The attack on Microsoft Exchange increased while WannaCry showed signs of return
The reason is simple, the patch has been released by Microsoft to Exchange Server users around the world, but it will certainly take a long time for these updates to be fully applied due to Microsoft Exchange users. organizations and businesses are known primarily for delays in applying changes to their systems.
Indeed, recent statistics from cybersecurity firm Check Point have shown a significant increase in the number of attacks targeting the critical vulnerability cluster ProxyLogon existing on Microsoft Exchange servers. Meanwhile, Palo Alto Networks claims to have at least 125,000 unpatched servers worldwide. That means these are all potential targets for cybercriminals.
Even as Microsoft actively accelerates the distribution of patches to partners from March 2, 2021, the number of Exchange Server attacks continues to increase sharply, specifically tripling globally, up to to tens of thousands of recorded cases to date.
The Microsoft Exchange vulnerability still appeals to cybercriminals
As of March 14, there are about 82,000 vulnerable Exchange servers around the world, according to Microsoft's internal research. About a week later, that is, by the end of March, this number has dropped significantly to about 30,000 exposed servers, according to data from RiskIQ. Despite the sharp decline, the number is still quite high, showing that ProxyLogon vulnerabilities in Exchange Server are still an attractive target for hackers.

Check Point's remote survey data last week showed more than 50,000 attack attempts globally involving Exchange Server, mostly targeting organizations in the government / military, manufacturing and banking sectors /. finance.
Microsoft Exchange Server is a popular email collaboration, calendar, and mailbox solution in the enterprise community. Users of this server are diverse, from giant corporations to small and medium businesses around the world. Therefore, successfully exploiting vulnerabilities in Exchange Server opens cybercriminals a huge opportunity to gain illegal profits from victim businesses.
Additionally, Microsoft says a ransomware variant called DearCry is taking advantage of the vulnerabilities to deploy ransomware on vulnerable Exchange servers.
WannaCry tends to make a comeback
In related news, despite being 'defeated' at the end of 2017, the number of security breaches related to the infamous WannaCry ransomware is showing signs of rebound.
In fact, this situation is in line with the general trend in the number of ransomware attacks worldwide in the past few months.
According to Check Point statistics, there has been a 57% increase in the number of ransomware attacks recorded in the past six months at a global level. More worrisome, the monthly increase since the beginning of 2021 is 9%.
Besides the commonly observed ransomware strains (Maze, Ryuk, REvil), Check Point noted that the number of organizations affected by WannaCry has increased by 53%.
' We found that the number of organizations affected by WannaCry increased more than 40 times in March 2021 compared to October 2020. New samples still use the EternalBlue exploit to spread the malware - has been with patches for more than 4 years ".
WannaCry ransomware spreads itself on computers using Windows operating systems. After being first discovered in May 2017, it quickly became one of the worst nightmares in the history of global cybersecurity with hundreds of thousands of computers infected, causing billions of losses. USD, followed by the collapse of countless businesses accidentally became victims.
With the efforts of all mankind, WannaCry is said to have been 'defeated' by the end of 2017. But in fact, it is not only not eradicated, but also showing signs of resurgence recently. .
Global security organizations continue to detect WannaCry every day, including many new variants that were designed to bypass patches aimed at it before. In January, for example, a new variant of WannaCry reached the top of the most popular ransomware in the US.
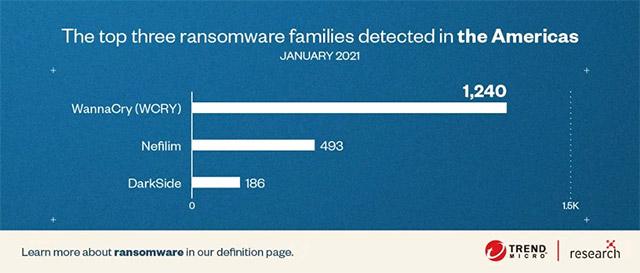
The reason behind this bizarre trend is because WannaCry has deep access to thousands of systems that are still vulnerable to EternalBlue now accessible over the public internet.
Check Point observes a similar trend starting December 2020, with the number of attacks continuing to grow by more than 12,000 by March 2021.
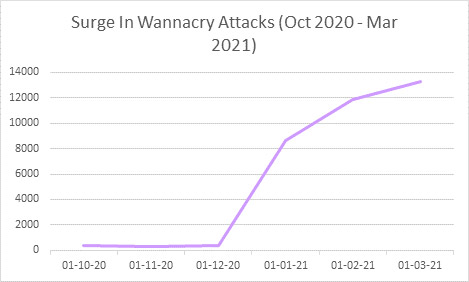
Thus, it can be seen that WannaCry is in fact still one of the popular and destructive malware types today. Raising vigilance against this ransomware strain is essential and should not be taken lightly.
You should read it
- ★ Vulnerability causes Exchange servers to 'crash' around the world: Microsoft offers a fix method
- ★ Switch from Exchange 2000/2003 to Exchange Server 2007 (part 1)
- ★ Transfer from Linux Mail Server to Exchange Server 2007 (Part 1)
- ★ Discover EMC in Exchange Server 2010 (Part 2)
- ★ Exchange Server 2007: ten minutes of instruction