How to use Canary Tokens to keep hackers from accessing your files
Are you worried about your personal files being stolen by hackers? Canary Tokens is a free and easy-to-use tool that you can quickly deploy to receive alerts when hackers open your files.
What are Canary Tokens?
Canary Tokens is a cybersecurity tool from Thinkst Canary that tracks hackers as they access your personal data. It works by embedding your file with a special tracking URL to notify you via email when it is opened. Similar to how a honeypot works, the idea is to place a tracker disguised as a regular file on your device. When the hacker opens the file, a hidden link opens, alerting you to the violation.
How to use Canary Tokens to protect your data
The article will show you how to embed the Canary Tokens tracking URL into the Windows folder. However, you can use Canary Tokens to protect all types of files and services, from Word and Excel documents to specific URLs, to online services like Azure and Microsoft SQL servers, etc. .
Let's start by visiting Canary Tokens.

When you visit the website, you will be greeted by the Canary Token generator. The generator requires you to set up three fields:
- The first is to choose the appropriate token for your file type.
- The second is for your email address.
- The last section is for anything you want to remind yourself of when the alert is triggered.
Because the article is embedding the token in a folder, the author has selected the Windows folder from the Select your token drop-down menu .
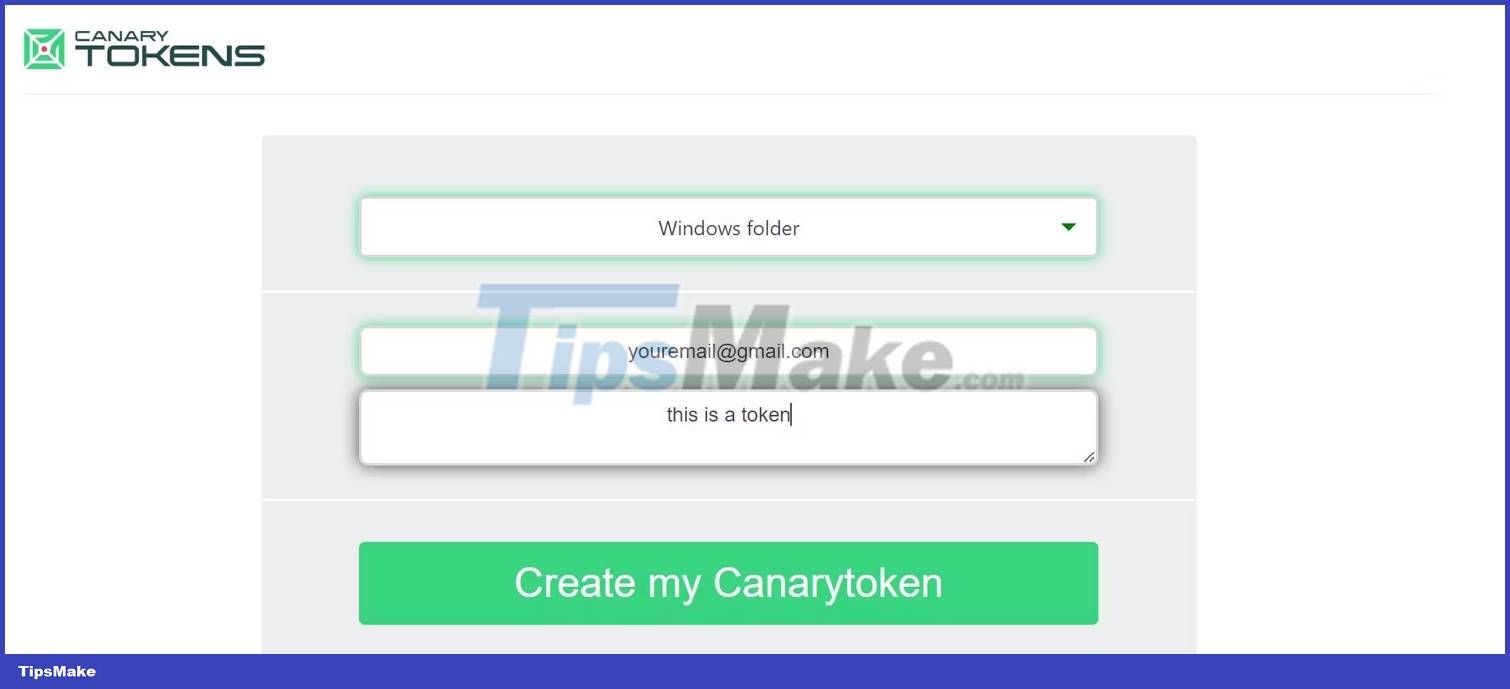
The author has also provided email to receive notifications and text notes to remind about the intended use of the token.
