How to remove ransomware .Mogera Virus File
. Mogera encrypts files in your computer, but that may not be the only damage that this ransomware is causing you. Ransomware .Mogera Virus File may still be hiding somewhere on the PC.
Learn about .Mogera Virus File and how to remove this dangerous ransomware
- About .Mogera Virus File
- How ransomware works
- Summary about .Mogera Virus File
- How to remove ransomware .Mogera Virus File
- 1. Prepare
- 2. Task Manager
- 3. IP related to .Mogera
- 4. Disable Startup programs
- 5. Registry Editor
- 6. Delete potentially malicious data .Mogera
- 7. Decode
About .Mogera Virus File
When the system is completely encrypted, the .Mogera virus leaves the file _readme.txt with instructions for the user:
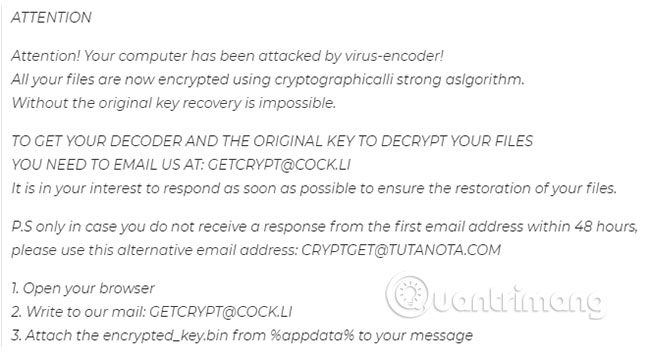
If you want to learn more about the recently released virus program called .Mogera, the following information can give you some basic and useful knowledge related to this malware. This malicious software belongs to the ransomware class that encrypts the file. This type of malware carries the ability to use data encryption methods through which ransomware such as .Mogera, .Rectot, .Ferosas can hold the documents of the targeted users.
Victims will not be able to view these data on their computers anymore. As soon as this ransomware completes the encryption process, a ransom notification is created on the computer screen of the targeted user, informing the person that their document has been encrypted and they must pay ransom to recover them.
Cyber criminals often add detailed instructions in the ransom message, forcing the victim to comply with the ransom request. Attached to the ransom message is always a threat to delete the data if the victim does not make a payment. If unfortunately become a victim of .Mogera, continue reading the next section of the article.
How ransomware works
To get started, consider the fact that, if you have a ransomware on your computer, that means you don't have to deal with a normal computer virus. The data encryption virus you are processing only focuses on file encryption. This means that the PC does not suffer any real damage. The data encryption code makes document files inaccessible, but does not cause any harm to the data files themselves. Being aware of this aspect in the way ransomware. Mogera Virus File works is very important. It helps us understand this type of malware, as well as the reason why detection and processing is quite difficult.
Because this PC virus doesn't really harm, both target victims and antivirus programs find it hard to detect. Sadly, in most attacks, the virus is not detected until it locks files on the victim's computer. The fact is, in most cases, there are almost no symptoms, showing signs of a ransomware attack.
However, you should be wary of abnormalities with RAM and processor in Task Manager as well as other strange system behavior, as this may be a potential warning sign of being infected with ransomware. Some lucky users can detect ransomware infections, before all files are locked and thus prevent data encryption. Normally, if you notice anything unusual, it is best to turn off the PC and ask a review specialist.
Summary about .Mogera Virus File
Name .Mogera High Risk Ransomware Type (Ransomware .Mogera encrypts all types of files) Symptoms Ransomware. Mogera is hard to detect. In addition to using more and more RAM and CPU, there are almost no other obvious signs. Distribution method Most of the time, this trojan is distributed via spam emails and social network messages, malicious ads, pirated software downloads, unknown sources, suspicious torrents and methods. Other similar.How to remove ransomware .Mogera Virus File
1. Prepare
Note : Before continuing, you should bookmark this page or open it on another device such as a smartphone or PC. Some steps may require you to exit the browser on this PC.
2. Task Manager
Press Ctrl + Shift + Esc to enter Task Manager. Go to the tab labeled Processes (or Details on Win 8/10). Carefully review the list of processes that are currently running on the PC.
