What is BBBW Malware? How to remove and restore data?
Do files on your computer with the .BBBW extension prevent you from opening them? You may also have found a text document in the infected folders indicating that your files are encrypted and you should purchase a decryption tool to restore access to your data.
If so, your device has been infected with the BBBW ransomware and the cybercriminals have encrypted your files. So how does this ransomware variant work? Is it worth paying the ransom to decrypt your files? Do you have any other choice but to pay the ransom?
How BBBW . Works
The BBBW malware is a ransomware variant that infects a user's computer and encrypts almost any file format it can access. As a result, all infected files are given the .BBBW extension, making them unopenable.
For example, "audio.mp3" will become "audio.mp3.bbbw" and this also applies to all infected files on your computer. In addition to changing the file's format, the cybercriminals behind the virus also added text documents to the infected folder.
The text document states that the user's data has been encrypted with a key that cannot be decrypted by any other means. Criminals claim the only way to decrypt your data is to pay a high price for a decryption tool, which acts as a ransom they want to take from the victim.
To gain the victim's trust, cybercriminals offer to send any of the infected files. Victims are redirected to two or more email addresses so that the criminals can be contacted.
Scammers use an emergency clause stating that if victims contact them within a specific time frame, they will offer a 50% discount on the decryption tool. A good question to ask is: Should the ransom be paid?
The answer is no! Even if you pay the ransom, there is no guarantee that the criminals will give you the decryption tool. Even if they do, you will act as one of the sponsors of the bad guys, and they will use your money to trap other users. So paying a ransom for your data also indirectly harms others.
If already infected with this malware, what should you do next?
What to do if your PC is infected with BBBW ransomware?
How you deal with a BBBW ransomware infection depends on whether you have a backup of your data. Here's what you should do in both cases:
If there is a data backup, restore it

Infecting critical data with malware is the only weakness that fraudsters rely on to exploit users. Therefore, if you have a backup of your data, you can quickly restore files from the backup without paying a ransom.
However, you should remove all viruses from your computer before restoring a backup; otherwise your backup might also be infected. Therefore:
- Do not connect an external drive containing the backup to your device unless it has been completely removed from the virus.
- Do not restore backups from online sources by opening them on the same infected computer.
Instead, follow these steps (if applicable):
1. First, boot the system into Safe Mode. If you don't know how, refer to TipsMake's guide on how to boot into Safe Mode on Windows 10, Windows 11 and macOS.
2. After booting into Safe Mode, download anti-virus software and perform a complete malware scan to make sure your system is free of malware.
3. Reboot and exit Safe Mode once the scan is complete and permanently delete your infected files.
4. Use the System Restore feature on Windows to restore your computer to the state it was in before it was infected with a virus, or use a Time Machine backup in macOS to restore data. You can also factory reset your Windows (or macOS) device if you want the operating system to be cleaner.
5. After resetting or restoring your computer, you can restore your files from a backup.
Without any backups, can you still deal with malware? Yes, and here's how.
If you don't have a backup, decrypt the files if you can
If your device has been infected with the BBBW ransomware but you don't have a backup, the only way to recover your files is to decrypt them.
Since the BBBW virus belongs to the STOP/DJVU ransomware infection family, you must use decryption tools that can decrypt files affected by this variant.
After testing different ransomware decryptors, it can be concluded that Emsisoft's decoder for STOP/DJVU is the best one for removing files infected with BBBW variant.
Follow the steps below to decrypt files using Emsisoft decoder for STOP/DJVU:
1. Download Emsisoft decoder for STOP/DJVU.
2. Right click on the downloaded file and select Run as administrator .
3. When the UAC window appears, click Yes.
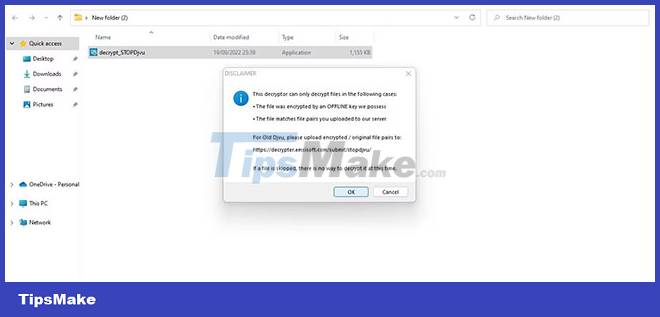
4. In the License Terms window , click I agree and then click OK.
5. In the Decryptor tab , click the Add folder button to add folders containing encrypted files.
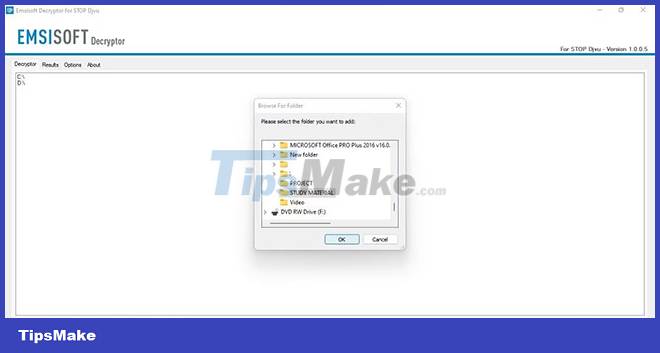
6. If you added the wrong folder, select it and select Remove object(s).

7. In the Options tab , check the Keep encrypted files box . Doing this will ensure that if your file is lost during decryption, the decryption process changes its contents, or the file becomes unusable, you will still have the original encrypted files to decrypt. by other tools.

8. When all the folders with the files you want to decrypt are added, click Decrypt.

9. Let the tool complete the decryption process and verify if it was successful.
If the tool successfully decrypts your files, the article recommends that you create a backup of your data and store it online. Then follow the same steps mentioned in the previous section, i.e. boot into Safe Mode, run a malware scan, restore and reset the operating system, and restore files from a backup.
This will ensure that your operating system is completely free of malware, preventing your files from becoming infected with viruses in the future.
Note that Emsisoft's decryptor does not always succeed in decrypting the file, and when that happens, it displays one of the following errors:
- Error: Unable to decrypt file with ID: [your ID]: You receive this error because the decrypter database does not have a decryption key to decrypt your file. Therefore, consider using another tool.
- No key for New Variant online ID: [your ID] - Notice: this ID appears to be an online ID; decryption is impossible: As the error message says, scammers have encrypted your files with an online key, so only they can decrypt the file. Therefore, it is only possible to recover encrypted data by paying a ransom.
- Result: No key for new variant offline ID: [example ID] This ID appears to be an offline ID. Decryption may be possible in the future: This error message indicates that the fraudsters used an offline key to encrypt the file, but it is currently unavailable. If the decryption key is uploaded to the decoder, you can decrypt the files in the future. So wait or try another decoder.
Hopefully now you have a better understanding of BBBW malware and how to safely restore your files from backup without paying scammers. Furthermore, if you don't have a backup of your files, you can use tools to decrypt infected files.