How to try to crack a password yourself to test its strength
The article tested 3 different passwords with an open source password cracking tool to find out which method really works when it comes to password security.
What is password cracking?
When you create an account with an online service, the provider typically encrypts your login information on their servers. This is done using an algorithm to create a 'hash,' a seemingly unique random string of letters and numbers for your password. Of course, it's not actually random, but a very specific string of characters that only your password could generate, but to the untrained eye, it looks like a jumbled mess.
It's much faster and easier to turn a word into a hash than to "decode" the hash back into a word. So when you set up a password, the service you're logging into will run your password through the hash and store the result on their servers.
If this password file is leaked, hackers will try to find out its contents by cracking the passwords. Since encrypting passwords is faster than decrypting them, hackers will set up a system that takes potential passwords as input, encrypts them using the same method as the server, and then compares the results to the password database.
If the hash of a potential password matches any entry in the database, the hacker knows that every attempt matches the potential password tried.
How to Crack Your Own Passwords Using HashCat
Let's try cracking some of the passwords this article has generated to see how easy it is. To do this, we'll use Hashcat, a free and open source password cracking tool that anyone can use.
For these tests, the example will crack the following passwords:
- 123456 : A classic password and cybersecurity nightmare, 123456 is . NordPass calculated that 3 million accounts used 123456 as their password, of which 1.2 million protected corporate-level accounts.
- Susan48! : A password that follows the patterns that most users would use to create secure passwords. This generally meets the criteria for basic password protection, but as we will explore later, it has some important weaknesses that can be exploited.
- t9^kJ$2q9a : A password generated using Bitwarden's tool. It is set to generate a 10 character long password with upper and lower case letters, symbols and numbers.
Now, let's encrypt the passwords using MD5. Here's how the passwords would look if they were in a saved password file:
- 123456 : e10adc3949ba59abbe56e057f20f883e
- Susan48! : df1ce7227606805745ee6cbc644ecbe4
- t9^kJ$2q9a : 450e4e0ad3ed8766cb2ba83081c0a625
Now, it's time to crack them.
Perform a simple jailbreak using Dictionary Attack method
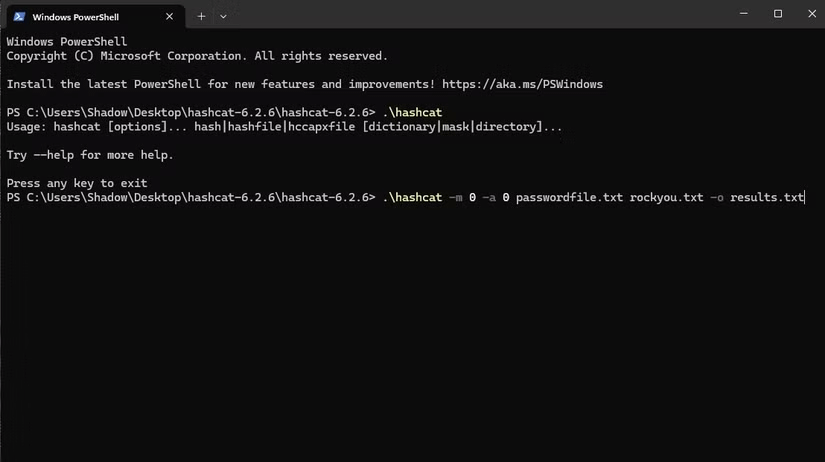
To start, let's perform a Dictionary Attack, one of the most common password attack methods. This is a simple attack where a hacker takes a list of potential passwords, asks Hashcat to convert them to MD5, and sees if any of them match the three entries above. For this test, let's use the file "rockyou.txt" as our dictionary, which was one of the largest password leaks in history.
To start cracking, the author of the article went to the Hashcat folder, right-clicked on an empty space and clicked Open in Terminal . Now that the Terminal was open and set to the Hashcat folder, invoked the Hashcat application with the following command:
.hashcat -m 0 -a 0 passwordfile.txt rockyou.txt -o results.txtHere is what the command does:
- .hashcat calls Hashcat.
- -m 0 : Specifies the type of encryption to use. In this case we will use MD5, listed as 0 in the Hashcat help documentation.
- -a 0 : Specifies the attack to perform. The Hashcat help documentation lists Dictionary Attack as 0, so we call that here.
- passwordfile.txt rockyou.txt : The first file contains the 3 encrypted passwords we set up earlier. The second file is the entire rockyou password database.
- -o results.txt : This variable determines where we put the results. In the command, it puts the cracked passwords into a TXT file named "results".
Despite the large size of rockyou, Hashcat processed all of them in 6 seconds. In the resulting file, Hashcat says it cracked the password 123456, but the passwords Susan and Bitwarden were not cracked. This is because 123456 was used by someone else in the rockyou.txt file, but no one else used the passwords Susan or Bitwarden, meaning they were secure enough to survive this attack.
How to keep your account safe from password hacking
The main factors that prevent the Bitwarden password from being cracked are its length (10 characters) and unpredictability. So when creating a password, try to make it as long as possible and spread out symbols, numbers, and uppercase letters evenly throughout the password. This prevents hackers from using masks to predict the location of each element and makes it much harder for them to crack.
You're probably familiar with the old password adages like "use a character array" and "make it as long as possible." Hopefully, you know why people recommend these helpful tips—they're the key difference between an easy-to-crack password and a secure one.
You should read it
- ★ How to Remove the Password from a Zip File Without Knowing the Password
- ★ Break hotspot password on iOS within 1 minute
- ★ How to crack Windows 10 password, how to break password on Windows 10
- ★ How to crack Winrar Password - Find the Winrar compressed file password quickly and effectively
- ★ List of easy passwords to crack in 2023, in less than a second