general policies for the entire system, but at the same time can delegate administration to divide management capabilities in one large environment.
Main Components of Active Directory System
User : are user accounts, when installing Active Directory, there will be some built-in accounts created as Administrator who have full system administration rights, backup operator is a group and users can backup and restore the system's data without the need for valid permissions on these data.However, for employees in an organization to use resources and log in to the domain, the administrator needs to create valid accounts, and allocate them to users.Users will use the accounts provided by the administrator to log-in and domain.And access data on file server or other services .
Group : is a collection of users with common properties, for example, a sales department employee has access to the sales folder on the file server or we want the company's employees to have the right to print For laser printers, we should create the printing group and assign the print permissions on the laser printer and then add all the company employees to this printing group instead of assigning printing rights to each individual user which will be ineffective (you need to pay attention to using the Domain User group for general operations, by default all created users belong to this group).
OU (organization unit): are organizational units, when designing a domain, we investigate how many systems there are organizations such as how many departments and divisions.Based on the results of this survey, the OU will be created corresponding to the function. The position of the Sales Department will have a Sales OU and this group will contain group sales, group sales will include all members of the sale department. , and these users are also placed in the Sales OU along with group sales.Thus, we need to distinguish clearly sales and Sales OU groups, between them there are basic differences that OU is used for policy management as we want all employees of sales department in the environment. If you are actually installing MS OfficeXP automatically or updating any patches when you log in, then we must interact through the OU.But obviously we cannot manage the access permissions of these users with the OU, so we need to create groups and assign permissions through these groups.Those are the most fundamental differences that we need to distinguish.
The above are the 3 basic objects of the active directory system, and there are other components such as group plicy, site, trusting, global catalog, fsmo.will be presented in the following sections.
Before embarking on building a domain system for your organization, some considerations we need to consider are:
- Need to have at least 2 domain controlers as Primary (PDC) and the other one is Backup (BDC) to meet load balancing and faultolerant function , if the system only has a single controler domain, it must backup the system state data The Active Directory carefully follows the baseline so that it can recover when a problem occurs or migrate to another computer when the PDC is unexpectedly damaged.
- Active Directory system uses DNS for the process of interpreting services and their members, so it is necessary to have a valid DNS for Active Directory to work correctly, what is the Domain name? Active directory installation can choose to install DNS service integration, in case the DNS server is available, the address of this service must be declared in the Prefered DNS section and the domain name is the name of the organization such as tcdescon.com , security365.org .
- It is necessary to examine how many members (users) correspond to the number of accounts created in the Acitve Directory, how many departments and departments to create corresponding OUs and Groups, plus we It is important to consider the usage rights of objects, responsiveness, and so on, to give a full outline of your Domain Controller system.
To do this lab, computers with the TCP / IP configuration are shown below, in which DC1 is a Primer Domain Controller with DC2 Backup System (Secondary Domain Controller) all using Windows Server 2003. Client1 can use Windows XP or Windows 2000.
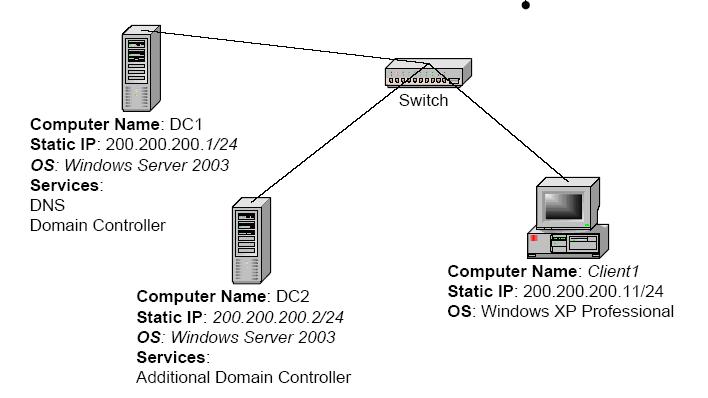
System Domain Controler And IP Address (Click on image to enlarge)
1- Perform automatic installation of Active Directory on DC1 by the Unattend method
To upgrade a Windows Server 2003 Standalone to a Domain Controller, we use the dcpromo command and then provide the full domain name, role and installation location. In this section, please log-in to DC1 using Administrator and create the file as shown below, replace the domain security365 name with your domain name as well as the corresponding Password or SafeModeAdminPassword information, you can choose to install DNS at the same time by specifying AutoConfigDNS = Yes, if If you want the system to reboot after installation, set the value of RebootOnSuccess = Yes
[DCInstall]
RebootOnSuccess = No
DatabasePath =% SYSTEMROOT% NTDS
LogPath =% SYSTEMROOT% NTDS
SysVolPath =% SYSTEMROOT% Sysvol
UserName = administrator
Password = Password
ReplicaorNewDomain = Domain
TreeOrChild = Tree
CreateOrJoin = Create
NewDomainDNSName = security365.org
DNSOnNetwork = No
DomainNetBiosName = SECURITY365
AllowAnonymousAccess = No
AutoConfigDNS = Yes
SiteName = Default-First-Site-Name
SafeModeAdminPassword = netmanager
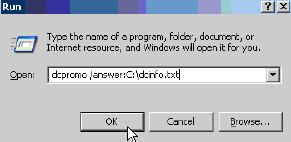
Save the file in C: with the name dcinfo.txt
Then run the command dcpromo /answer:C:dcinfo.txt
Restart the system when the installation process is complete, next we need to create user accounts with the corresponding Group and OU according to departments as shown below based on the actual model of the company. 2 CA and NC branches, each branch has Marketing, Accountign and Sales departments.
