Things to know about an information system security manager
Today, due to the actual demand, large IT security departments will often need a person to manage the Information System Security Manager.This person will perform the role of supervisor, manager and responsible for professional training for other information security personnel.Below are details of what you need to know if you want to pursue and build the future with this job.
The general responsibility of an information system security manager
Like all other professions, responsibility in work is indispensable.Depending on the needs of each business, information system security managers must take on different jobs, however, they are generally responsible for fulfilling their responsibilities. after:
- Managing the deployment and development of an IT security system of an organization or enterprise.
- Ensure security policies, standards and procedures are established and enforced.
- Coordinate checking and evaluating information security ability.
- Monitor a corporate information system security team (as well as personal telecommute employees if available).
Information system security managers are also known as IT security managers (IT security managers), who in this profession will often work full-time in the office environment.Overtime is more frequent than other jobs, simply because the system security team will often have to work constantly with a security issue or threat. until it is completely resolved, instead of returning home on time and temporarily putting aside everything for the next day to do it.
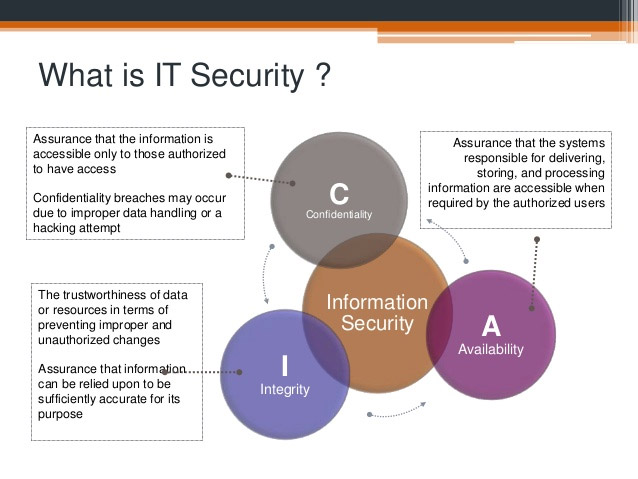
Core work: Designing a security policy for the system
To design a security policy, an information system security manager may have to collect and reorganize technical information according to the company's goals and needs, as well as the products Current security and ongoing programs and activities of the company.They will also need to conduct analysis and assessment of possible risks and then make sure to come up with solutions to minimize those risks.
This platform work aims to create information security plans and policies for organizations.An information system security manager will be responsible for determining the organization's current security infrastructure, as well as determining what type of security must be designed and implemented to meet the requirements. of that organization.
Finally, an information system security manager will have to monitor the remaining members of the system security team as they conduct design and implementation of security solutions required by the organization.
Daily work
The information system security manager will provide the necessary instructions when the security team must analyze and evaluate, handle security vulnerabilities and manage security systems such as antivirus, firewall, patch management, unauthorized intrusion detection and daily encryption.
Sometimes an information system security manager will be required to interact and advise non-technical staff in the organization or company.For example, in staff meetings or other situations that need to address security issues.
In the event of a security disaster on the system leading to data loss, the security manager will be responsible for supporting data recovery.
Knowledge and skills needed
An information system security manager will often have knowledge of several areas, including:
- Be knowledgeable about existing security tools and programs.
- Knowledge of procedures and security in business.
- Implementing hardware and software security.
- Techniques and coding tools.
- Have knowledge of different communication protocols.
- Information system security managers should also have good decision making and situational skills.
- Experience, training and certification required
Although there are many requirements for this position depending on the organization offering the recruitment, in general it can be said that this job is not simple and especially unsuitable for 'newcomers'. ', young people with experience.Typically, organizations will require their future information system security managers to have at least a bachelor's degree in a computer-related field plus nine years of practical work experience.
However, employers can ask for more years of experience if you don't get the university degree they want.The work experience of candidates should be directly related to information security, and management and leadership skills are also a huge plus.Sometimes, just knowledge and experience is still not enough, for a management title, the skill is also extremely important.
The following certifications may also be required:
- MCSE: Security
- Unix / Linux certificate
If you want to become an IT security manager in the future, you need to focus on building strong security skills.If you are still in school, adjust the selection of courses to be reasonable to develop these skills.On the other hand, take part in basic training courses and devote one or two certificates, then apply to work at low-level security positions, then train your skills and accumulate the necessary experience. In fact, the promotion opportunity will come to you.
Good luck!
See more:
- What you need to know about an information security analyst
- Things to know about a CIO (CIO)
- Top 10 IT jobs with the highest salary in the future
- How much money do programmers in the US earn each year?