Edward Snowden released an application to turn inexpensive smartphones into security systems
Many times, digital security protection measures are not equal to the simplest common protection methods. A series of passwords is sometimes just like putting a note on the outside of the office door to guard it.
To protect the freedom of the press (initiated by the Freedom of Press Foundation FPF) Edward Snowden (who is also the director of FPF) has just released a Android application called Haven, which turns the phone into a successor. security for the house.
Haven uses mobile built-in hardware like camera, microphone, light sensor and accelerometer to monitor the house when you are away. It will take photos, record the sound of anyone who broke into the house and send it to the phone to alert the user. Haven also uses the technology to automatically adjust screen brightness when lighting conditions change.
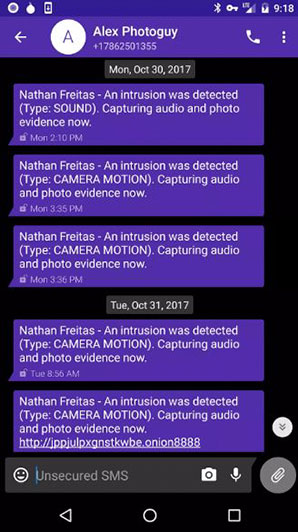
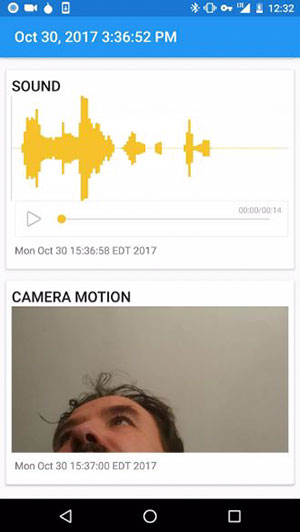
Images and sounds are sent immediately when there are signs of intrusion
Since sending photos and audio to mobile is not really safe, the application also encrypts each byte of data via Signal's secure messaging application. If that's still not enough, users can change the phone's settings to run with Orobot, turning the phone into a TOR Onion Service.
You can read more about Haven here https://guardianproject.github.io/haven/ or download the Haven Beta version here https://play.google.com/store/apps/details?id=org.havenapp. main
Haven is an open source project and Snowden also hopes programmers can review, contribute, edit according to their own use.
See more:
- 6 unexpected uses of webcam
- 3G phones help smart home control
- 3 golden rules to avoid fake attacks
You should read it
- ★ How to choose a CCTV surveillance camera
- ★ Security level of Wi-Fi security camera system
- ★ 'Imitate' China, the US will deploy dense camera system, a surveillance camera 4 people
- ★ 5 signs that your family's surveillance camera has been hacked
- ★ The risk of being 'reverse tracked', revealing a private image from a security camera