What is Volumetric DDoS Attack?
These DDoS attacks attempt to consume bandwidth in the target network / service or between the target network / service and the rest of the Internet.
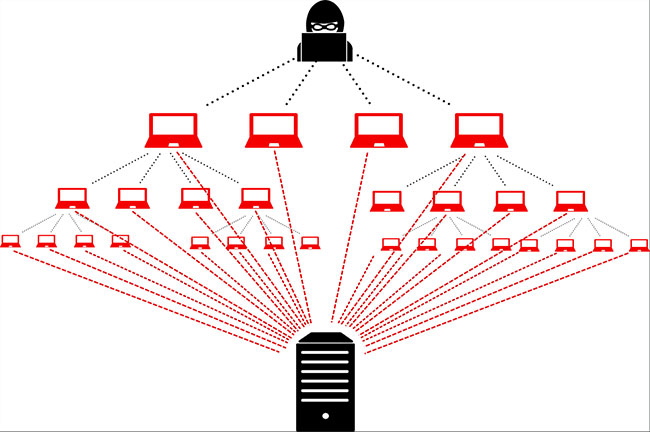
Volumetric DDoS Attack types
Volumetric DDoS Attack attacks are typically performed against a specific target, usually critical service provider (SP) services or business customers.
Highly skilled attackers tend to combine Volumetric DDoS Attack with Application Layer Attack to conceal more concentrated application-level attacks that cause real damage. the.
These types of DDoS attacks take advantage of vulnerable services, such as memcached, NTP, DNS and SSDP, and launch spoofed queries, flood the destination with large reply packets. , filling links and, in many cases, the target network infrastructure going down.
Volumetric DDoS Attack types include ICMP Flood, IP / ICMP Fragmentation, IPSec Flood, UDP Flood, and Reflection Amplification Attack.
Signs of Volumetric DDoS Attack
Such DDoS attacks typically have very high bandwidths (up to 100Gb + or even exceed multiple Terabits per second), becoming immediately apparent to both the target and the provider of the upstream connection. For this reason, attackers have learned to actively monitor the results of their attacks and often randomize attack parameters as soon as the defender can intercept or restrict the current attack vector. Using DDoS mitigation tools.
For the detection of Volumetric DDoS Attack attacks, Flow Telemetry (NetFlow, IPFIX, sFlow, etc.) analysis has become the industry standard. Flow Telemetry is typically performed using dedicated flow analysis tools (usually centrally located), remotely processing outflow from routers and switches, activating appropriate defensive measures. according to the classification of the attack.
Why is Volumetric DDoS Attack dangerous?
While Volumetric DDoS Attack is primarily focused on causing congestion, they can also be a sign of an ulterior motive, masking more complex DDoS attacks. In such cases, attackers can try to cause as much disruption and distraction as possible, including monitoring and quickly altering their attacks to evade. Avoid static minimization techniques.
These types of DDoS attacks are known as DDoS "Trojan Horse" and can be aimed at disabling the firewall or intrusion prevention system, allowing attackers to enter the network, install malware. and ultimately data theft.
How to mitigate and prevent Volumetric DDoS Attack
Mitigating and Preventing Volumetric DDoS Attack requires DDoS protection technologies, such as Remotely-triggered Blackholing (RTBH) and Source-based Remotely-triggered Blackholing (S / RTBH), proven to be very effective when used in a way that is appropriate for the situation.
The BGP feature, FlowSpec (short for "flow specification"), has been shown to be extremely effective when combined with security-focused Flow Telemetry analysis tools. Combining Flow Telemetry analysis with FlowSpec enables automatic detection and analysis of attacks, helping to mitigate Volumetric Attack attacks. The following steps are recommended, especially in the context of network expansion and the adoption of the Internet of Things (IoT):
Uses Flow Telemetry analysis, complemented with behavioral analysis for detecting anomalies and DDoS attacks. By focusing on understanding what is considered normal, the process of identifying the unusual becomes easier.
When detecting a DDoS Volumetric DDoS Attack, use FlowSpec to automatically enable network-based mitigation, to block attacks at network edges.