How to Protect Windows NTLM Credentials from Zero Day Threats
Windows devices use an older login method called NTLM, which is enabled by default. If malware attacks your system, it can expose your system password to hackers. They can use a variety of Man-in-the-Middle attacks to steal your Windows login credentials. Fortunately, you can protect your Windows NTLM credentials from Zero Day threats with a few simple tweaks to your NTLM settings.
How do Windows NTLM threats steal your passwords?
NTLM (NT LAN Manager) is an older authentication method that is still used on many Windows devices. It works by turning your password into a code (hash) to verify you without sending the password over the network. This method is not secure because if your PC is compromised, your login password will be visible to the attacker.
Recently in April 2025, security researcher Check Point blogged about the disclosure of NTLM hashes through a vulnerability dubbed 'CVE-2025-24054'. According to them, this is an ongoing cyberattack targeting government and corporate users in Poland and Romania. The attackers are using various types of Man-in-the-Middle attacks, including Pass-the-Hash (PtH), Rainbow Table , and Relay Attack . Their main targets are high-level users or administrators.
While NTLM attacks are typically targeted at businesses and governments, home users are also vulnerable. Simply interacting with a malicious file can leak your system password.
Microsoft has released a security patch for CVE-2025-24054. So you should always keep your Windows system up to date to prevent these attacks. There are also a few other things you can do.
1. Disable NTLM authentication via PowerShell
Open PowerShell with admin rights and enter the following command. You will see another question asking if you want to modify the target SMB Client Configuration. For that question, click A .
Set-SMBClientConfiguration -BlockNTLM $true 
Blocking NTLM over SMB won't affect your latest Windows devices. However, if you run into issues with older printers, NAS servers, or other legacy devices, you can always switch back to allowing NTLM over SMB.
Set-SMBClientConfiguration -BlockNTLM $falseServer Message Block (SMB) is used for file sharing and networking. It is one of the most common connections used by PtH, Relay Attacks, and other Man-in-the-Middle attacks. By blocking NTLM over SMB, you are eliminating a key gateway for attackers.
2. Disable the old NTLM protocol in Registry Editor
Many Windows sessions are now stored in 'Kerberos', which is a very secure protocol as it uses ticket-based encrypted authentication. However, there is no need to completely disable NTLM as it has many uses. Instead, we will switch to the more secure NTLMv2 protocol instead of NTLMv1.
You can do this from the Registry Editor. First, back up your registry. Next, open the Registry Editor in admin mode and go to:
ComputerHKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsa 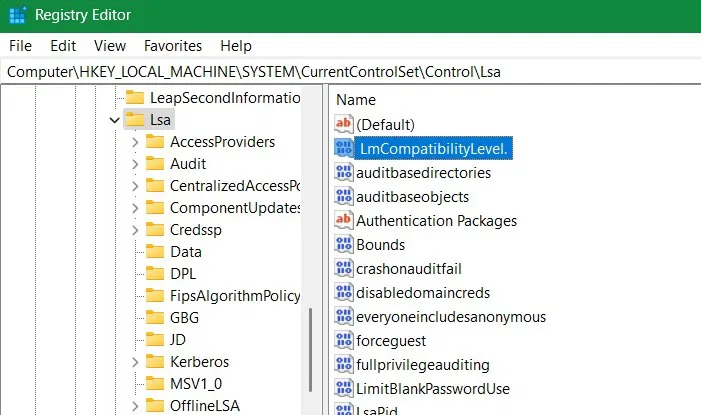
In the "Local Security Authority" (Lsa) registry key, go to the LAN security manager authentication level value, "LmCompatibilityLevel". If it is not there, create a D-WORD (32 bit) in Lsa as shown above.
Double-click "LmCompatibilityLevel" to open it. You'll see "0" as the default value. Set it to "3", "4", or "5" to have your Windows device only send NTLMv2 responses and block all legacy NTLMv1 responses.
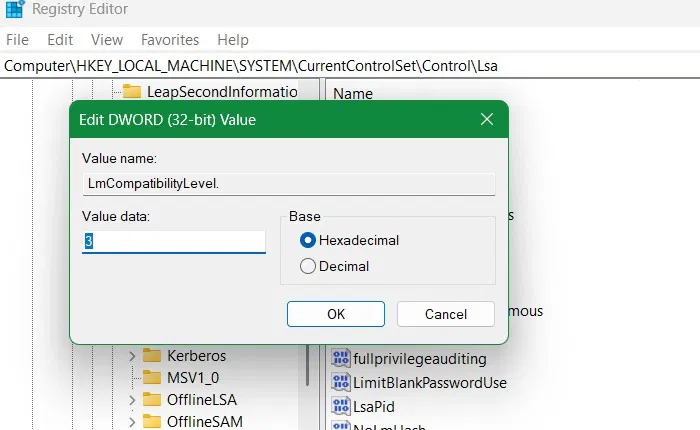
After you make the above changes, go to the path below:
COMPUTERHKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesLanmanWorkstationParameters
Here you will find a D-WORD value called 'RequireSecuritySignature' or 'EnableSecuritySignature'. Its default value should be '1'. If not, change it to '1'. Once you do this, all future SMB connections will require SMB security authentication. This prevents your device credentials from being stolen.
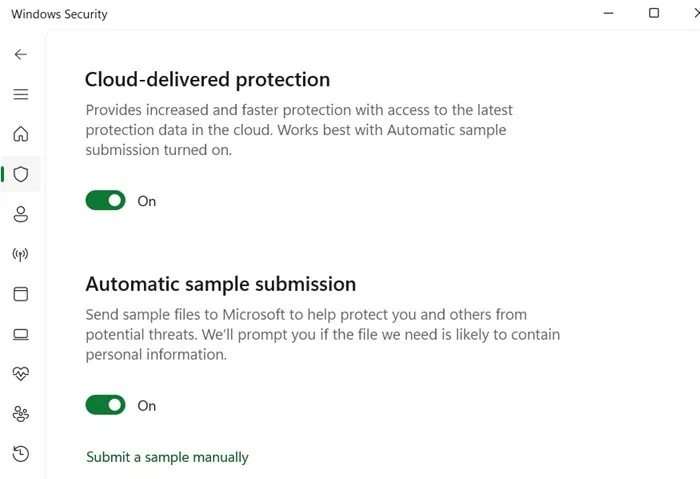
3. Turn on Cloud Protection in Windows Security
The above registry changes are harmless. However, if you don't want to do it, you can protect your device with the new Windows Security feature that helps prevent all kinds of threats like phishing attacks. This feature can be accessed from Virus & threat Protection > Manage settings > Cloud-delivered protection .
4. Other security measures
Microsoft recommends the following additional security mechanisms to avoid becoming a victim of NTLM credential theft:
- Enable multi-factor authentication : You can enhance your password and PIN-based login security with multi-factor authentication mechanisms. Go to Settings > Accounts > Sign-in options . Here, you'll find a variety of options, such as Windows Hello and creating a physical security key using a USB device.
- Avoid clicking suspicious links : NTLM malware often spreads via malicious links. While they may be blocked by Windows Security, why risk fighting these remote exploits ? Check out our detailed guide on how to spot and avoid malicious messages .
You should read it
- ★ How to fix constant 'Enter Network Credentials' message on Windows
- ★ What is PetitPotam Attack? How to overcome PetitPotam attack
- ★ How to share WiFi credentials with QR codes on Android 10
- ★ How to enable Local Security Authority (LSA) protection in Windows 11
- ★ How to customize the Windows 10 PIN code limit