Malicious Code EvilGnome attacks Linux systems with many rare tricks
Earlier this month, Intezer Labs' security researchers discovered a new Linux malware, capable of disguising itself as a Gnome shell extension, and designed to track those people are using Linux desktops, making them unable to recognize its appearance.
This backdoor implant is named EvilGnome, and is still not recognized by any anti-malware tool on VirusTotal [1, 2, 3]. More dangerous, it is also accompanied by a number of extremely rare malicious capabilities in the range of malware targeting the Linux system.
 EvilGnome has not been identified by any anti-malware tool on VirusTotal
EvilGnome has not been identified by any anti-malware tool on VirusTotal
"The malicious features included with EvilGnome, including desktop screenshots, data theft (files), automatic recording of the user's microphone audio, and the ability to download and execute. new malicious modules in the future More dangerous, this backdoor implant also has a keylogger function in development, and once completed, it can record comments, passwords and Compiled metadata, which normally doesn't appear in Linux malware versions has ever been recorded, 'said Intezer Labs research team.
- New Android Trojans lead users to phishing websites by notification on the application
Linux EvilGnome malicious code
- Infection through self-extracting archives
- Multi-backdoor modules with the same spy features
- Each suspicious contact with Gamaredon Group hacker group
Infection through self-extracting archives
EvilGnome is distributed with the help of self-extracting repositories created with the shell makeelf script, in which all metadata forms during the creation of a malicious 'payload' repository in the target its threads.
The malicious infection process is automated with the help of an auto-run argument, left in the self-executing payload titles. This argument is responsible for guiding malware to launch the file named setup.sh, thereby adding the malware agent to the address ~ / .cache / gnome-software / gnome- shell-extensions / folder, then try to sneak into the victim's system and disguise as a Gnome shell extension.
- The official GandCrab 5.2 decoder was released, ending the bad nightmare called GandCrab Ransomware
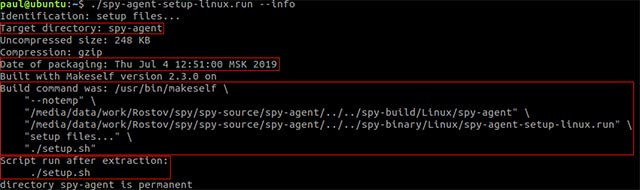 Self-extracting metadata metadata
Self-extracting metadata metadata
In addition, EvilGnome will also add a gnome-shell-ext.sh shell script to the crontab of the infected Linux computer, the script is designed to check whether spyware agents are running ( minute checking).
The gnome-shell-ext.sh script will be executed at the end of the infection process, enabling the launch of gnome-shell-ext spyware agents.
EvilGnome's configuration, stored in the rtp.dat file, will also be included in the self-extracting archive, and it allows the backdoor to obtain the commander's server and control IP address (C2).
- Your Linux system can be hacked just by opening a file in Vim or Neovim Editor
Multi-backdoor modules with the same spy features
This malware comes with 5 different modules. In particular, each module is designed to operate in a separate thread and can occupy "access to shared resources (as configured), which is securely protected by the mutex".
While analyzing EvilGnome's backdoor implant, Intezer Labs researchers found the following modules:
- ShooterAudio - record audio from a user microphone and upload it to C2
- ShooterImage - take a screenshot of your computer screen and upload it to C2
- ShooterFile - scan file system (file system) for newly created files and upload them to C2
- ShooterPing - receive new orders from C2, filter data, and can download and execute new malicious payloads
- ShooterKey - in development and not yet used, will most likely be a keylog module. Once completed, it can record comments, passwords and compiled metadata on the system
All traffic sent to and from the malware's C2 servers will be encrypted and decrypted by EvilGnome through RC5 symmetric block encryption, using the same decryption key with help from a variant of the open source library RC5Simple.
According to an analysis of Intezer Labs researchers, in case they cannot communicate with their C2 server, the malware samples will store all output data and data they steal in the mail. ~ / .cache / gnome-software / gnome-shell-extensions / tmp / on the memory itself of infected Linux systems.
- Shade ransomware, the nightmare of 5 years ago is showing signs of returning
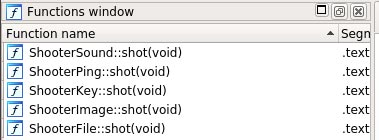 EvilGnome's module list
EvilGnome's module list
Each suspicious contact with Gamaredon Group hacker group
EvilGnome also seems to be connected to a group of hackers that distribute malware from Russia called Gamaredon Group. According to a report by a group of security intelligence experts from Unit 42 team (belonging to Palo Alto Networks security company), Russian Gamaredon Group has been operating at least since 2013 and is the name behind many battles. High-tech attack (ATP) attacks persist and leave much serious damage.
Although initially, Gamaredon Group relied heavily on the tools available to launch offensive campaigns, but then the group recruited many more members with high technical expertise, and gradually moving to custom malware development with a significantly increased level of danger.
According to an analysis of Intezer Labs, malware developers behind EvilGnome and Gamaredon Group contacted each other through the use of the same hosting service provider, as well as the use of servers. C2 is connected to the domain (domain) related to the Russian hacker group of this malicious software.
In addition, both EvilGnome and Gamaredon Group use port 3436 to connect to their C2 server via SSH, with "2 additional servers owning the same domain name as the Gamaredon domain name method (use .space TTLD and ddns) ", was found by Intezer Labs security research teams in EvilGnome's C2 server provider infrastructure.
- The most dangerous hackers on the planet: Anonymous, Equation Group, Department 121 . What do you know about them?
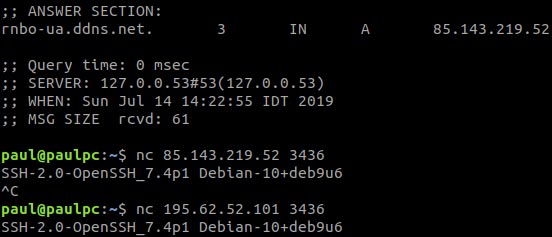 The SSH port opens on EvilGnome and Gamaredon's C2 server
The SSH port opens on EvilGnome and Gamaredon's C2 server
Last but not least, though, Gamaredon Group has never developed or used any malware related to Linux, but the modules and techniques used by EvilGnome's backdoor like "use SFX, persistence with task scheduler and deployment of information stealing tools . is extremely coincident with the techniques used by many Russian hackers so far. .
Finally, Intezer Labs' security team released a list of system attack traces (IOC) after ending EvilGnome's behavioral analysis, including sample hashing of malicious software. harm, also like the IP address / domain it shares with other tools developed by Gamaredon Group.
It is not surprising that future investigation results show that EvilGnome is closely related to Gamaredon Group, or even developed by this hacker group.
You should read it
- ★ Discover a new kind of malicious code that can record the phone call to extort money
- ★ Threats and risks from malware on USB Flash
- ★ Decode xHelper - the kind of immortal malicious code on Android, still 'alive' after factory reset
- ★ Researchers create malware based on artificial intelligence
- ★ CMC InfoSec provides malware removal tool for online DDoS attack