Install 'sirens' for Windows with Predator
With the rapid development of current technology, information security is becoming more important than ever. Imagine if a lot of valuable data on your computer is unfortunate so that outsiders know how dangerous it is.
Therefore, improving information security has never been excessive. Today, we will show you how to create another layer of security next to the security layer available on Windows. With just one USB and Predator software, you can be assured of a 2-tier "fence" layer on your personal computer. Let's see how to do it.
Download Predator for Windows
Specifically, Predator will turn your USB device into an access control device to your computer. When initializing, you just plug the USB into the computer, then enter the password to protect the computer access. If entered incorrectly, the Predator's warning system will start and the computer will sound an alarm.
First, you need to download and install on your computer
You click I Agree to agree to the terms provided by the provider

Next, select the link by clicking Browse

Next, the installation process will take a few minutes

Finally, click Close to finish.
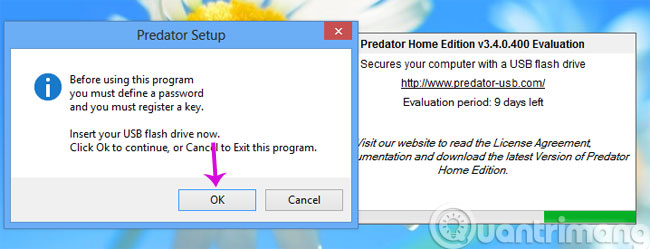
After installation is complete, launch Predator from the icon on the desktop. A message box will appear, now connect the USB you want to set up as "key" to your computer and click OK .
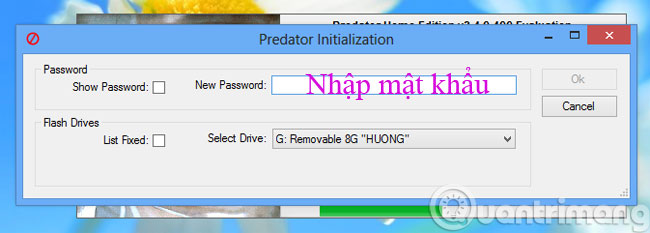
The next dialog box will ask you to set a password for the USB, as well as the character selection of the USB device connecting to the computer.
When everything is done, the Predator icon will appear in the system tray with an eye-catching green color, indicating that the software is in the launch state.

To continue setting up some other configuration options, right-click the Predator icon in the system tray and select Preferences .
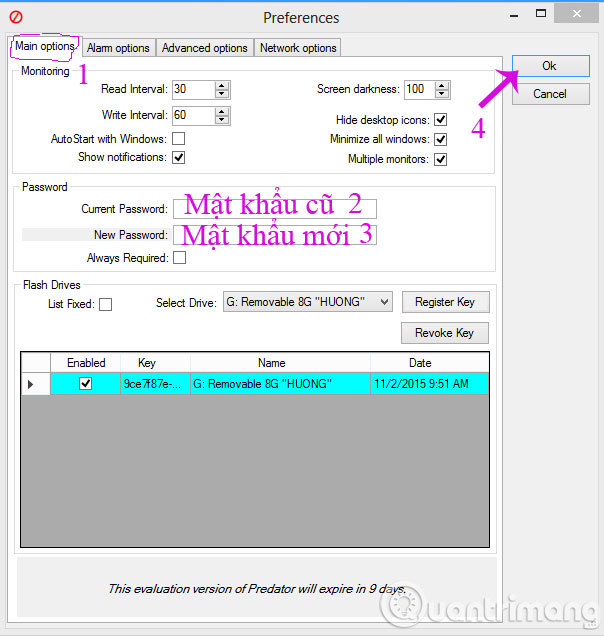
The Preferences window appears, in the Main options tab, you can change the password you previously set for USB, then press OK .
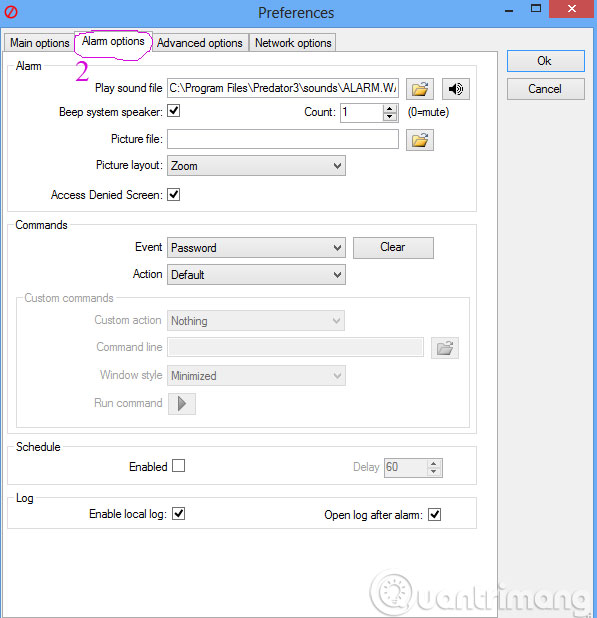
Next, in tab Alarm options will be the option of "alarming" sound unauthorized access, take a screenshot of the webcam screen, manipulate the wrong password, access logs . All can be customized Edit this section.
The other two tabs are network and language settings, so you don't need to care.
This is done for the Predator configuration steps, now when you go out, the computer will automatically lock and Predator will be activated. When someone enters the wrong password more than 3 times, the computer automatically generates an alarm and takes a picture of the crook through the webcam. Pretty awesome?
Predator works well in all Windows versions, and you will be provided with an unlimited 10-day trial before deciding to upgrade to a paid version.
- How to create self-extracting file and set password for compressed file?
- Use WinPatrol to monitor computers
- How to disable / enable Windows Firewall in Windows 7, 8
Good luck!