What is Deep Packet Inspection (DPI)? How does it work and how does it work in network security?
Also known as DPI, Deep Packet Inspection is a method of checking and managing advanced network traffic. It is also understandable that DPI is a packet filtering method for evaluating data. DPI gives network administrators powerful and thoroughly advanced management features, which conventional packet filtering processes - which only examine packet headers - cannot be detected.
In addition, DPI can also be used to redirect a packet to another destination. In more detail, DPI can be used to detect, locate, classify, re-route or block any package with specific data or code payloads, which cannot be done by normal packet filtering. This goes beyond the ability of just checking package headers.
- What is malware analysis? How are the steps taken?
 Deep Packet Inspection is a method of checking and managing advanced network traffic
Deep Packet Inspection is a method of checking and managing advanced network traffic
In fact, DPI can be partly or used in conjunction with Intrusion Prevention Systems (IPS), but it can also become an important feature of the firewall system. New system thanks to the ability to analyze traffic details, especially the title of packets and traffic data. DPI can also be used to monitor outbound traffic to ensure sensitive information does not leave (leaked) corporate networks based on a technology called data loss prevention (Data Loss Prevention). - DLP). DPI operates in the application layer of the Open Systems Interconnection (OSI) reference model.
So how does DPI work, often used in what cases, how does the technique work and does it contain limitations? We will find out later.
- Secure desktop application - weaknesses are often overlooked
Deep Packet Inspection - DPI
- How does DPI work?
- The case of using DPI in practice
- DPI deployment techniques
- The drawbacks of DPI
How does DPI work?
As mentioned, DPI is responsible for checking the content of data packets as they go through a certain test point, and making real-time decisions based on rules specified by the business. , internet service provider (ISP) or network administrator, depending on what the package contains. In other words, DPI will evaluate the content of a package going through a specific checkpoint. Then use the rules set up by the organization, service provider or system administrator to determine the specific things to do with that in real time.
Form of packet filtering in the past usually only considers the title information, just as you received a letter but only read the contents of the sender recording the envelope. The 'lack of tightness' in this case is unavoidable because it is partly due to technological limitations. Until recently, firewalls still did not possess the necessary processing capabilities to enforce deeper inspection processes for large traffic traffic in real time. Technological advances have allowed DPI to perform more advanced tests like you not only read the information flow outside the envelope, but also know how to open the envelope and read the contents of the letter.
- What is email encryption? Why does it play an important role in email security?
 DPI is responsible for checking the content of packages through a certain checkpoint and making decisions in real time
DPI is responsible for checking the content of packages through a certain checkpoint and making decisions in real time
DPI can check the content of messages, messages and identify the specific source of the application or service. After that, DPI can determine what to do with the application or service based on the information obtained.
In addition, filters can be programmed to search and reroute network traffic from a specific Internet Protocol (IP) address or a certain online service, for example. like Facebook.
- Alarming statistics on the situation of network security in our country in the first half of 2019
The case of using DPI in practice
DPI is highly applicable and is particularly useful in many practical use cases. It can be used as an intrusion detection layer to help identify early attacks that could bypass the firewall system.
For organizations that primarily use laptops in the workflow, DPI can act as an important security layer, which prevents malicious programs from entering the network in a way. more proactive. For example, DPI can detect and provide timely feedback in the case of a laptop being used to run prohibited applications.
Another great application of DPI for organizations and businesses is in network management to streamline network traffic. DPI helps to identify and prioritize the amount of data transmitted through the network because in many cases, there is a large amount of traffic that exists in the network. For example, a message with a high priority tag can be forwarded to less important messages or less important, related to regular internet browsing. DPI can also be used for data transfer to be adjusted to prevent peer abuse, thereby improving network performance.
- What is data exfiltration? How to prevent this dangerous behavior?
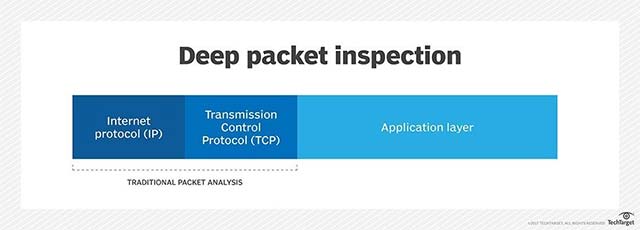 DPI's impact range compared to traditional package analysis techniques
DPI's impact range compared to traditional package analysis techniques
In addition, this feature will also be effective in blocking malicious requests. DPI can be used for defense purposes as a network security tool: Detecting and blocking viruses as well as other forms of malicious traffic.
Finally, DPI can also be used to prevent the risk of data leakage, such as from outgoing mail. It can check not only the amount of data coming in but also the amount of data transferred from the network data. By using specific rules, administrators can prevent sensitive data from being transmitted out of the network.
- Overview of building enterprise security detection and response system
DPI deployment techniques
There are a number of techniques related to the DPI process that an organization can take advantage of, including:
- Matching in templates and signatures. It is possible to analyze a package using the relevant database of recorded network attacks.
- IPS solutions. Can prevent detected attacks, as well as unwanted data.
- Unusual protocols. The default deny option can be used in this case, to help determine which content will be allowed to pass.
The drawbacks of DPI
No technology is 100% perfect, DPI is no exception. Although it offers many benefits, DPI also contains a few challenges in many cases. There are at least 3 major limitations of DPI, including:
First of all, DPI offers great efficiency in protecting the network against known vulnerabilities. But ironically, it could be a 'catalyst' to create new vulnerabilities. More specifically, DPI is highly effective in preventing overflow attacks, denial of service attacks (DoS), as well as some types of malware. However, it can also be exploited by crooks and become a tool to facilitate similar attacks.
Second, DPI contributes to increasing the complexity and difficulty of using existing firewall systems, as well as other security-related software. This technology requires regular updates and modifications to be able to maintain optimum performance.
Third, DPI can reduce network speed because it adds to the 'burden' of firewall processors.
- Find out about Ghidra - NSA's powerful cybersecurity tool
 Despite some disadvantages, DPI is still a reliable security choice for many network administrators
Despite some disadvantages, DPI is still a reliable security choice for many network administrators
Setting aside the above limitations, many network administrators still choose to adopt DPI technology as an effective effort to deal with the increase in the complexity and popularity of security risks. internet related.