What is Office 365 Attack Simulator? How to use it?
If you are using Office 365 Threat Intelligence, you can set up your account to run simulated real-time phishing attacks on the corporate network. It helps you prepare for future attacks. You can train your employees to identify such attacks using Office 365 Attack Simulator. This article will introduce some methods to simulate phishing attacks.
The types of attacks you can simulate using Office 365 Attack Simulator include the following types.
- Spear-Phishing Attack
- Password Spray Attack
- Brute Force Password Attack
You can access Threat Management's Attack Simulator in the Security and Compliance Center . If it is not available there, it is likely that you have not installed it.
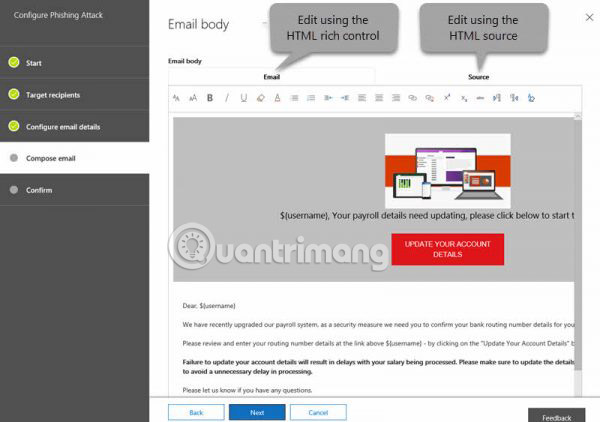
Remember the following:
- In many cases, older subscriptions will not automatically include Office 365 Threat Intelligence. It must be purchased as a separate add-on.
- If you are using a custom mail server instead of the regular Exchange Online , the emulator will not work.
- The account you use to run the attack must use multifactor authentication in Office 365.
- You need to login as a global administrator (global) to launch the attack.
Attack Simulator for Office 365
You need to be creative and think like a hacker when doing proper attack simulation. One of the phishing attacks is spear phishing attacks. In general, people who want to test spear phishing should research a bit before attacking and use a display name that looks familiar and reliable. Such attacks are mainly done to collect user credentials.
How to perform phishing attacks using Attack Simulator Office 365
The method of performing phishing attacks using Attack Simulator Office 365 depends on the type of attack you want to perform. However, the user interface is easy to understand, and so it is easy to add attack simulation.
- Start with Threat Management> Attack Simulator .
- Naming the project with a meaningful phrase will help you later, when processing data.
- If you want to use an existing template, you can do so by clicking Use Template .
- In the box below the Name section , select the email template you want to send to the target recipient.
- Click Next.
- In this screen, specify the target recipient; It can be an individual or a group
- Click Next.
- The third screen allows you to configure email details; This is the place to specify display names, email IDs, phishing login URLs, custom landing page URLs, and email topics.
- Click Finish to launch the spear phishing attack.
There are several other types of attacks available in Office 365 Attack Simulator, such as Password-Spray and Brute-Force attacks. You can learn them simply by adding or importing one or more common passwords, and see if the network has a chance to be hacked by hackers.
Simulation attacks will help you train your employees about different types of Phishing attacks. You can also use the data later to find other things in your office.
If you have any questions about Attack Simulator in Office 365, please leave a comment in the comment section below! Good luck!
See more:
- Compare Microsoft Office 2016, Office 365 and Office Online
- How to identify phishing emails
- 4 security warnings you should not "ignore"
You should read it
- ★ Hacker cracked a password of 16 characters in less than 60 minutes
- ★ What is IPFS Phishing attack? How to avoid?
- ★ What is 51% attack? How does 51% attack work?
- ★ Learn about the Adversary-in-the-Middle phishing attack method
- ★ Warning the emergence of ransomware DDoS attack, the scale can be up to 800Gbps