After you fill out the form, click Create my Canarytoken and download the ZIP file embedded with a special token.
Now, extract the ZIP file by right-clicking on the file and selecting Extract All , then enter the folder where you want to place the file. Ideally, it should be somewhere easy for hackers to find. For example, if you want the file on your desktop, you would enter C:UsersYourUserNameDesktop (remember to replace YourUserName). You can then add the file to the folder and rename it to a name that a potential hacker might want to open.
Now that our trap is set, let's try opening the folder and check if the warning has been triggered.
How to check if hackers have access to your files
Checking whether your special file has been opened is as simple as opening your email account (the one you linked previously) and checking the Canarytoken Mailer in your inbox.
Enabling email notifications on Chrome or your favorite web browser will help notify you immediately when the file is opened. You may also want to check your spam folder in case Canarytoken Mailer is identified as spam.
Token activation will notify you with an email that looks like this:
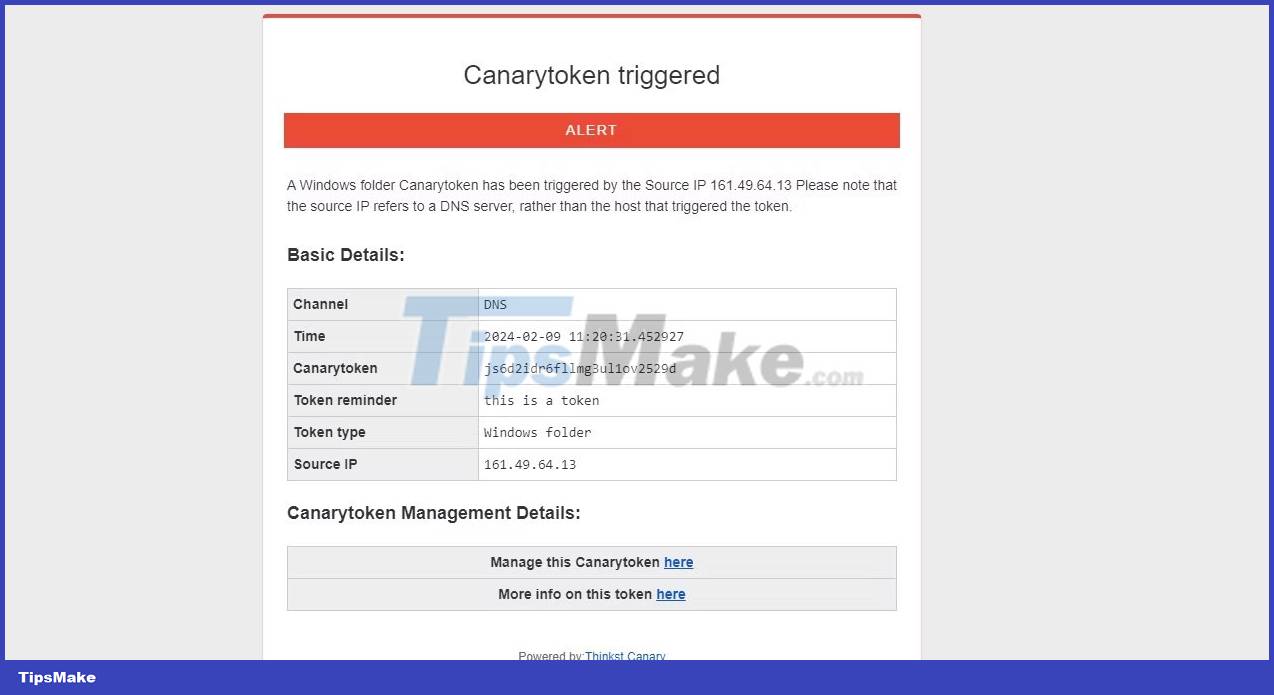
As you can see, it contains information such as date and time, text note reminder, and source IP, which can be used for various purposes. You can use an IP tracker to find the general location where your files are opened. Additionally, select More info on this token here to see the location of the problem.
