10 tips for security
Erik Larkin
Network governance - In the world of humorous stories, bad guys are often geniuses but have evil morals. However, in the world of Web, hackers, spammers and phishers may be bad, but they are not regulated to be geniuses. They can live and survive by exploiting known security holes, but users do not patch or patch. Or by relying on the trends of millions of people to perform certain behaviors they are told.
However, although not a genius to avoid such general attacks, but just need to execute some fixes or patches, you will avoid most bad guys in today's web society.
1. Turn on the auto upgrade function
Do you turn off the automatic upgrade of Windows and other programs for some reason? However, the period of self-declared viruses (or exposures) to computer users is over. Modern attacks now often hide and perform implicit controls inside your computer, and untimely software will be fertile ground for these types of attacks to grow.
Today, a hacked website launches a series of probing actions on your computer to find an unpatched vulnerability to exploit. If a vulnerability is detected, it is better to hope that your antivirus program will catch the next attack. Otherwise you won't notice anything wrong when it infects the system.

However, you can completely block most of the exploits on the web by updating all programs in a timely manner - not just the operating system and browser. Attack sites often look for vulnerabilities in seemingly innocent looking external applications, such as QuickTime and WinZip, as well as in Windows and Internet Explorer. So turn on the automatic update features for any software that offers this service - this is the fastest and easiest way to update patches.
2. Find other vulnerabilities

A free security application released by Secunia can help you be safe in network access. Secunia Personal Software Inspector, now available free of charge, can perform scanning of installed software to see which programs are not updated. However, it does not stop here - for every 'overdue' program that the program finds, it will provide buttons to resolve quickly and easily, such as the Download Solution button, this is Get the software patch button that you don't need to open the browser.
The program also introduces you to a number of links to software vendor sites as well as full Secunia reports about vulnerabilities on your system. You can lock alerts for a certain program (but be careful before doing this).
Secunia PSI is not perfect and it is not always easy to update unsafe program components. However, for most applications, it provides patches quickly (which is very important).
3. Use the new browser with effective security features
Most dangerous attack websites cannot leave any trace. Small pieces of code inserted but not displayed on the page but can launch destructive attacks within it.
Avoiding such sites alone can be annoying. However, new site-blocking features in newly released Firefox 3 and Opera 9.5 browsers can prevent this type of attack.
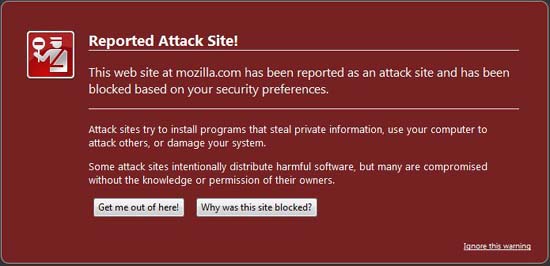
Both browsers extend the anti-phishing features from previous versions to block malicious sites whether they are hacked sites on legitimate sites or sites created by bad guys. Browsing is at the risk of stalking on such pages as an additional layer of protection. Microsoft also plans to add this self-feature to Internet Explorer 8.
4. Avoid Social Engineering
Most dangerous scammers use smart marketing methods to trick you into doing their own discretionary actions and from there entering your computer. A lot of social engineering attacks are ridiculously ludicrous, expressed by clumsy, misspelled grammar words, but that doesn't mean you will dismiss the danger. Occasionally, an attack can bypass your precaution and cause you to open malicious email attachments or downloadable files. A targeted attack can use your right name and headline of the business.
To combat them, use a powerful tool: VirusTotal.com. You can easily upload any file (up to 10MB) to the site and it will be scanned by 35 different antivirus engines; These include from Kaspersky, McAfee and Symantec. A report will tell you about what each engine concludes about your file. If you receive many specific warnings that include the names of certain threats, it is best to delete the file.
The lack of warnings will not guarantee a safe file, but this tool also gives you a lot of benefits. Obviously, using VirusTotal to check email attachments and downloads is not 100% sure, but you will avoid the tricky social engineering action.
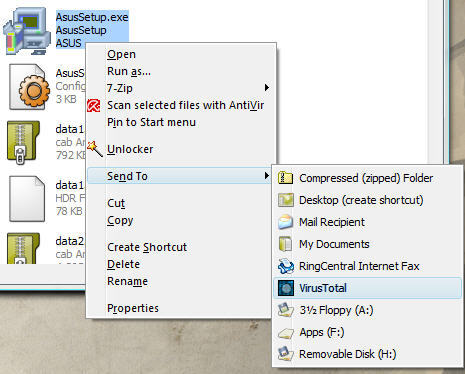
If using VirusTotal to become a habit and you want to scan files easily with VirusTotal, download VirusTotal's free Uploader utility. When you install this utility, just right-click a file, you'll see an option (under Send To ) to upload it to VirusTotal site.
5. Dominate malware
Typically, sign-based anti-virus software is vulnerable under a malware "storm". The attacker tries to avoid detection by overflowing the variables that security labs can analyze. Therefore, besides digital signatures, any antivirus program worthwhile today conducts pre-detection without requiring a complete sign to identify hidden malware.
