7 kinds of ransomware you didn't expect
You are browsing the web, checking email, a sudden message appears. Your computer, your data is locked, encrypted by ransomware. You cannot access until you pay the ransom. Most people know the process of making a ransomware, which is why ransomware creators are always looking to find and create new ransomware to make you pay. Here are some new ransomware you should know.
1. Cerber ransomware
If your computer is infected with Cerber ransomware (often hacked via email attachments placed under Microsoft Office documents), your data will be encrypted with each new file ending in .cerber .
Note: Unless you are in Russia or Ukraine or other former Soviet states such as Armenia, Azerbaijan, Belarus, Georgia, Kyrgyzstan, Kazakhstan, Moldova, Turkmenistan, Tajikistan or Uzbekistan, you will not be attacked by Cerber ransomware.
You know that you have been attacked by Cerber when you receive a notification on your computer screen. In addition, instructions on how to pay will be in each folder in TXT and HTML format. Alternatively, you can find a VBS file (Visual Basic Script) to show you how to pay. This Ransomware will tell you how to pay ransom and decode the data.
2. PUBG Ransomware
In April 2018, many people saw PUBG Ransomware take a different approach to encrypt users' computers for ransom. Instead of asking for money to unlock the file, the coder behind this strange malware gives you two choices:
- Play GameUnknown's Battlegrounds (cost $ 29.99 on Steam).
- Just paste the scammers' code provided on your screen.
In fact, this is not malware, although it is likely to cause problems and appear as a true ransomware. PUBG Ransomware is just a promotional tool for PlayerUnknown's Battlegrounds.
See also: Tips to become the last survivor of PlayerUnknown's Battlegrounds game
Looks like this ransomware is not bad, right? Yes, but it encrypts the file and changes the file extension to .pubg. In a nutshell, if you see two options, code and shooters, you should choose the appropriate action. If this is a real ransomware, you will have to pay at least 10 times the amount of that game. However, this is one of the most easily solved ransomware.
3. Jigsaw ransomware
Originally known as BitcoinBlackmailer, this Jigsaw ransomware got a new name thanks to the appearance of Billy the Puppet.
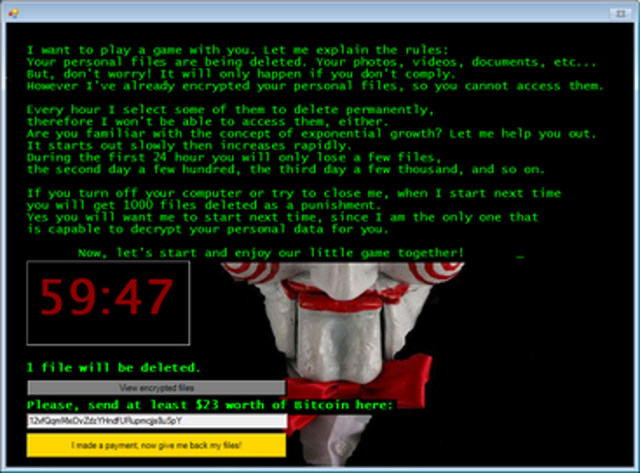
Discovered for the first time in April 2016, Jigsaw is distributed via spam emails and ransomware-infected attachments. When activated, Jigsaw locks the user's data and the Master Boot Record system (MBR), then displays the attached message.
This is essentially a threat: if you don't pay the ransom (in Bitcoin) within an hour, a file will be deleted from your computer. Each delayed hour, the number of deleted files will increase and restarting or attempting to terminate the process will result in 1000 files being deleted. The new versions of Jigsaw also threaten to disclose victim's sensitive information if they do not pay.
4. Ranscam ransomware
We are familiar with how ransomware works. You are infected with malware that encrypts important data or the entire computer, then forces you to pay an amount to decrypt the data through the decryption key.
The usual ransomware will be the same but Ranscam is different. It does not encrypt data to get ransom that your data will be permanently deleted.
5. FLocker ransomware
In June 2016, it was discovered that FLocker ransomware (ANDROIDOS_FLOCKER.A) has been developed on Android phones and tablets. Smart TVs with Android support have been added to its list of targets.
You may have heard of Flocker even if you didn't know its name. This is one of the kind of ransomware that displays warning 'law enforcement', notifying you that you have viewed this illegal document on the system. In addition, it targets users in Western Europe and North America; The fact is that everyone except those in Russia, Ukraine, or any other former Soviet Union country.
The victim is required to pay via the iTunes voucher, this is usually the target of the scammer and when you receive the money, you will get back control of your phone or Android TV.
6. Ransomware fake
It's amazing to know that some ransomware don't really do anything. Unlike PUBG Ransomware, these ransomware are simply fake ads, claiming to have control over your computer.
This ransomware is easy to solve but the 'power' of ransomware is really enough to make it profitable. Victims pay that completely do not know they really do not need to do that because their data is not encrypted.
The attacks of these types of ransomware often appear in the browser window. When it appears, you cannot close the window and notice 'your file has been encrypted, pay 300 USD with Bitcoin, this is the only solution'.
If you want to check if the ransomware you have encountered is real or just a scam, press Alt + F4 on Windows and Cmd + W on the Mac. If the window is closed, update your antivirus software immediately and scan your computer.
7. How to disguise ransomware
Finally, consider how ransomware deceives victims through its appearance. You already know that fake email attachments often have ransomware. In this case, the attachment will appear as a valid DOC file, sent by spam email and a request for money, this attachment is the bill. After downloading, your system is attacked.
However, there is another disguise, for example, DetoxCrypto ransomware (Ransom.DetoxCrypto) impersonating the famous Malwarebytes Anti-Malware software with the small Malwerbyte name change. There is also a Cryptolocker variant impersonating it as Windows Update.
You think you already know all the ransomware, but not, think again. Scammers will not stop until you get your money and they always appear with new designs.
If you're worried about ransomware, try some precautions such as regularly backing up your data, updating your computer, staying away from suspicious and strange files, using mail filtering, and running some sets. Internet security.
- If you don't want to be a victim of Ransomware, read this article
See more:
- List of the 3 most dangerous and scary Ransomware viruses
- Ransomware can encrypt cloud data
- Summary of effective Anti-Ransomware software
- With the NMR's 15 free Ransomware decoding tools, you won't need to ransom the file anymore