Installing Linux on Windows 8 will be a problem
One of the most influential changes when manufacturers put Windows 8 on their device is the appearance of UEFI instead of BIOS.
UEFI (Unified Extensible Firmware Interface - Unified extensible firmware interface) outperforms the old BIOS (Basic Input / Output System) in all aspects, except for one thing: UEFI will prevent you from installing Linux a Windows 8 bundle.
Every time you start your computer (laptop, PC), the BIOS is the operating system - or is it not the first mini control system loaded into memory (The operating system is stored on the HDD / SDD while the BIOS is stored on a separate memory of the mainboard). It will check the status of the hardware components before allowing the user's operating system to load into memory and reassign the operating system. The BIOS has dominated the computing world for the past 30 years, but now it seems that the platform is about to retire when Microsoft and its hardware manufacturing partners are working to support UEFI development.
The ancient interface of the BIOS.
There is a similar BIOS function, also a small operating system first booted when the device is turned on (so it has control over all the hardware), but UEFI is a 'juniors' level so it is very many extended functions, more user-friendly interface, works with the mouse instead of just using the keyboard like the BIOS the day before, even users can surf the web or backup the operating system from the UEFI interface .
And yet, if the BIOS is caught dead on the hardware on the mainboard, then UEFI can be loaded from anywhere, even on the hard drive or from some storage outside the LAN (provided the mainboard is designed to support). Want more? Most older BIOS cannot recognize hard disks with capacities larger than 2.2 TB. With HD players need to use a new series of 3TB drives, this is clearly a disaster! UEFI can even boot from the drive with a capacity of . zetabyte, a long number we can reach.
The day before the computer wanted to connect to the network, it had to go to the main operating system such as Windows, Mac, Linux, so the technicians who wanted to repair something complicated had to rummage their tools down to the machine. With UEFI, carriers can integrate network connectivity and remote debugging tools more conveniently, both for technicians and customers. Indeed, the advantages UEFI offers both end users and many manufacturers do not count.
New interface is more user-friendly, works with the mouse.
All seem very promising, but in the hardware manufacturing world, the most interesting feature is the secure boot. In the past, if a good day was boring with Windows and wanted to try a certain operating system, the steps were simple: Download & burn the installation disc of the new operating system. , memorize or note the instruction to install, restart the device, format the old Windows installation drive and install the new operating system on it. The risks of installing a strange operating system are created by users, but there is a problem that they often bring to the debt guarantee center right away, all because of the ease of the BIOS.
But with UEFI? Forget! Hardware manufacturers can configure UEFI to prevent users from installing strange operating systems on their hardware. However, UEFI is just a framework, manufacturers, whether hardware or software (operating systems) need cooperation from other firms to complete their UEFI version - one Complete hardware controls with the ability to support all types of hardware and boot up all operating systems.
The funny thing is that even if Apple, IBM . joined the game early, Microsoft is still hanging out, so the hardware manufacturers have to wait until now to popularize UEFI. But that is not enough, Microsoft insists on PC to install Windows 8 to support secureboot, or even more if the company can agree with OEM, the machines when sold are pre-installed Windows 8 & UEFI will . . cannot install the type any other operating system.
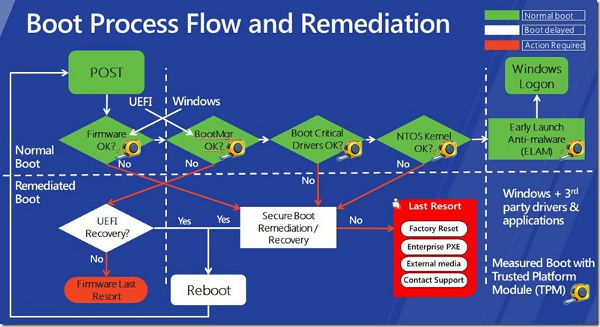
Secureboot constantly checks critical components such as kernel drivers when booting the operating system.
In fact, secureboot is not born to serve this business game. Its main purpose is to prevent the startup of unknown operating systems or operating systems, reducing the risk of being tracked and stolen for users. A chip on the mainboard will store the encrypted information of key components on the user's main operating system. If during the operating system boot, UEFI compares with the encryption information and detects that these components are strange components, or have been modified, it will stop the process of booting your machine. The problem with Linux is that, obviously, Linux is not malware or virus at all, but if its information is not included in the chip mentioned above, Linux is still not allowed to boot by UEFI.
The solution seems very simple: Save the official Linux Distro in it for UEFI to recognize. But in fact, in order to do this, we need a password to access that secureboot chip, but on Windows 8 machines (PC products, Windows 8 pre-installed laptops, pre-installed this operating system logo on it to for sale, this password is only known to Microsoft and the hardware manufacturer. The Linux products or the two companies agreed and proceeded to save the information to the secureboot chip, or to find devices without secureboot or even without UEFI to exist. The first way does not seem satisfactory, ask Microsoft? In your dream! The second way completely depends on whether the hardware vendors provide users with the option to turn on / off secureboot or not, because it is impossible to tell UEFI to go back to the BIOS.
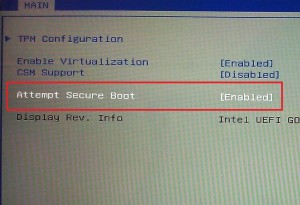
The most feasible 'detour' for Linux developers is working with the bootloader - this is the component that directly activates the loading of the operating system (not UEFI or BIOS) and resides on the hard drive. can be easily changed. As long as developers create a bootloader approved by Microsoft and affix ' secured ' labels there, the operating system that bootloader will activate will not be checked by secureboot.
Now the first person to do this is Matthew Garret, who convinced Microsoft to approve his bootloader name SHIM. Shim will soon support SUSE, Fedora and Ubuntu booting. The Linux associations are still trying to find a better way to put Linux on a computer instead of having to compete with Microsoft too much, but it seems that until now SHIM is still the only way.