A promising method of using behavioral analysis to identify malicious software is based on how malicious code attacks your computer. But your antivirus software is not enough to do it yourself. ThreatFire, a popular free download from PC Tools, adds a layer of protection based on such behavior. In recent tests, this is a tool that has identified 90% of malware based on its behavior.
Note : If you use the AVG Free antivirus program, stay tuned for ThreatFire until PC Tools releases a new version. The current version 3.5 is currently in conflict with AVG, but PC Tools said it will fix the problem.
6. Rescue your Inbox from spam
Spam filters are getting better and better, but spam technology is also growing, so some spam still penetrates through. Instead of having to take the most delete button to delete all this spam, try using disposable email addresses.
Such an address is the address you create when you visit an online shopping site, forum, or a service that requires you to enter an email address. If that address is spammed, you can leave that mailbox.
Yahoo's Web mail users can choose the Plus service for $ 20 per year, which includes a disposable email feature in AddressGuard (besides many other features). With this feature, you can click on the bookmark to create a new address for the site within 10 seconds.
Gmail users can simply add "+ everything " to their email address before using it, but if that address starts receiving spam you can't find a fix. You will create a filter in Gmail to lock all mail at that address.
For others, a free service provided from Spamgourmet.com can be quick and easy to install and use; It allows you to create disposable email addresses.
7. Improve the habit of counterfeiting
Performing stealthy acts in phishing attacks to forge personal information still exists and is being made popular, many fake sites can be difficult to distinguish from authenticated pages. However, some simple operations can help you ensure you never get phishing attacks again.
The best and simplest method is to never click on links in any email to access financial accounts. Instead, you must always type a URL or use a bookmark. That habit will protect you from most phishing attacks.
If you cannot make that change, use the latest version of Internet Explorer, Firefox or Opera to browse the web. They all have built-in features to block fake attack sites.
Last and not least, you should always keep an eye on fake tricks in using URLs like http://adwords.google.com.d0l9i.cn/select/Login. If you encounter this type of URL, you might think your domain is google.com. But in fact it is directed to d0l9i.cn, a site in China.
Internet Explorer 8 also uses an innovative feature called Domain Highlighting.
8. Keep your site safe
Sites may be like angelic lands but behind that scene it is a battle zone. And then the cannon is aimed at your site.
Phishers use automated tools to search the site to uncover vulnerabilities. If they detect a vulnerability, they will immediately launch attacks on the vulnerability by using additional malicious code to attack your visitors.
To help keep your site safe, start with some simple and free scans to find issues. First, fill out a form at Qualys.com to request a free scan for an IP address.
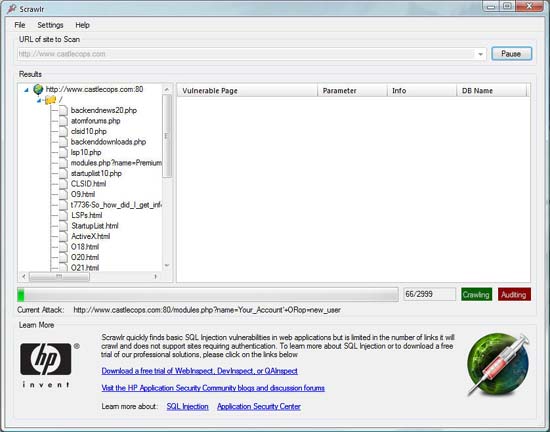
Next, download the free tool Scrawlr from HP. After installing this tool, use Scrawlr to scan SQL injection vulnerabilities for your site.
A specific status report provided by the two scanners will not guarantee your site is safe. For example, this program will find problems with JavaScript code, another type of attack. And while requesting or running the scan easily, fixing a reported vulnerability may require some work. However, that job will take less effort than fixing your site and your reputation after the site is attacked.
9. Create a password that is safe and easy to remember
Experts say we should use strong and unique passwords for all of our accounts. However, they do not tell us how to remember them, so most of us use the same password for all our accounts.
This is the simplest one that allows you to remember only one password, and still has a unique and strong password for each site you use. Add-on Password Hash (or PwdHash) for Firefox and Internet Explorer needs a simple password that you type and run through an algorithm that uses the site's domain name as part of the calculation. The utility will replace the result of a strong password before you send it to the site. All you have to do (after installing Password Hash) is to press the F2 key in the password box before typing.
10. Implement extended support for stubborn infections
Sometimes even the best antivirus program misses an infection. And when a virus or Trojan horse enters your system, removing it can be a lot more difficult. If you expect some other support, then this is the time to need extended support.
Many antivirus software manufacturers offer free scanners and can do it simply online through a web browser. This scan will take some time, because the scanning service will need to download a large number of Java or ActiveX components before it can start working, but they are easy to implement. You can run them with your installed antivirus application.
Trend Micro HouseCall: detect and remove malware; Works with both Internet Explorer and Firefox
BitDefender Online Scanner: detect and remove malware; Internet Explorer request.
Kaspersky Online Scanner: detect malware but not remove; Works with Internet Explorer and Firefox
F-Secure Online Virus Scanner: detect and remove malware; Requires Internet Explorer browser
ESET Online Scanner: detect and remove malware; Internet Explorer request