Warning with 4 dangerous variants of WannaCry malware
The worldwide spread of WannaCry malware has not shown signs of stopping. This type of malicious code still attacks computer systems of many agencies and organizations around the world. Meanwhile, WannaCry version 2.0 has a stronger attack capability than version 1.0.
Especially now there are many hackers creating more malicious versions based on the original WannaCry malicious code. These versions not only feature features of harmful WannaCry extortion codes, but they appear with different interfaces and languages including Thai and Chinese. Experts have now discovered four variants of WannaCry malware.
- How to handle the emergency WannaCry malicious code from the National Information Security Department
- How to remove / fix ransomware WannaCry
- How to identify WannaCry malicious code from Vietnam Computer Emergency Response Center (VNCERT)
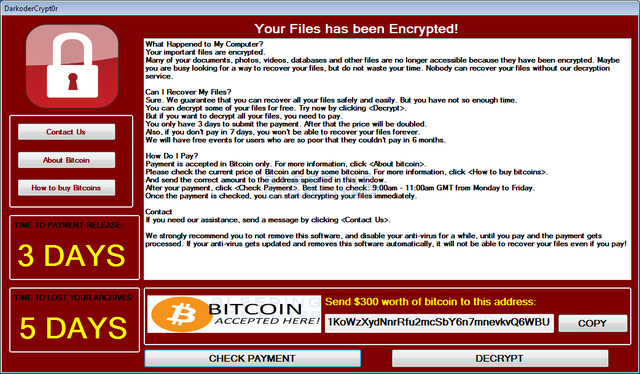
1. DarkoderCrypt0r variant:
Top of the 4 variant versions of WannaCry, the most complete is DarkoderCrypt0r. If you look at the interface of DarkoderCrypt0r it will look similar to WannaCry, in addition to the custom title and bitcoin address. This variant has the ability to encrypt data files, ransom, display the .DARKCRY extension after the data name is locked, and the executable file appears @ DaKryEncryptor @ .exe .
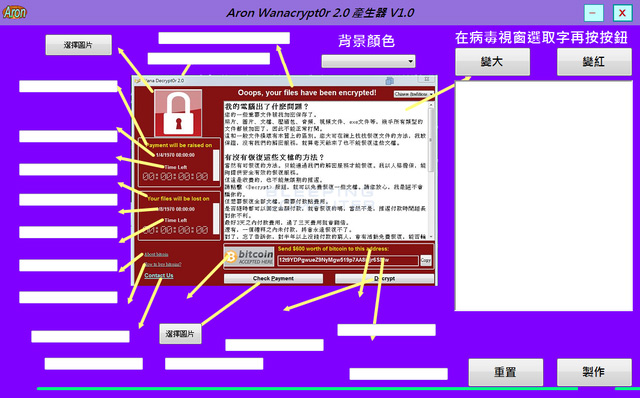
2. Aron WanaCrypt0r 2.0 Generator v1.0:
Aron WanaCrypt0r 2.0 Generator v1.0 is currently being developed by hackers to turn it into a customized version of the malware. This type of variation will create a custom WannaCry lock screen, so that hackers can change the text, image and color content of the notification screen. Interface of this type of variation in Chinese language.
Aron's ability to attack WanaCrypt0r 2.0 Generator v1.0 is pausing at a level that allows hackers to attack computer systems using ransomware.
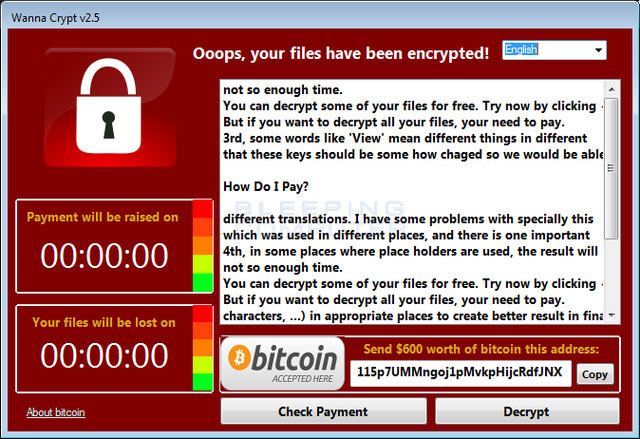
3. Wanna Crypt v2.5 variant:
Like the second variant of the WannaCry malware, Wanna Crypt v2.5 is in development, not yet integrating virtual ransom data locking tools like WannaCry malware. The variant will only display the lock screen when the system is compromised.
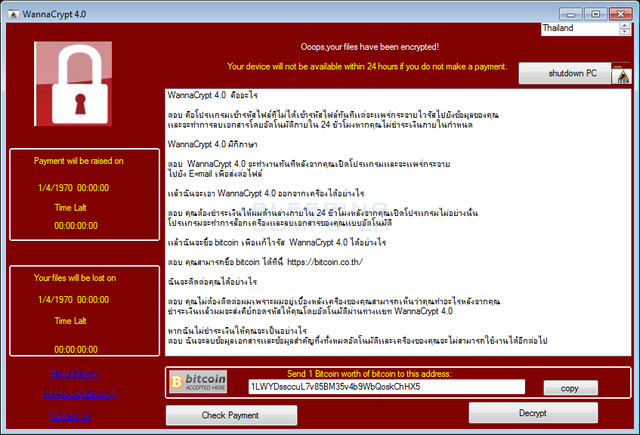
4. WannaCrypt 4.0:
The interface of the WannaCrypt 4.0 variant in Thai has not yet been able to encrypt data for ransom, similar to the Wanna Crypt v2.5 variant.
Due to the horrific attack and spreading with the speed of WannaCry malicious code, even variants of this malicious code, users should not activate any strange links or attachments. In addition, regular updates of patches from Microsoft and computer protection software are also ways to prevent intrusion, encrypting the data of today's dangerous global WannaCry malware.
- How to close the port / Port 445 on Windows 2000 / XP / 2003 to Windows 10 to prevent ransomware WannaCry
- Microsoft released an emergency patch to prevent ransomware from attacking
You should read it
- ★ All about WannaCry, Ransomware has been confusing for the past few days
- ★ 2 effective and free ways to check WannaCry
- ★ How to prevent EternalRocks malicious code
- ★ Prevent WannaCry variants by turning off this Windows 10 installation
- ★ A hacker in the United Kingdom found a way to temporarily encrypt the WannaCry malware