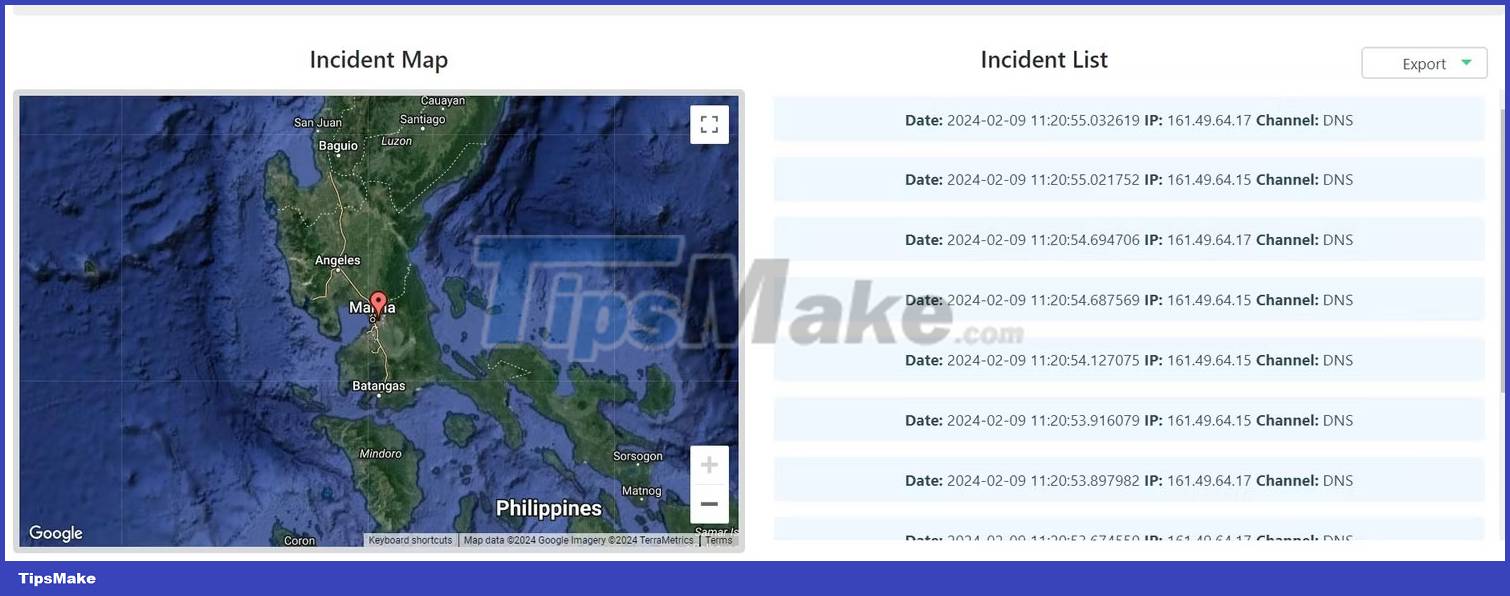
The location specificity that Canary Tokens provide will vary depending on how the file opener's ISP operates and whether they are using a VPN to protect their location data.