Google Chrome uses Windows 10's new security feature to combat exploits
Windows 10 supports Intel's Control-Flow Enforcement (CET) technology called Hardware-enforced Stack Protection.
Hardware-enforced Stack Protection uses the Intel CET chipset security extension to protect applications from popular vulnerability exploitation techniques such as Return-Oriented Programming (Return-Oriented Programming -). ROP) and Object-Oriented Programming (OOP).
An attacker bounty uses such computer security exploiting techniques to hijack the program's intended flow of control in order to execute malicious code through the browser. Windows 10's Hardware-enforced Stack Protection block these attacks when it detects that the natural flow of a modified application is detected.
Google Chrome is not the first Chromium-based web browser to support the Hardware-enforced Stack Protection feature. In February, Johnathan Norman, Microsoft Edge vulnerability research lead Microsoft Edge 90 added support for Intel CET functionality.
This security feature will most likely be applied to Chromium browsers other than Google Chrome and Microsoft Edge, including Brave and Opera. Furthermore, Mozilla is also considering supporting Intel CET for its Firefox web browser. However, no new information has been released since the company announced this a year ago.
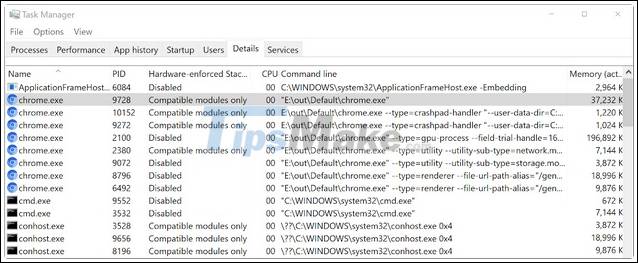
Windows 10 users with a CET-compatible CPU (Intel 11th generation or AMD Zen 3 Ryzen) can check if the browser process is using this security feature using Task Manager.

To do that, open Task Manager, click on the Details tab and right-click on the column header, then check the Hardware-enforced Stack Protection option. Once enabled, a newly added column will show Intel CET-enabled processes.
You should read it
- How to Become a Full Stack Programmer
- Stack Overflow hits the hacker face, no significant damage is recorded
- Chrome 73 launches with hardware media key, PWAs and Dark Mode support on Mac
- How to protect your Google account with Password Alert utility
- Google Chrome is now 23% faster, have you tried it?
- To enable Hardware Acceleration in Chrome, Firefox
 Windows users need to update this software immediately
Windows users need to update this software immediately Warning: This seemingly harmless message contains malware that threatens millions of Android users
Warning: This seemingly harmless message contains malware that threatens millions of Android users 5 common password-setting errors should be avoided
5 common password-setting errors should be avoided Warning of zero-day vulnerabilities in window manager on PC
Warning of zero-day vulnerabilities in window manager on PC What is Adaptive Security?
What is Adaptive Security? How to use Google Authenticator on a Windows PC
How to use Google Authenticator on a Windows PC