Experience with K7 application - Total Security 11.1
TipsMake.com - The name K7 may be unfamiliar to many users, but in the security software market today, this application has a fairly solid foothold. From 1991 until now, they have focused on building and developing security solutions, helping computer users avoid the common troubles in today's life. In the following article, we'll cover some of the basics as well as the outstanding features of this program, which is K7 Total Security 11.1.
First 'impression':
With a 30-day trial period, the installation capacity is quite light (about 70 MB), does not require users to enter information or other details during the installation, K7 will cause many users to remember. One point to note here is that K7 Total Security cannot 'live' with Malwarebytes in the same computer:
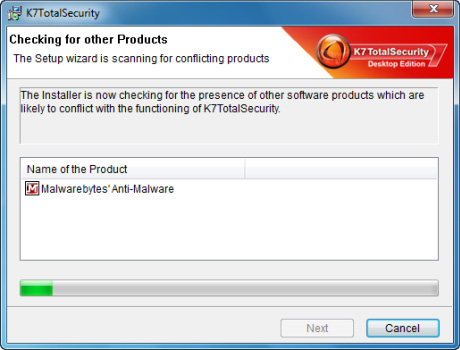
If Malwarebytes is available on the system, K7 will ask the user to uninstall first, then continue the installation process when rebooting.
The installation process is quite simple, you hardly have to adjust any options, just enter your email address and username to activate the trial account. And then there is the process of identifying the system, the network connection protocol, displaying the main console as well as how to protect the system based on the options.
The official work window divided by tabs, the system tray icon is also 'equipped' with some frequently used options such as turning off or turning on some functions, completely disabling some chapters process of the system such as Windows Firewall and Windows Defender .
Options and usage:
The main tabs on K7 main control panel include: Security Center, Tasks, Settings, Tools and Support:

In the Security Center section , the program provides an overview of the current state of the operating system. When you hover over each of the respective components, the system will display the corresponding option to enable or disable the component. Therefore, users do not need to click too much to change options.
If you want to start or schedule the scan by time, check the updated version or work with the file in quarantine - Quarantine . use the Tasks tab. There is also an option to review previous actions, the entire scanning process, vulnerabilities detected, or restore the default configuration - quite useful when users change Change settings too much.
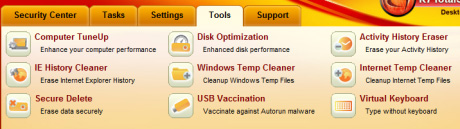
In the Tools tab, you will see several modules that support deleting junk files and optimizing system performance. But some modules, such as Computer TuneUp and Disk Optimization , provide too little detail about what K7 is doing.
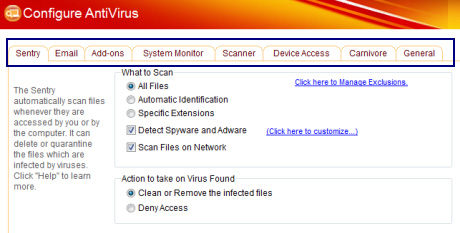
Besides, users can also access and change the settings of each related component from the Security Center or Settings tab . The main control interface of the Antivirus section is also divided into a combination of tabs, including the full range of common options such as default virus scanning, file and folder isolation .:
