Intel released Microcode for CPU Linux to fix Meltdown and Specter
This article is in the series: Overview of vulnerabilities on Intel, AMD, ARM chips: Meltdown and Specter. Please read all the articles in the series to get information as well as take steps to protect your device against these two serious security holes.
On January 8, Intel released micro-data files for Linux processors to mitigate the effects of Meltdown and Specter vulnerabilities on their CPUs. By microcode files, the operating system can fix errors without performing BIOS updates on the computer.
- Why Intel killed the BIOS, switched to UEFI?
- How to enter BIOS (UEFI) on Windows 10
According to Intel, this release is available for 40 Linux versions and 2371 Intel processors, from the latest to the Pentium Processor 150 Mhz since 1995.
This release of microcode files only fixes errors on certain processors. Below is a list of updated microprocessors, the first column is the processor type, the second is the release note, and the last is the number of new releases.
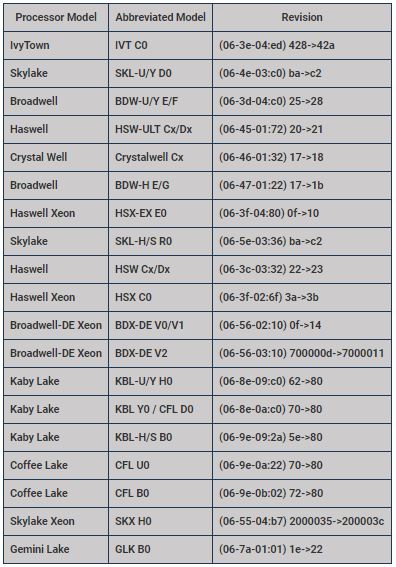
Processor tables and updates
Windows users can also use these micro-updates but need to be tested by Microsoft first and released later. The final microcode update was released in 2015. It is not known whether Microsoft intends to release the update.
Application of microcode data files to Linux
On Linux, using these files is quite easy because Linux distributions are available as updates. To install, the best way is to use the Package Manager package management tool in the Linux distribution.
For Debian and Ubuntu, APT is recommended to install. Package Manager also installs dependencies if demand, such as incode-tool, for example. Redhat and Centos need to use Yum and find microcodt_ctl.
If you cannot update via Package Manager, you can install it manually. On modern Linux distributions it is often necessary to copy the downloaded intel-ucode directory, then to / lib / firmware, then run echo 1> / sys / devices / system / cpu / microcode / reload. You can see the example of updating Ubuntu manually here. https://www.bleepingcomputer.com/forums/t/667654/latest-ubuntu-meltdownspectre-updates-break-my-pc/?p=4420456
Ubuntu uses microcode microcode
This is Intel's instructions for installing microcode
- Instructions for updating microcode -
This package contains microcode files in 2 formats:
* microcode.dat
* intel-ucode directory
microcode.dat is a text file that is still used on some Linux distributions. The system can be updated via the update interface on the kernel
CONFIG_MICROCODE_OLD_INTERFACE = y.
To update microcode.dat for the system, need:
1. Be sure to have / dev / cpu / microcode
2. Write microcode.dat on the file, for example
dd if = microcode.dat of = / dev / cpu / microcode bs = 1M
The intel-ucode folder contains micro-binary files named after the template
family-model-stepping. The file is supported on most Linux kernels, usually in the / lib / firmware directory and can be updated via the microcode reload interface.
To update the intel-ucode package needed:
1. Be sure to have / sys / devices / system / cpu / microcode / reload
2. Copy the intel-ucode directory to / lib / firmware, overwrite the internal files
/ lib / firmware / intel-ucode /
3. Write on the reload interface of 1 to reload the microcode file, for example
echo 1> / sys / devices / system / cpu / microcode / reload
See more:
- AMD released a firmware update for Specter to fix the vulnerability on the CPU
- How slow is Meltdown and Specter, which is Microsoft's explanation
- There is an iOS and Mac update that fixes the Specter vulnerability
You should read it
- ★ How to update Kali Linux and fix errors when updating
- ★ How to prevent and handle when Windows Update deletes Linux
- ★ Immediately patch CWP vulnerability that allows code execution as root on Linux servers
- ★ How to set up or disable Linux Mint update notifications
- ★ 14 interesting Linux commands in Terminal