How to recover data encrypted by WannaCry malicious code
The attack from the WannaCry malware, although it has subsided lately, has been extremely serious for organizations and agencies that have been attacked by computer systems. WannaCry has the ability to 'bypass' all security security firewalls. All data contained in the computer will be completely erased. And to be able to retrieve those important data, we are forced to pay a virtual money.
In this situation, there are many measures to prevent attacks, spread and strengthen the security system to prevent the vulnerabilities that WannaCry uses to invade computers. So what if the computer was attacked by WannaCry and lost most of the data? If the reader is experiencing this situation, you can use the WannaKiwi tool.
The WannaKiwi tool comes from a security researcher at Quarkslab, capable of helping users recover data after being attacked and wiped out by WannaCry.
Note to users , WannaKiwi can run on both Windows XP, Windows 7, Windows Vista, Windows Server 2003, 2008. But the tool can only 'save' data when the computer has not restarted since infection.
Step 1:
First of all, we click on the link below to download the WannaKiwi tool to your computer.
- Download the WannaKiwi tool
Step 2:
After downloading, we proceed to extract the file.

Then, access the folder and extract and run the .exe file to start the Wannakiwi program.
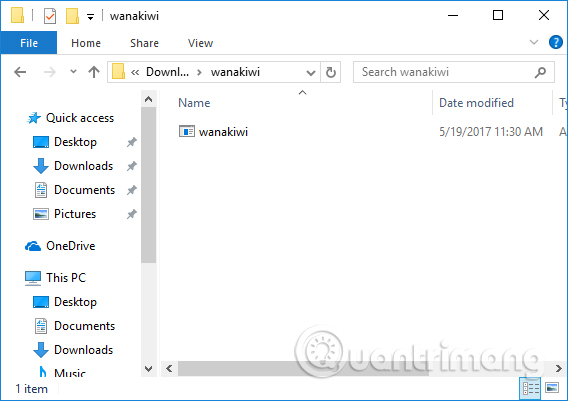
Step 3:
Soon, the tool will scan the entire system to find the 00000000.pky encryption string, and then perform data recovery for the user.
When the WannaCry malware attacks and infects the computer, the wcry.exe process will be created and the process will generate a private RSA key. But WannaCry did not delete the sequence of prime numbers from RAM. So if the computer is infected and has not restarted, these important serial numbers remain intact and are used to decrypt the data that WannaCry has encrypted.
Video restores data infected with WannaCry with Wanakiwi
Thus, taking advantage of the loophole of WannaCry malicious code that Wannakiwi tool has helped users can retrieve all data that was encrypted by this malicious code, deleted from the computer system. However, the computer since infection has not restarted any time Wannakiwi will work. If the computer is turned off and turned on again, it is impossible to use the Wannakiwi tool anymore.
I wish you all success!