What is Salami Attack?
A Salami attack can wreak havoc on individuals and organizations. This is a stealthy method to steal small amounts of money or data from many people or businesses, often without the victim knowing about the theft.
What is Salami Attack?
In a Salami attack, attackers make small, incremental changes to the system to steal small amounts of money or resources. The changes are often so small that they go unnoticed, but add up to a substantial amount.
This attack is so named because it is similar to slicing Salami (the name of a sausage) when enjoyed. The first Salami attack took place in the 1940s, when a group of programmers from the Soviet Union stole money from the government, manipulated transactions, and collected a lot of cash.
Salami slicing (another name for the Salami attack) can also involve breaking an important target into smaller, more manageable chunks and working on each separately. This can make it easier to achieve your master plan and can also make it less noticeable to others.
These attacks can be difficult to detect because the changes are often very subtle and hackers can cover their tracks by masquerading as legitimate attacks.
How does the Salami attack work?

Users with high-level access to the network can perform a Salami attack by installing a Trojan Horse that automatically rounds a customer's amount in a transaction. Most clients assume that deductions are transaction fees. This is because the attackers make the number as low as possible to avoid detection.
Two principles are very useful in performing the Salami attack:
1. Stealth
Salami attacks often involve making changes that are difficult for others to detect or object to. This could include hiding changes in complicated, confusing documents, or making changes when they are less likely to be noticed.
Financial institutions are sometimes held responsible for attacks on their customers, attempting to make illegal shady transactions in financial documents.
2. Perseverance
Attacking Salami often requires persistence, as it can take a long time to make enough small changes to achieve the overall goal. It may be necessary to provide justifications or explanations for each change to make it seem reasonable or necessary.
Types of Salami . Attacks
Some common types of Salami attacks used in the cybercrime world include:
Financial Salami Attack
This is the most common form. These attacks involve stealing small amounts of funds from multiple accounts, in order to remain undetected.
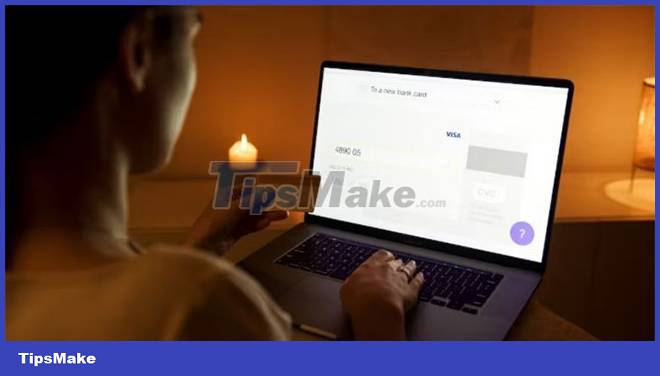
Salami activities of this type usually involve credit cards. A fraud device will be installed on the credit card swiping device and collect data on the card as it is being processed. The resulting data is then used to create fake credit cards or make unauthorized charges on the original card.
Another similar form of financial Salami attack is ATM skimming, which involves installing a device on an ATM to collect data on a bank card as it is inserted into the machine. The collected data is then used to create fake bank cards or make unauthorized withdrawals from accounts.
Another type is payroll fraud, which involves altering employees' payroll information, like bank account numbers and direct deposit amounts, to transfer part of their wages into the attacker's account. labour. Similarly, invoice fraud involves altering the details of a legitimate supplier's bill into an attacker's account. Additionally, in an investment scam, false or misleading information is used to convince victims to invest in a fraudulent scheme, resulting in their investment funds being stolen.
Attack Salami Information
These attacks involve stealing or changing small pieces of information from multiple accounts to go undetected.
Attack on Salami CPU
These attacks involve the use of malware to covertly consume a small amount of the computer's processing power.
Cyber Salami Attack
These attacks involve the use of malware to consume a small amount of the network's bandwidth, in order to remain undetected.
How to protect yourself from a Salami attack?
There are several ways you can protect yourself from a Salami attack.
Use a unique password

Use a secure, unique password for your account. Using the same password for multiple accounts makes it easier for perpetrators to gain access to your account if they get the password for one of them. It's also a good idea to use a password manager to help you create and manage strong, unique passwords for all your accounts.
Enable two-factor authentication (2FA)
Enabling 2FA on your account provides it. 2FA provides an extra layer of security. With 2FA, you must enter a code sent to your phone or email in addition to your password when logging into your account. This makes it much harder for others to access your account, even if they get your password.
Use software update
Firewalls help protect your computer or network from unauthorized access, while antivirus software can detect and remove malware from your system. You should keep both of these tools up to date and run regular scans to help protect your system from malware.
Additionally, installing updates for your operating system and other software can help protect you from vulnerabilities that attackers can exploit. You should also keep your devices, such as computers and phones, up to date with the latest security patches.
Avoid unknown links
When you click on links or download attachments on unsafe websites, use caution. Also, look out for messages that contain suspicious links or attachments, as they can be used to distribute malware or trick you into providing sensitive information. Only click on links or download attachments from sources you trust.
Follow all your accounts
Monitor your account and credit report regularly. Monitoring accounts and credit reports can help you spot any unusual activity or unauthorized charges. If you see anything unusual, tell your bank or credit card company right away.
Be careful with phishing

Attackers often use phishing attacks to trick people into providing sensitive information, such as passwords or credit card numbers. Be wary of suspicious emails or website links, and don't provide personal information in response to unsolicited requests.
 What is the difference between bandwidth, speed and network throughput?
What is the difference between bandwidth, speed and network throughput? What is Fault Injection Attack (FIA)? Is it worrisome?
What is Fault Injection Attack (FIA)? Is it worrisome? What are UDF files?
What are UDF files? Difference between EXE file and MSI file
Difference between EXE file and MSI file What is hardware hacking? Is it worrisome?
What is hardware hacking? Is it worrisome? Should SSDs be defragmented?
Should SSDs be defragmented?