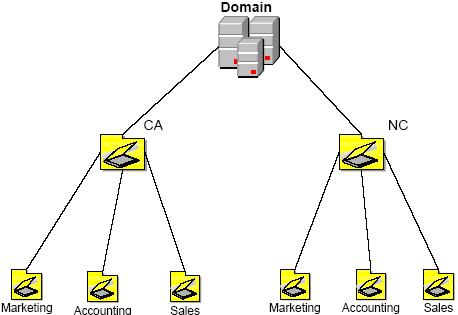
2- Create OU structure with dsadd ou:
There are many ways to create objects on Active Directory such as OU, Group, User.You can use the Active Directory Users and Computers console graphical interface then right-click on the Domain Name (eg security365.com) and select the corresponding actions.Here we use a less common method based on the command line, which is very convenient when you want to build the system automatically.
To create a new OU, use the dsadd ou command line:
Dsadd ou 'OU = NC, DC = security365, DC = com'
Dsadd ou 'OU = CA, DC = security365, DC = com'
Dsadd ou 'OU = Marketing, OU = NC, DC = security365, DC = com'
Dsadd ou 'OU = Accounting, OU = NC, DC = security365, DC = com'
Dsadd ou 'OU = Sales, OU = NC, DC = security365, DC = com'
Dsadd ou 'OU = Marketing, OU = CA, DC = security365, DC = com'
Dsadd ou 'OU = Accounting, OU = CA, DC = security365, DC = com'
Dsadd ou 'OU = Sales, OU = CA, DC = security365, DC = com'
You can use the bat file to perform the process automatically, with OU being the name of the created OU, DC is the name of the domain that should be created sequentially.
3. Create User With user account:
We can create user accounts with user accounts , for example, will create an account for Nguyen Tran Duy Vinh of Sales department:
- login username vinhndt, password 123qwe login! @ #
- belongs to the Sales OU set
- first name is nguyen tran duy
- last name is honor
- upn name is ntdvinh@security365.com
- so that an account can be used immediately, set –disable no
User account 'CN = vinhndt, OU = Sales, OU = CA, DC = security365, DC = com' –upn
vinhndt@security365.com –fn nguyen tran duy –ln vinh –pwd 123qwe! @ # –disabled no
3. Create Group with dsadd group :
Users in each department often have common characteristics such as access to resources shared by the department, ability to use the printer . So create user groups (Group) then add users to .We can do this with the dsadd group command line.The following example will create a gourp named as Consultants (CN) in the Marketing OU of the Security365 domain. The code, group type is security and group scope is global.
Dsadd group 'CN = Consultants, OU = Marketing, OU = CA, DC = security365, DC = com'
–Secgrp yes –scope g
Note : There are two types of groups in active directory which are security and distribution.Most groups we create and use the security goup category.Distribution group is only used for the operation of applications such as Exchange Server, and you cannot assign access to this group type.In addition, the groups are divided into 3 types of scope groups: Global, Universal and Local.With Local Group members can only access the resources on the internal domain.When the system has multiple domains, so that users can access the resources in other domains, they must be members of Global or Universal Group.
