Execute and troubleshoot certificate deployment issues in ISA Server 2006 - Part 2
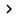 Execute and troubleshoot certificate deployment in ISA Server 2006-Part 1
Execute and troubleshoot certificate deployment in ISA Server 2006-Part 1
In this article, I will show you how to use digital certificates in web chain and reverse publish scripts.
Introduce
We will start with a brief introduction to the types of certificates used in a secure publishing scenario and then introduce the functionality that SAN certificates (SAN = Subject Alternate Name) provide as well as Their differences with classic certificates, such as wildcard certificates.
Types of certificates
There are three commonly used certificate types:
- Normal certificate
- Wildcard certificate
- SAN (Subject Alternate Name) certificate
Normal certificate
A certificate is usually a 'classic' certificate. This type of certificate used for a Fully Qualified Domain Name (FQDN) is also known as a DNS hostname like owa.it-training-grote.de.
Wildcard certificate
Wildcard certificates are often used when a company needs to publish different hostnames with the same domain name. Instead of using many common certificates, we can use this type of certificate. For example, if you buy a wildcard certificate for * .it-training-grote.de, you can use the certificate to publish webservers with it, with the names owa.it-training-grote. de and www.it-training-grote.de.
SAN certificates
SAN (Subject Alternate Name) certificates are also called domain certificates or Unified Communication (UC) certificates. With the help of SAN certificates, it is possible to publish multiple FQDNs with the same or different Top Level Domain name (TLD).
For example:
owa.it-training-grote.de
www.it-training-grote.de
Server01
Server01.exchange.internal
Autodiscover.exchange.internal
Autodiscover.it-training-grote.de
SAN certificates are widely used in publish scenarios of Exchange Server with or without ISA Server 2006.
These enhancements in ISA Server 2006 Service Pack 1
ISA Server 2006 Service Pack 1 supports the use of SAN certificates. Before ISA Server 2006 Service Pack 1, ISA Server only checked the certificate name and ignored the additional names in the SAN field of the certificate.
Use a self-signed certificate
One way to use certificates for publishing ISA Server is to use the SELFSSL.EXE tool from the IIS 6 kit. With the help of the SELFSSL tool, administrators can create certificates for Common Name (CN).
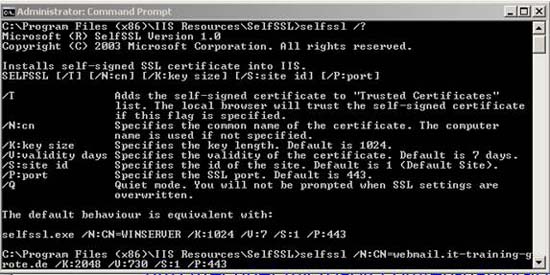
Figure 1: SELFSSL from the IIS 6 Resource Kit
Because the self-signed certificate is not issued by a trusted Root CA, the user must manually place the self-signed certificate in the trusted Root CA repository on the local ISA Server.
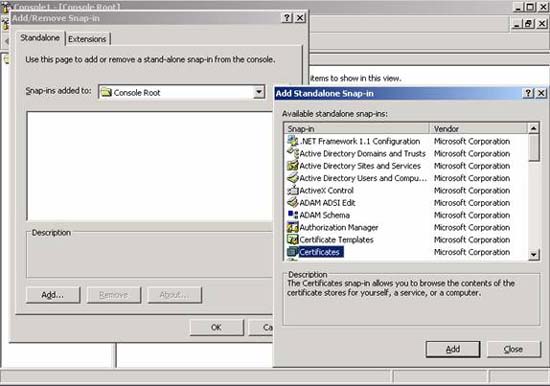
Figure 2: Additional Snap-In certificate
Next, select the local computer account as the certificate store to see all the installed certificates, which are the certificates that ISA Server will use for publishing and webchain scenarios.
Figure 3: Display certificate in the repository
Trusted Root CA certificates
ISA Server ensures that each certificate used can be authenticated against the issuing CA. ISA Server checks the certificate chain for Root CA. A list of trusted root CAs can be found in the local computer repository on ISA Server 2006 machines.
