Here's how I hack 40 websites in 7 minutes
The following article is translated from the story of Georgios Konstantopoulos, electrical and computer student in Greece.
Last summer, I learned about information security and hacking. Last year, I learned a lot and continuously improved my hacking skills, learning how to 'make computers work the way others have never thought of'.
My experience is always limited to the simulated environment and I consider myself a white hat hacker, never dipping into someone else's story.But now, I will detail how I hacked the server containing 40 websites .
Note: Computer science knowledge is required to understand the technical details below.
A friend told me his website has an XSS vulnerability and wants me to see it. This is important, so I have to ask him to allow me to test the web application and the host server. The answer is yes.
From now on, I'll temporarily call my friend's website, http://example.com/
First, find as much information as possible about the opponent and try not to hit them.We started scanning, taking about 2 minutes.
$ nmap --top-ports 1000 -T4 -sC http://example.com
Nmap scan report for example.com {redacted}
Host is up (0.077s latency).
rDNS record for {redacted}: {redacted}
Not shown: 972 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| {redacted}
80/tcp open http
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Victim Site
139/tcp open netbios-ssn
443/tcp open https
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_{redacted}
445/tcp open microsoft-ds
5901/tcp open vnc-1
| vnc-info:
| Protocol version: 3.8
| Security types:
|_ VNC Authentication (2)
8080/tcp open http-proxy
|_http-title: 400 Bad Request
8081/tcp open blackice-icecap
As a result, many ports are open. Recognizing that FTP (port 21) and SMB (port 139/445) are open, we guess the server is used to host files and share files, and is also a webserver (port 80/443 and proxy 8080/8081). If the information just scanned is not enough, UDP scans and more than 1000 ports will be needed. The only port that we are allowed to interact without authentication is 80/443.
Without wasting time, I run gobuster https://github.com/OJ/gobuster to find out which files are interesting on the webserver, and also find the information manually.
$ gobuster -u http://example.com -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 100
/admin
/login
It turns out the path / admin is an admin tool for authenticated users to edit on the webserver. It needs login information but we don't have both username and password so we have to skip it. (Gobuster cannot find anything valuable).
So it's been 3 minutes in vain.
When I opened the website, I found it asking to login. We create an account by junk email, click on the confirmation link in the email and log in. The website redirects to the Profile page and we update the information above.
Seeing that the website looks customizable, I try to check for Unrestricted File Upload vulnerability (file download vulnerability). On the Terminal, I execute the code:
echo " " > exploit.phpecho " " > exploit.php
I tried downloading 'image' and finally the exploit.php file was uploaded. Of course it doesn't have a thumbnail, but it also means that my file has been uploaded somewhere.
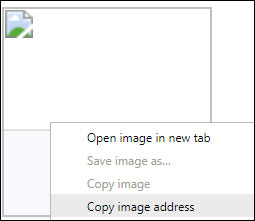 Get locations to tap
Get locations to tap
We think we will check the extension, replace it with extensions like .jpeg or .jpg to avoid executing remote code if an attacker loads the malicious code. We don't care about security, right?
`Copy image address` results in the following url being copied to our clipboard:
http://www.example.com/admin/ftp/objects/XXXXXXXXXXXX.php
So it looks like our webshell is ready.
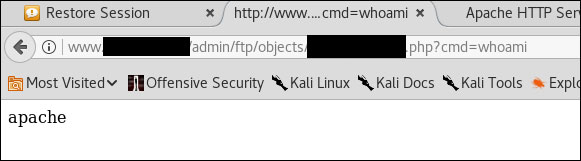
Webshell is ready to operate
Notice that the webserver runs the perl script, we get a reverse shell (the type of shell the target communicates against the attacker) on the buoy http://pentestmonkey.net/cheat-sheet/shells/reverse-shell- cheat-sheet then set IP / port and get very low access. (Sorry because this section has no photos).
5 minutes passed but only very low rights.
Surprisingly, the server not only hosts a website but also has 40 pages . Sadly, I didn't keep a detailed screenshot but the list is behind this:
$ ls /var/www
access.log site1/ site2/ site3/ {. the list goes on}
You got it. Access to all websites hosted here means I can read all the backend code of all sites. But I limit myself to the code of example.com page. Inside the cgi-admin / pages directory all perl scripts connect to MySQL database with root access. Information to log in is also available in text format. Temporarily assume the name and password are root: pwned42.
Certainly the server runs MariaDB so I have to read about this issue on GitHub https://github.com/dockerfile/mariadb/issues/3 before accessing the database. We then execute the code:
mysql -u root -p -h localhost victimdbname
Password: pwned42
And so we were in the database with root access.

'use databasename;' Allows us to access 35 databases, read and edit any content.
So after just 7 minutes, we had the right to read / edit the contents of 35 databases.
At this point, my conscience forced me to stop and announce what I found. The loss will be very large if an attacker is present, such as:
- Clean up content on all databases, as described here https://stackoverflow.com/questions/9497869/export-and-import-all-mysql-databases-at-one-time leads to data Data of 35 companies will leak out.
- Delete all 35 databases.
- Leave the back door and continue to access it with cronjob (doing repetitive tasks) as described here.http://blog.tobiasforkel.de/en/2015/03/19/setup-cron-job-for-apache-user/
It should be noted that the MySQL process runs under root. I try to run ! whoami to get root privileges but failed.