4.Add User to Group With Dsmod:
To Add User Nguyen Tran Cat Vinh is a member of group Consultant in OU Marketing (which is the sub-OU of CA) for domain Security365.Com we use the following command:
Dsmod group 'CN = Consultants, OU = Marketing, OU = CA, DC = security365, DC = com' -
addmbr 'CN = vinhntc, OU = Marketing, OU = CA, DC = security365, DC = com'
In the case of remote administration or need to create multiple objects at the same time for the system it is best to use the command line utilities.The way to administer Active Directory through graphical interfaces such as Active Directory Users and Computer can be found atwww.microsoft.com, all questions are sent to the HelpDesk section atwww.security365.org, the Company. An Absolute Solution.
II - Join Client1 Disable Domain Computer
After installing and configuring the Active Directory system, we need to join the users to the domain so we can manage and grant access and use of resources to users.Please log in to Client1 as Administrator and right-click My Computer and select Properties:
On the Computer (Network Identification) tab, click Change or Properties depending on the Client1 operating system used is Windows XP or Windows 2000. Next, enter the following information:
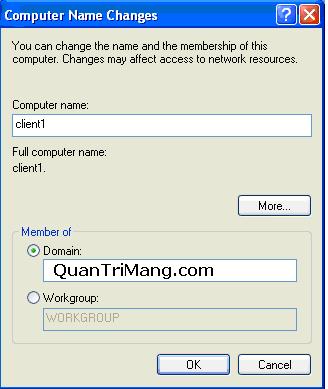
Click OK, a dialog box asking for Username & Password information will be displayed, enter the valid account as Administrator and click OK to complete the domain join process.
III - Installation Secondary Domain Controler:
For large network systems with multiple users, we should deploy additional secondary domain controllers (also known as Backup Domain Controler-BDC) to enhance the responsiveness of user access requirements and when the primary domain controler In the event of problems, the system can still operate normally thanks to this secondary domain controler, in addition to being able to recover Active Directory databases on the PDC.Both Domain Controler systems contain the same domain database as user, group policy, and ou . and when the data on this domain controller changes, it will automatically replicate to the control domain. Again, this process is completely automatic because the KCC service (knowledge consistent checker) of the system takes care of it.However, in special cases you can start replicate immediately.Here are the steps to build secondary domain controllers:
Join the DC2 computer into the domain and log-in with the Administrator account.Open Start -> Run and run the dcpromo command
On the next installation screen we select the Additional domain controller entry for an existing domain and click Next.On the Network Credential window, enter the account Administrator, Password of the domain and select Next:
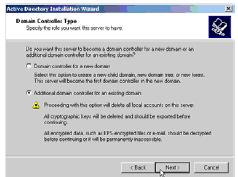
Next the program will ask for the name of the domain that DC2 will be a secondary domain controller (in the additional domain controller box).This name will display automatically if DC2 is a member of the Domain.If you proceed to level up without DC2 domain join, you must enter the full Domain name like security365.com.One thing to keep in mind is to configure the DNS address for the domain in the Prefered DNS section, because most problems and errors when upgrading a secondary domain controller as well as through the Active Directory activity are related to configuration. Incorrect DNS server address image makes server name resolution and services unavailable.
Then accept the default value for the installation location, the database store of the active directory as well as the sysvol folder.If you want to change these parameters after installing, use the NTDSUTIL tool.
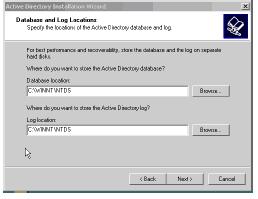
Finally a table summarizing the information of secondary domain controllers is displayed, check the tar again and click Next to proceed with the installation process. Once completed, restart the DC2 system.
So we have completed the active directory system for domain security365.com with a primary and a secondary domain controller, at which point the client computers on the system can join the domain with valid accounts to perform the job. mine.
Author: Indochina Dragon
Email: Indochina@Security365.Org
Security Solutions Company - Web:http://www.security365.org
Share by
Samuel Daniel
Update 25 May 2019
You should read it
- ★ Fix Windows error that cannot connect to domain
- ★ Instructions for installing Active Directory on Windows Server 2008
- ★ How to check which Domain Controller holds the FSMO role in Active Directory
- ★ How to Back Up Active Directory in Windows
- ★ Prevent deleting data in Windows Server 2003 Active Directory