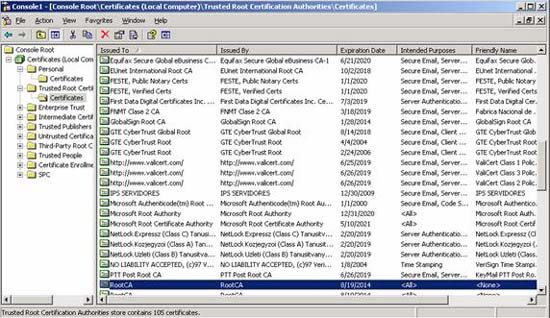
Figure 4: Trusted Root CA certificates
Certificates are used in the Web chain scenario
One of the bad features used in ISA Server 2006 is the use of certificates in web chain scenarios. Web chain is used to string web traffic from ISA Server with other Webproxy like ISA Server. To use a certificate in the webchain script, the user must have the prerequisites below:
- There is a client authentication certificate
- Trusted by a root CA
- There is a private key installed in the local computer certificate store
- Personal certificate store is installed in the firewall service account
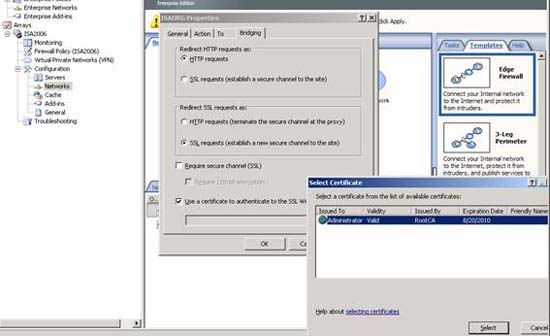
Figure 5: Select certificates in the Web chain scenario
Exchange Remote Connectivity Analyzer
Microsoft Exchange Remote Connectivity Analyzer is a very useful tool for testing different types of publishes with or without ISA Server, not using the required tools like Microsoft Outlook. Exchange Remote Connectivity Analyzer is also useful for validating the correct deployment of certificates on the Exchange Client Access Server (CAS) or on ISA Server.
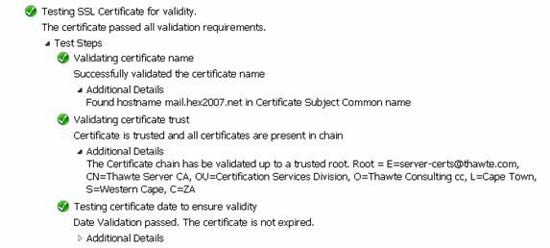
Figure 6: Exchange Remote Connectivity Analyzer
ISA Server 2006 Best Practice Analyzer
Another useful troubleshooting utility with certificate issues for ISA Server 2006 is the ISA Server 2006 Best Practice Analyzer, this is the database ISA Server analyzer with best practices from Microsoft to find possible configuration errors or related issues. For the purpose of troubleshooting certificates, ISABPA checks the ISA Server configuration and searches to see if the certificates are used in the publishing and web chain scenarios, plus the corresponding certificates. Whether found in the local computer certificate store.
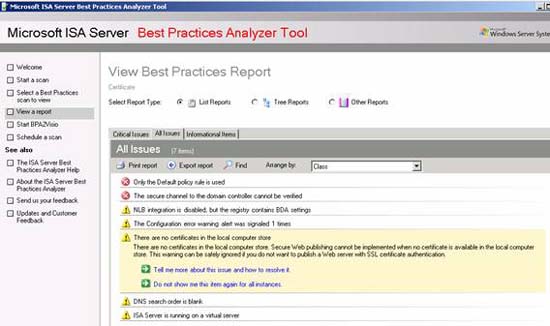
Figure 7: ISA Server Best Practices Analyzer
To give you some information about how ISABPA displays certificate-related issues, we have removed all certificates from the internal computer archive.
Conclude
In this article, I have provided you with some more information about ISA Server 2006 certificate deployment and troubleshooting. In addition, I also introduced some new ISA Server 2006 Service features. Pack 1 can extend ISA Server 2006's ability to use SAN certificates in a webserver publishing script.
You should read it
- ★ How to set up Windows Deployment Services on Windows Server 2016
- ★ Creating SSL Server 2008 Server with ISA 2006 Firewalls (Part 2)
- ★ Creating SSL Server 2008 Server with ISA 2006 Firewalls (Part 1)
- ★ Apache 2 supports SSL / TLS: Step-by-step instructions (continued Part II)
- ★ Create private cloud with Hyper-V (Part 2)