If any of them seems shady, consumes too much RAM / CPU or has a strange description or no description, right-click on the process, select Open File Location and delete everything. over there.
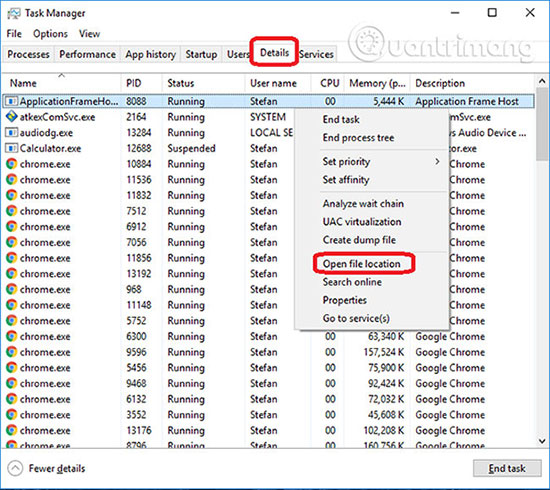
Also, even if you don't delete the files, be sure to stop the suspicious process by right-clicking on the file and selecting End Process.
3. IP related to .Mogera
Access C: windowssystem32driversetchosts . Open the server file with notepad.
Find the location of Localhost and see the information below.
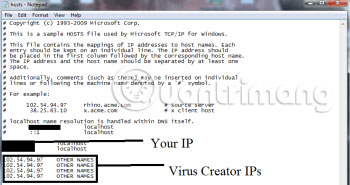
If you see any IP addresses there (below Localhost), check them carefully because they may come from .Mogera (if not sure, leave comments in the comment section below for help) .
4. Disable Startup programs
Open the Start menu and type msconfig.
Click on the first search result. In the next window, go to the Startup tab . If you're on Windows 10, you'll go to the Startup section of the task manager, as shown in the image below:
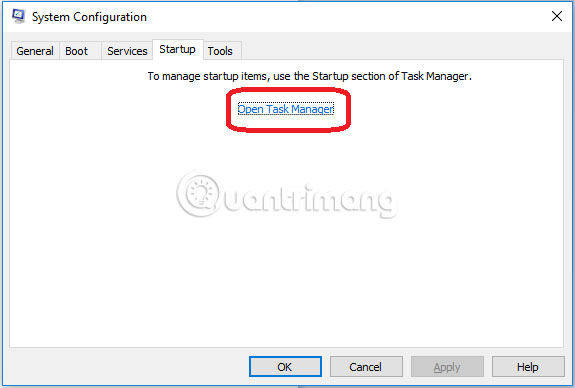
If you see any shady looking entries in the list (unknown manufacturers or manufacturer names seem suspicious), there is a possibility that there is a connection between them and .Mogera, turn off the program and select OK.
5. Registry Editor
Press Windows + R key combination and in the results window, enter regedit.
Now press Ctrl + F and enter the name of the virus.
Delete everything found. If you are not sure whether to delete something, do not hesitate to leave a comment in the comment section below. Remember that if you delete something wrong, you can cause problems for your PC.
6. Delete potentially malicious data .Mogera
Enter each of the following locations in the Windows search box and press Enter to open these locations:
- % AppData%
- % LocalAppData%
- % ProgramData%
- % WinDir%
- % Temp%
Delete everything you see in Temp associated with ransomware. With other folders, organize their content by date and delete only the most recent items. As mentioned above, if you are not sure about something, leave a comment in the comment section.
7. Decode
The previous steps are all aimed at removing ransomware .Mogera from your PC. However, in order to regain access to the files, you will also need to decrypt or restore them.TipsMake.com has a separate article with detailed instructions on what you need to do to unlock your data.
Hope you are succesful.
You should read it
- ★ No anti-virus software can detect this extremely dangerous new Ransomware on Android
- ★ What is Ransomware CryptoWall 4.0? How to clean up Ransomware CryptoWall 4.0?
- ★ Ransomware can encrypt cloud data
- ★ What is the Wannacry Ransomware? How to prevent Wanna Cry Ransomware?
- ★ How to get rid of root virus * .OSIRIS - Ransomware Locky?