The settings of the Firewall section are similar, sorted and tabbed, but are easier to see than the Antivirus item. Here, you have the right to or not allow any application to connect to the Internet, adjust or update the network connection method in use .:
In fact, most users feel satisfied with K7's default settings and customizations. For example, when plugging a USB drive (or mobile phone, portable storage device .) into the computer, the program will display a notification window if the device has not been tested:
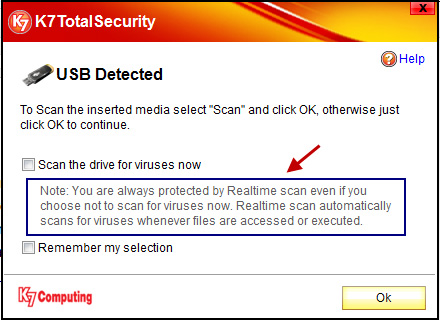
Firewall feature:
This security mode of K7 Total Security is quite 'quiet', but still has all the basic functions. Users can check and monitor which programs are allowed to access the Internet, or when there is an updated / updated version of an application .:
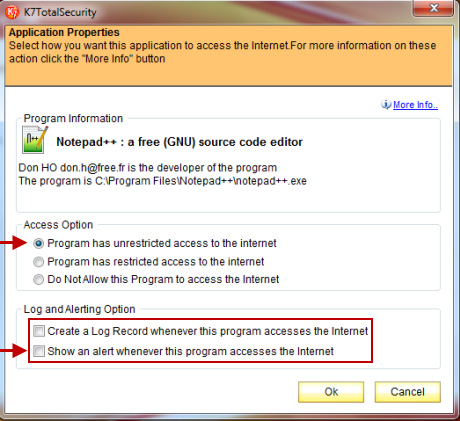
Besides, users can completely create 'exceptions' based on the rules related to the amount of computer traffic, ports and IP address classes:
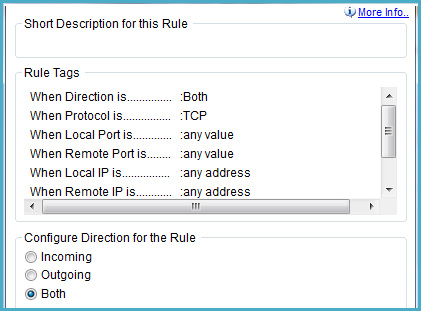
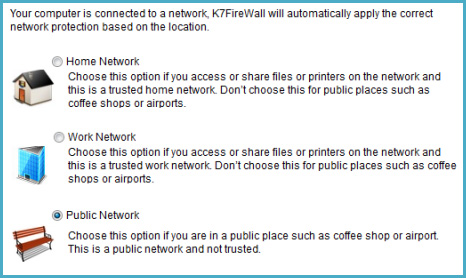
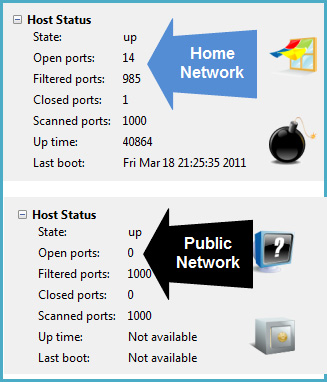
When we tested this Firewall feature, we performed a command to scan the entire remote system to see what signals were returned. The tool applied here is Nmap with Network mode set to Home . As a result, the Firewall detects that 14 Ports are open, and the amount of data back and forth is sufficient to confirm the details related to the operating system, Workgroup name . Then we continue to switch Network into Public before executing the second scan. And the results were unexpected, the number of active Ports dropped to 0, and could not detect any information:
Antivirus and Antispyware features:
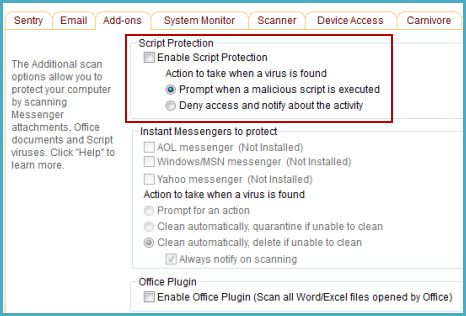
Slightly different from the few options available in the Firewall section, here you can choose the default operation when the program detects vulnerabilities, exceptions and the file management catalog is isolated, next to Enable Enable Script Protection feature , applied to some popular IM programs such as AOL, MSN, Yahoo .:
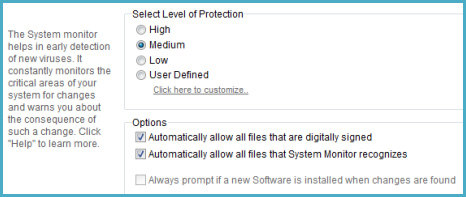
In System Monitor, users can set the security level at will:
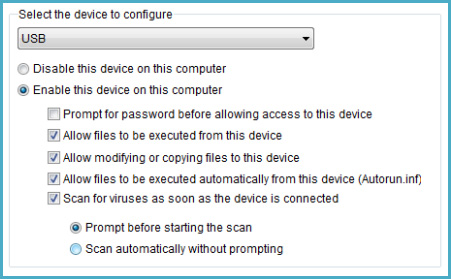
The Device Access tab allows users to set the mode, which applies to external devices such as USB drives, CD / DVD drives . when interacting with the operating system:
Finally, a real test with a few malicious websites, this is the moment to decide whether the K7's security is as safe as the advertisement:
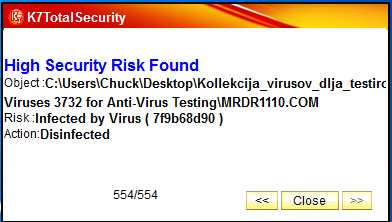
The image above proves that the security of K7 can completely meet the needs of most users. Various customization options, easy configuration and setup, friendly interface, multiple security and system optimization mechanisms . obviously you won't have to consider too much when choosing K7 Total Security 11.1. Good luck!