Home computer at any potential risk
Every family has at least one novice computer user. For example, those who are passionate about P2P networks cannot resist 'cunning' download clicks; The commune's husband and wife mistakenly clicked on pop-up ads and suspicious updates; or her cousin returned the laptop full of malware. Now you stand in front of two choices: either become a paranoid stingy with dangerous warnings others consider to be excessive, or set up a smart and popular security prevention system for family members. family with friends how to exploit the Internet safely.
The following four steps can help you make this task easier.
Although it is very desirable that our methods are easy to understand and use, we cannot guarantee completely against all malware. Crime hackers are constantly plotting new plans against the best defense barriers. It is often said that the prevention program "runs after" hackers. However, following these steps can help you reduce the risk for the computer from the family.
Step 1: Create multiple user accounts
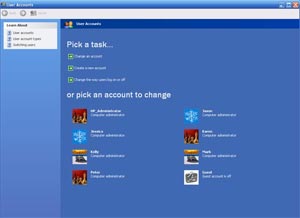
Windows user account control function easily limits privileges for specific users
The first step for many users is to give each member a separate account, especially for family members. Because they are often not very knowledgeable about computer knowledge and network activities, it is necessary to separate the scope of activities for each person to support each other's "consequences". Advanced functionality in creating multi-user accounts is that administrators can limit the ability to install programs, perform system-wide operations for others. That helps prevent guests from executing harmful programs for your computer. To solve the problem effectively, each member should have some intuitive tips such as using a password protection login program, which helps maintain privacy.
In most Windows operating systems, simply click on the Start menu, open Control Panel and select 'User Account'. To add users just click the 'Add' button on the Users tab, enter a name, select a user type with administrative privileges or restrictions.
Make sure the 'login password' component is used. Each member will have a unique username and password to ensure privacy for each person. The nature is required to log back in after a mid-term pause also for security purposes. You can edit the setting of the suspension time to minimize the login frequency.
Step 2: Control the security checklist
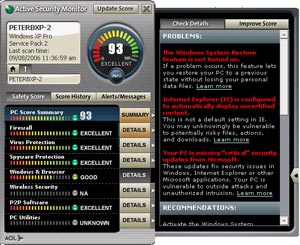
AOL Active Security Monitor with predictable security situations
The saying ' the best protection is to have a good attack plan ' especially true in the field of computer security. Viruses and malware are always trying to get into your network by any means, do not ignore the opportunity no matter how small, especially when you ' lock the main door and open the window '.
The Security Starter Kit provides you with a multi-faceted security program with firewall, virus, spyware and real-time protection. This program is in our 'favorite free security programs' collection. There is also free AOL Acive Security Monitor software that provides predictive scanning with a number of other advanced methods.
If you have enough money, consider upgrading security. You can add one or two commercial versions, providing a number of extension components such as 'on-the-fly' protection mode, advanced spyware removal mode, which is rarely available in free versions. . Trend Micro PC-cillin is quite powerful and easy to use software with many outstanding features and it is a bright candidate for your protection fence.
Step 3: Download browser protection software
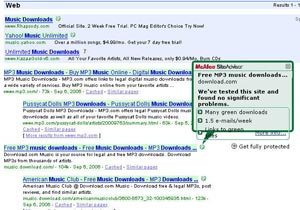
McAfee SiteAdvisor combines color code websites that are racing against Google search pages
User accounts and firewalls can help you avoid a lot of troubles but can't prevent children like your children from clicking unsafe links. If kids know how to surf and search, you can't stop them from downloading free games or music. Depending on the circumstances, you may use the following different measures:
A. Using McAfee SiteAdnisor : Identifying online threats is a way to avoid them. McAfee SiteAdnisor for Internet Explorer and Firefox has 3 levels according to the blue, yellow or red icons on the website to check. These three levels are based on 3 criteria: download quality, number of e-mails sent each week, safety of incoming links. You can view the full explanation by clicking on the SiteAdnisor icon on each specific website, or by browsing the icon located in search sites like Google or Yahoo.
B. Changing browsers : Both Mozilla Firefox and Opera are rated as safer browsers than Internet Explorer. Both have pop-up ad blockers, viruses and spyware. But it's also worth noting that Firefox's extensive user base is now starting to become an attractive target. Because the authors of malware and viruses want to influence a larger number of users. However, these two browsers are still considered safe options. Stopping the use of IE will quickly reduce the number of threatening threats knocking on your door.
C. Using sandbox : Control scope IE is attracting a large number of serious threats, but people often prefer to use this most popular browser. They can use a sandbox like GreenBorder Pro with Safe Files. GreenBorder software works by creating external browser browser protection. Your activities are left in a detached environment that does not signal from regular Net interactions. SafePods quarantines the browser in a similar way and allows users to clean tracks in each session.
D. Use filters : Filtering and monitoring programs such as OnlineSafety Shield and Optnet PC Parental Control Software are primarily set to block issues such as pornographic or gambling websites, or block links URL of some specific websites. Other filters have more ingredients, some are more suitable for children than adults.
Step 4: Popular, popular and popular
Although sometimes family and friends share computers with you, they don't really "try" to poison the machine. But the risk is that they do not have enough knowledge before threats. Steps 1 to 3 can only be applied to you. You have set up user accounts and protection software, but the most important thing now is to help people who share computers.
Help people understand common threats such as malicious malware distribution methods. Dangerous links can be embedded almost anywhere, software attach and download software must be very careful. A simple and quick way to learn is to refer to the recently updated Security Glossary (we will include this version in the next few days). There is also a guide for users to generally identify (or avoid) suspicious websites with 'suspicious Websites'.
If all seems too much for new learners to use computers, you can create a safe checklist on your computer. Must be placed so that anyone who uses the device can know and be alert. Maybe that will help you later thank you so much yourself.
You should read it
- How to protect folders with Secure Folder?
- How to turn on Tamper Protection for Windows Security on Windows 10
- 10 simple ways to protect data and accounts
- Enhance Windows security with Panda Gold Protection
- How to open Windows Security in Windows 10
- Troubleshoot software protection service issues in Windows 10
 Solve the threat from the network
Solve the threat from the network Class-based defense solution for VoIP networks
Class-based defense solution for VoIP networks Protect personal information on 'social networks'
Protect personal information on 'social networks' Five tips for safe online shopping
Five tips for safe online shopping Norton 360 - Comprehensive PC protection
Norton 360 - Comprehensive PC protection Password management problems in IE and Firefox
Password management problems in IE and Firefox