How Linux stores and manages user passwords
Are you wondering how Linux effectively manages a multi-user environment? In this article, TipsMake.com will explain how Linux stores and manages user passwords and login information.
Discover the file / etc / passwd
When the user enters a username and password, Linux will check the password entered for entries in some files in the '/ etc' directory.
The / etc / passwd file is one of the most important files to store user information.
The nearest item in this file corresponds to the user 'carbon'. There are multiple information fields separated by colons.
carbon: The name of the user this item corresponds to.x: Indicates that a password exists for the user. However, the password is stored in the file '/ etc / shadow'. If instead of x it displays the icon ! , this indicates that the password does not exist.1000: User ID of this user.1000: Group ID of the group that contains this user.carbon, , ,: Indicates multiple information fields including full name and phone number. Here, no phone number is provided./home/carbon: The location of the home directory assigned to this user./bin/bash: The default shell is assigned to this user.
Please create another user for the stored phone number. The user 'pluto' is added to the system with the adduser command.
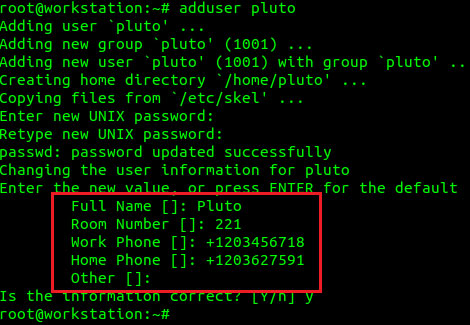
Looking back at the etc / passwd file, once again, we can see the complete information for the user 'pluto'.
Whenever the user is created, the default home directory and shell values will be specified in /etc/adduser.conf.
The User ID for the created user starts from 1000 and runs up to 59999.
'Carbon' users can view the entries in / etc / passwd file only by using the cat command.
Only the root user can write to the file. Other users can only read the file. Because everyone can read this file, storing passwords here is not ideal. Instead, the password is stored in another file called '/ etc / shadow'.
Explore the file / etc / shadow
Now, let's see if the password is stored for users 'carbon' and 'pluto' in the file '/ etc / shadow'.
Looking at the file permissions of '/ etc / shadow' , we can see that only root users can read and write to the file. Also, only members of the 'shadow' group can read the file. In fact, the 'shadow' group is empty but is syntactically required for this file.
Logging in as root, we can see the last 10 lines of '/ etc / shadow'. Each entry in '/ etc / passwd' has a corresponding entry in this file. The format will be as follows:
pluto:$6$JvWfZ9u.:18283:0:99999:7::: Also in this file, every entry has multiple fields separated by colons:
pluto: The name of the user this item corresponds to.$6$JvWfZ9u.$yGFIqOJ.: The user hash password is stored along with information about the hash algorithm used. Additionally, a salt value is used along with the plaintext password to generate the hash password.
{ plaintext password, salt} -> hashed password The $ symbol is used to separate 3 fields.
$6 $JvWfZ9u. $yGFIqOJ. $6: Hash algorithm used. Below is a list of potential hash algorithms.$1: MD5$2a: Blowfish$2y: Eksblowfish$5: SHA-256$6: SHA-512
$JvWfZ9u.: Salt value.$yGFIqOJ.: Password is hashed.
The resulting hash value is stored as an encrypted password for the user. Salt values are unique to each user. Even if two users have the same plaintext password, using a single salt will produce a unique hash value.
Following are the remaining fields in this section,
18283: Indicates the number of days since January 1, 1970, the password was last changed0: This field is used to indicate the number of days after which the password may be changed. A value of 0 means that the password can be changed at any time.99999: This field indicates the number of days after which the password must be changed. The value 99999 indicates how long the user can keep the password.7: If the password is set to expire, these fields indicate the number of days to alert the user of the password expiration.:::Three more fields are also part of this section, although they are empty here. The first number indicates the number of days to wait after the password expires, after which the account will be disabled. The second number indicates the number of days since January 1, 1970, the account has been disabled. The third field is reserved for future use. Empty fields indicate that this user's current password has not yet expired and is not set to expire soon.
The last 7 fields relate to password validity, collectively known as ' Information Aging Policy' information holdings.
The default values corresponding to the 'Password Aging Policy' are specified in the file '/etc/login.defs'. These values can be changed for the user with the change command.
What about group information?
User information and passwords are stored in '/ etc / passwd' and '/ etc / shadow' files. Similarly, group information is stored in the file '/ etc / group'.
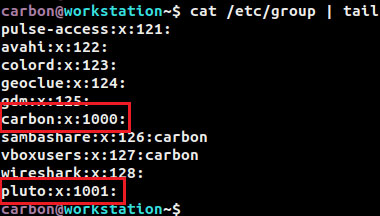
Highlight above are the groups that belong to the users 'carbon' and 'pluto'. When a user is created in Linux, that user is immediately assigned to a group with the same name as the username.
Members of a group can also share group passwords for activities related to that group. The value of x indicates that the group's password information will be in the file '/ etc / gshadow'.
However, access to '/ etc / gshadow' is restricted to the root user.
Root users can view the entries of '/ etc / gshadow' , similar to '/ etc / shadow'. Looking at the entry of the 'carbon' group, we can see that the second field has value ! , indicates that the password does not exist for this group.
When the user wants to log in, the hash of the entered password is found using that user's salt value in '/ etc / shadow'. It is then compared to the stored hash. If the values match, the user is granted access.
You should read it
- ★ How to manage passwords using the Bitwarden utility
- ★ What is the smartest and safest way to store passwords?
- ★ The last 9 years Firefox has not protected user passwords carefully
- ★ Top 10 faces with the worst passwords in 2018: Second US Defense Ministry
- ★ Americans are banned from using password 1234 to ensure safety