Additions for Exchange Server 2007 - Part 2: Default protection
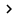 Part 1: Introduction steps
Part 1: Introduction steps
Marc Grote
Before you begin, note that this article is based on the Beta version of Windows Server 2008 and Exchange Server 2007 SP1, so it may have some features changed or removed in the final versions. same of products.
The calculation is reliable
Microsoft said that Exchange Server 2007 is a security design. Exchange 2007 was designed and developed according to a strict principle of a highly reliable security software development cycle - Trustworthy Computing Security Development Lifecycle (TWC), which was first introduced. in October 2002. Over time, Microsoft has changed a lot in this development cycle and security related improvements built into Exchange Server 2007. Microsoft said that Exchange Server 2007 has more security advantages than previous Exchange versions of Microsoft.
Default security
Microsoft has tried to protect Exchange Server 2007 with existing security technologies. One goal in the security plan is that every critical traffic bit will be encrypted by default. Except for the Server Message Block (SMB) cluster communication issues and some unified communications Unified Messaging (UM), Microsoft has achieved this goal. Exchange Server 2007 is Microsoft's first mailing system where users can use self-signed certificates. In addition, Exchange Server 2007 uses Kerberos for special communication issues, Secure Sockets Layer (SSL) and other encryption technologies.
Certificate
Exchange 2007 uses X.509 certificates to set up Secure Layer Security (TLS) and Secure Sockets Layer (SSL) transmission channels for communications between protocols such as HTTPS, SMTP, IMAP4 and POP3.
Note :
POP3 and SMTP access is disabled by default like in previous versions of Exchange Server. Exchange Server 2007 uses certificates for several components.
SMTP
Certificates are used for encryption and authentication for Domain Security (new points in Exchange Server 2007) between different Exchange organizations. These certificates are used to protect connections between Hub Transport servers and Edge Transport servers. Each SMTP communication between Hub Transport servers is encrypted.
Sync EdgeSync
Exchange Server 2007 uses a self-signed certificate to encrypt LDAP communication between ADAM instances of Edge Transport servers and an internal Active Directory server, on which Microsoft Exchange EdgeSync service communicates with Active Directory to replicate Active Directory information for ADAM case on Edge Transport server.
POP3 and IMAP4
Exchange Server 2007 uses certificates to authenticate and encrypt each session between Post Office Protocol version 3 (POP3) and Internet Message Access Protocol versions 4 (IMAP4) and Exchange Server 2007 clients.
Unified messaging (Unified Messaging)
Certificates are used to encrypt SMTP sessions for Hub Transport servers and for Unified Messaging (UM) IP gateways.
AutoDiscover
Certificates are used to encrypt communication between client and client access server - Client Access Server (CAS).
Client access applications
Exchange Server 2007 uses certificates to encrypt communication between the Client Access Server and clients such as Outlook 2007 (Outlook Anywhere aka RPC on HTTPS), Microsoft Outlook Web Access (OWA) and Exchange ActiveSync.
For security purposes, Microsoft advises users to use certificates created by the internal certificate authority of themselves or the third group of commerce certificates if in case you have multiple clients Access Exchange Server 2007 from non-domain member computers.
Mailing connector
Exchange Server 2007 uses several connectors (connectors) to relay traffic from the source to the destination server. Exchange Server 2007 uses two different types of connectors. One for incoming traffic, this can be configured on each Exchange Server 2007 and some connectors for outgoing mail traffic.
Exchange Server 2007 supports many different authentication mechanisms to protect mail transmission, or authentication or both.
You can use:
- Transport Layer Security - Transport Layer Security (TLS).
- Domain Security - Domain Security (Mutual Auth. TLS).
- Basic authentication after starting TLS.
- Authentication of Exchange Server.
- Integrated Windows authentication
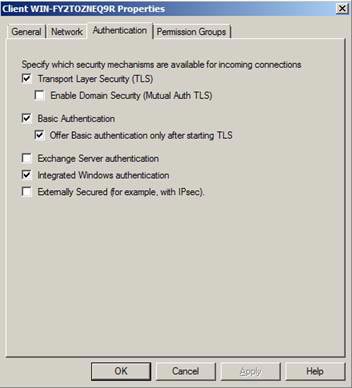
Figure 1: Connector authentication
Microsoft Edge Transport Server
The Microsoft Edge Transport Server is a role that must be installed on Windows Server 2003 or Windows Server 2008. The Edge Transport servers are mail relay servers and in addition they provide integrated anti-spam and anti-virus functionality. Microsoft Forefront Edge Security or of group products. The Microsoft Edge Transport Server is installed into the Windows workgroup and is not a part of a domain. The Edge Transport Server uses AD / AM (Active Directory Application Mode) to synchronize Active Directory data associated with the Edge Transport Server. The sync process is called Edge sync.
