Microsoft shook hands with VirusTotal in resolving malicious code issues that affected MSI files
Microsoft and the Chronicle's VirusTotal team have teamed up to develop tools to make warnings faster and more accurate for modified MSI files to turn into malicious Java code repositories.
When developers create a software, they often sign it using digital code-signing to confirm that they are the new person who created the software.Another benefit is that all modifications to signed Windows PE (.exe) will cause the signature to become invalid, which helps provide an extra layer of security to ensure that the program does not fake.

Although developers can also sign a Microsoft Installer (MSI) file with a digital signature certificate, in this case the signatures cannot guarantee whether the MSI file has been tampered with or not yetThis is because the contents of the signed MSI file are fully editable, while the signature will remain in effect.
- Microsoft changes the default settings to keep the content stored on the hard drive safe
The above problem contributes to the problem because it can allow an attacker to use MSI files as a storage mechanism for malicious programs, while those files are still displayed as signed.In addition, some antivirus software rely on digital signatures to help determine whether a file is malicious or not, so this may also allow maliciously tampered files to avoid being detected. .
The problem with this method of distributing malware is that another program will still be required to extract malicious code from the MSI file and execute it.However, according to the new VirusTotal blog post, all this will change if a malicious Java JAR file is added to the signed MSI file.
Zip files are read from the end
Java archive files (JAR) are simply Zip files containing the necessary components, code, and declarations that allow them to be executed by the Java launcher.According to Zip file characteristics, a valid Zip archive will have to end with "the end of the central directory record", indicating where the ZIP file is at the end and containing the titles for each file stored. Inside.
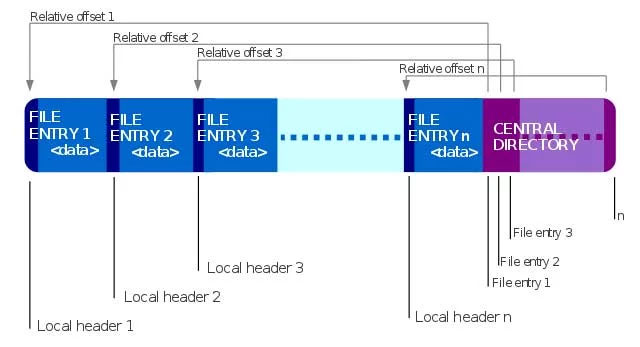
VirusTotal explains that because JAR files are simply Zip files, so when Java executes a file, it reads from the end of the file to the beginning of the archive file and ignores the rest of the MSI file.This allows an attacker to distribute signed MSI files with malicious JAR files, rename them to JAR files, and then execute them with Java's javaw.exe launcher.
'The problem lies in the ZIP-based JAR file format for storing different components and resources, and this ZIP type is correctly identified by the presence of the end of the central directory record (located at the end of the archive) to allow easy append of new files. When Java opens the JAR file, it will look at the end instead of the beginning of the file, so the JAR file will be executed independently of the data at the beginning of the file. In addition, on Microsoft Windows systems, the Java Runtime Environment installation program will register the default link for JAR files so that when you double-click the JAR file on the computer, the system will automatically run the file with "javaw -jar" ".
To illustrate this kind of malicious MSI file, VirusTotal has come up with a real-world discovery pattern using the above method.Chronicle also revealed that vendors operating on VirusTotal discovered these types of models, calling them "Jacksbot" and they were extremely rare.
"So far, this technique has been proven extremely rare. Although you can connect anything to the end of MSI files, in this particular case, only one JAR file will execute. as described, 'Chronicle's representative said.
- The Internet is experiencing a huge problem with C / C ++, causing developers to "sweat"
VirusTotal works with Microsoft
Two security experts Mark Russinovich and Mark Cook of Microsoft have updated their Sigcheck tool to find out if the signed MSI file is fake.This new feature can be found in Sigcheck 2.70 and is being used by VirusTotal to identify whether the signed MSI files are modified when they are uploaded to their service.
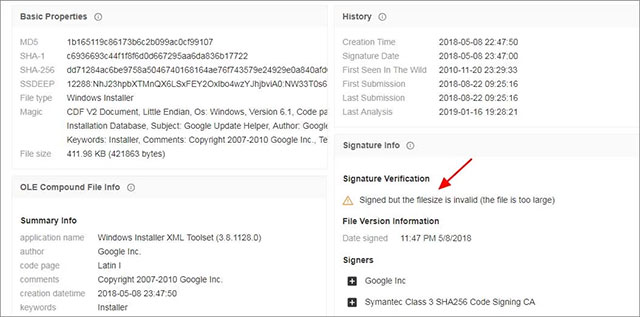
If Sigcheck discovers a signed MSI file is modified, it will display a warning with content Signed but the filesize is invalid (the file is too large) , temporarily translated: This file has been signed but the file size is not valid (file too large).You can refer to the illustration below.
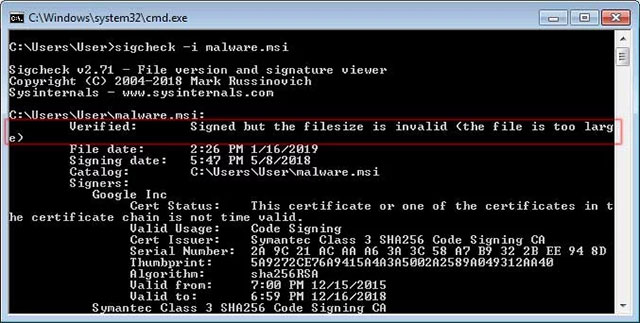
This new discovery will also be displayed in the command line as shown below:
Microsoft Security Response Center (Microsoft Security Response Center) also reviewed these malicious file types and stated that they will display as signed in the latest versions of Windows 10 and Java (updated). ).And Microsoft has decided not to fix this problem in current versions of Windows, at least at this point.
"This attack vector has been verified in the latest versions of Windows 10 and Java is available at the present time (Windows 10 Version 1809 and Java SE Runtime Environment 8 Update 191). Microsoft has decided that they will Do not fix this problem on current versions of Windows'.
See more:
- The first Windows 10 build for foldable computers appeared on Microsoft servers
- Microsoft launched a video reminding Windows 7 "death" and advised users to upgrade to Windows 10
- The corner of getting rich: A company hung a $ 1 million prize for anyone who hacked WhatsApp and iMessage
- Hacker purged two-factor security just by automated phishing attacks