What could happen?
After reporting the results, I was allowed to dig deeper. Before trying to upgrade to root and cause further damage, I see if the current permissions can find any files.
At this point I remember the open SMB port, which means there must be a public folder that the user has to file somewhere. After a few times of listing, this is what appears in the / home / samba / secured directory .
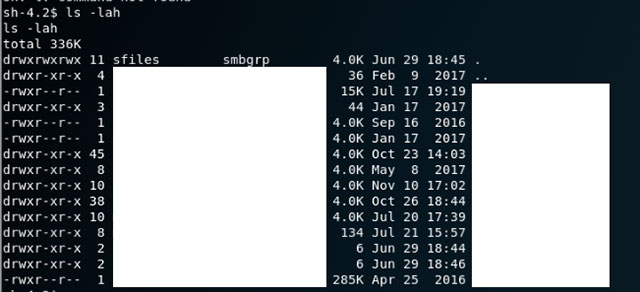
File of all companies
Within all of these directories, there are files of each user of each company, including the type of sensitive data such as:
- .Psd, .ai file (designers should know well)
- Cookies sqlite
- Bill
- Eboook
- Login information for SSIDS WiFi
With these things, an attacker can:
- Sit outside the company office but log on to the intranet and perform all kinds of attacks.
- Clean up the data and release it to the public.
- To see all the folders and realize the importance of the problem also takes a lot of time.
Decisive owl
After a few laps, I decided to catch the big fish, root access. I refer to the float page https://blog.g0tmi1k.com/2011/08/basic-linux-privilege-escalation/ and start looking for files.
Since I have used up a lot of techniques already, I can't seem to find much. Then I remembered. With the previous CTF (Capture the Flag) challenges, the OS is often patched but occasionally deliberately set up, giving you root privileges. People still patch.
Which Linux version is running on?
$ cat /etc/issue
CentOS Linux release 7.2.1511 (Core)
What about the kernel version?
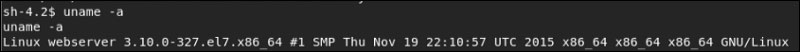
The Kernel version of the Linux server
Seems like an old kernel version. I found it on this blog http://davemacaulay.com/easily-test-dirty-cow-cve-2016-5195-vulnerability/ how to check if the kernel is vulnerable to the scenario below.
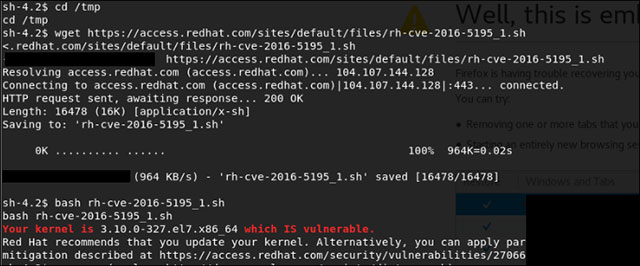
Check if the kernel is vulnerable
Then:
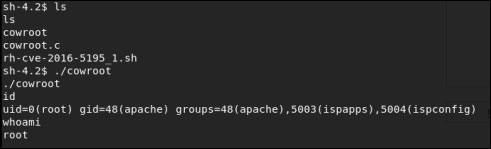
Account for root privileges
It is done. I immediately wrote an email detailing the steps along with the impact of each step I took and closing a very interesting night.
Summarizing this is what an attacker can do:
- Read and edit all files on the server
- Leave the back door
- Install and distribute malicious code on the server's internal network
- Install extortion code
- Use server to dig virtual money
- Use server as a proxy
- Use the server as a C2C server
- Put the server into the botnet
- Depending on your imagination .
The next day, my friend (contacted the server operator) said that the error when uploading the file was fixed.
Chung recalls, we found out:
- The web application has an Unrestricted File Upload vulnerability, which leads to low access
- Login information MySQL database, resulting in the right to read / write 35 databases
- Many sensitive files
- Finally, take advantage of the unpatched kernel to gain root access.
Some solutions proposed
Start with the file download error. Since the backend code of this web application is written in perl, but I do not know this language, there is no solution available. One suggestion is not to use perl, it's 2017 already.
Besides the file system, I encourage careful file permissions for users, according to the minimum rule of law. Then even users with low access rights cannot read.
Running all websites on a server is not a good idea. Sharing common credentials for all databases is not a good idea.
Finally patch everything. Just one order, with CentOS like this.
su -c 'yum update' Thank you for reading, sorry for the long post. I want to speak carefully because this is important.
See more:
- The most basic insights to becoming a Hacker - Part 1
- The journey halfway around the world finds back 200,000 dollars bitcoin
- Journey from unknown to becoming software engineer in San Francisco for 12 months
- To learn about SQL and databases, do not ignore these 23 online resources
You should read it
- ★ Hacker took control of the London Police Department website, posting 'unacceptable' content.
- ★ More than 1,300 phishing kits are being sold on the hacker forum
- ★ There has been hack Among Us and this is how you find out hacker
- ★ Top 28 Android tools and apps you should know (Part 2)
- ★ Learn about SQL Injection and how to prevent it