The Edge Transport Server provides some of the following features:
- Content Filtering
- Provider IP Allow and Block List
- Sender Filtering
- Sender Reputation
- SMTP Tarpiting
And some other features.
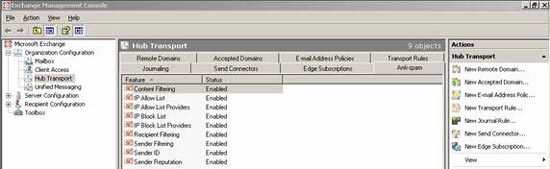
Figure 2: Edge Server Anti Spam
Microsoft Forefront
Microsoft Forefront is a Microsoft anti-spam and anti-virus solution, which is provided for Microsoft products like Exchange Server 2007, Microsoft Sharepoint Portal Server, Microsoft Windows clients and other products. One solution for Microsoft Exchange is Microsoft Forefront Edge Security. You can use Forefront Edge Security on the Microsoft Edge Transport Server and Hub Transport Servers, but it is better to use Forefront Edge Server Security in DMZ on Microsoft Edge Transport servers.
Functions of Microsoft Forefront security
- Provides layer security through Multiple Scan Engine Management to protect mail systems.
- Provides options for sophisticated scanning with additional and flexible:
- Scan 'in memory' to minimize the impact on Exchange servers to ensure optimization and efficiency.
- On-demand scanning, scheduling and real-time storage and database groups.
- Full protection for Outlook Web Access.
- Scan SMTP and Exchange Information Store to strengthen protection and effectiveness.
- Scan MTA mail for all messages routed through Exchange MTA Connectors (X.400, MS Mail, CC Mail, .).
- There is also a Microsoft virus scan API integration enabled in Exchange 2000 and 2003.
- Minimize worm-causing spam and protect storage information through Forefront Worm Purge.
- Identify all messages with untrusted attachments through flexible file filtering rules.
- Exclude infected attachments into a secure repository with Forefront Quarantine Manager.
- Automatically upload the latest virus signatures.
- Notify administrators of virus accidents or events via email, event blogs.
- There are many custom rejections for outgoing messages based on senders, recipients, and set of domain information by administrators.
Figure 3: Microsoft Forefront security
Security configuration utility - SCW (Windows Server 2003 SP1)
Exchange 2007 provides a SCW template for each Exchange 2007 server role. By using this template with SCW, you can configure Windows Server 2003 to block unnecessary services and ports for each Exchange server role. . When using the Security Configuration Wizard, you can create a sample XML file to use to help protect this server and other servers.
Figure 4: Security Configuration Wizard
Since SCW was first introduced in Windows Server 2003 SP1 - before Exchange Server 2007 is RTM, you must enable CSW to configure Exchange Server 2007. Exchange Server 2007 has two SCW configuration files that need to be installed on the server. want to run it.
With Hub Transport server
scwcmd register / kbname: Ex2007KB / kbfile: "% programfiles% MicrosoftExchange ServerscriptsExchange2007.xml
With the Edge Transport server
scwcmd register / kbname: Ex2007EdgeKB / kbfile: "% programfiles% MicrosoftExchange Serverscripts Exchange2007Edge.xm
Conclude
In this article, I have explained how secure Exchange Server 2007 is, Edge Transport Servers and what Anti Spam and Antivirus techniques can further improve security. . In Part 3 of this series, I will continue the discussion by showing you how to ensure client access to Exchange Server 2007 and some of the necessary changes in Exchange Server 2007 configuration.
 Part 3: Email client access protection
Part 3: Email client access protection
You should read it
- ★ Microsoft continues to 'delay' the plan to launch a new version of Exchange Server for another 4 years
- ★ Learn about the Security Configuration Wizard in Exchange Server 2007 - Part 1
- ★ Mobile communications with Exchange Server 2007 - Part 1: New device features and improvements
- ★ The attack on Microsoft Exchange increased while WannaCry showed signs of return
- ★ Transfer from Linux Mail Server to Exchange Server 2007 (Part 1)