Detecting SharkBot malware hiding in anti-virus applications on Google Play
SharkBot banking malware has infiltrated the Google Play Store, the official Android app store, masquerading as anti-virus software with the ability to clean the system.
While this malicious app is not very popular, its presence on the Play Store shows that bad actors still find a way to bypass Google's automated defenses. Up to this point, this application is still available on the Google Play Store.

The application contains malicious code SharkBot

Application developer details
NCC Group researchers discovered the existence of SharkBot on the Google Play Store. Recently, NCC Group published a detailed technical analysis article about this malware.
What can SharkBot do?
SharkBot malware was first discovered by Cleafy in October 2021. Its most important feature, which sets it apart from other banking trojans, is money transfer via Automated Funds Transfer System (ATS). This is done by it by simulating taps, clicks and button presses on compromised devices.
The NCC says the money transfer feature is still available in the latest version of SharkBot but is only used in case of advanced attacks.
Currently, the four main functions in the latest version of SharkBot are:
- Injections (overley attack): SharkBot can steal login information by displaying web content (WebView) with a phishing login page as soon as it detects that the official banking application is open.
- Keylogging: SharkBot can steal credentials by logging accessibility events (related to text field changes and buttons being clicked) and sending these logs to a command and control server (C2).
- Block SMS: SharkBot can block/hide SMS messages (steal OTP codes without the user's knowledge).
- Remote Control/ATS: SharkBot can take full control of Android device and control it remotely (via Accessibility Services).
To do the above, SharkBot abuses the Accessibility privilege on Android and then grants it more permissions if needed.
In this way, SharkBot can detect when the user opens the banking application then execute the appropriate website injection and steal the user's information.
In addition, SharkBot can also receive commands from the C2 server to perform other actions as follows:
- Send SMS to a phone number.
- Change SMS manager.
- Download files from a specified URL.
- Get the updated configuration file.
- Uninstall the app from the device.
- Turn off battery optimization.
- Display overlay for phishing.
- Activate or deactivate the ATS.
- Closes a specific application (such as an anti-virus tool) when the user tries to open it.
Reply to notifications
One of the notable differences between SharkBot and other Android banking trojans is the use of relatively new components to take advantage of the "Direct reply" feature for notifications.
SharkBot can intercept new messages and respond to them with incoming messages directly from the C2 server.
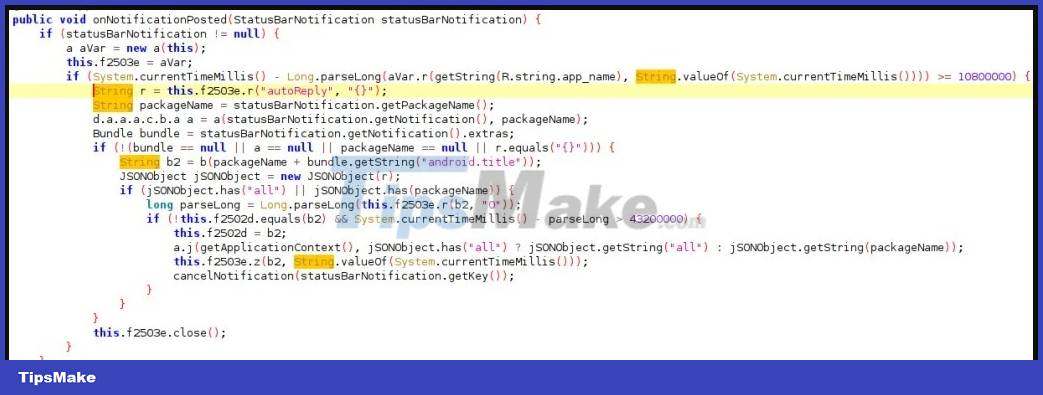
The source code of the auto-reply to notifications feature
NCC notes that SharkBot uses this feature to drop feature-rich payloads onto the compromised device via a shortened Bit.ly URL.
Initially, the rogue antivirus will only contain a reduced version of SharkBot to reduce the risk of detection and bypass the automatic defenses of the Google Play Store. Then, through the "Direct reply" feature, the official version of SharkBot with full features including ATS will be downloaded and installed.
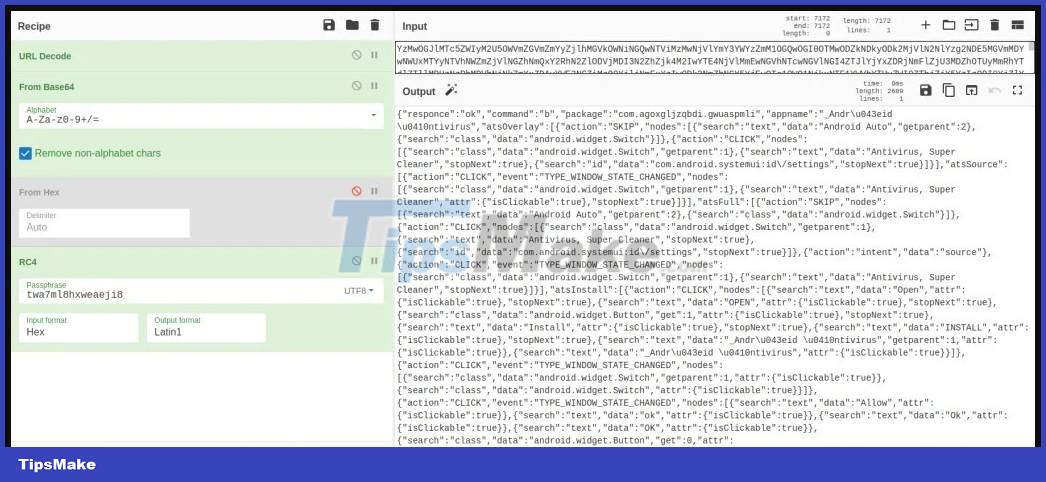
Decrypt the additional malicious download command sent from the C2 server
SharkBot's C2 server is based on a DGA (domain generation algorithm) so it becomes much more difficult to detect and block command-level domains for SharkBot.
To protect yourself against dangerous trojans like SharkBot, you should never completely trust apps on the Google Play Store. Install as few apps as possible on your device. In other words, only install applications that you feel are necessary for life and work.
You should read it
- ★ Detecting new malicious code capable of 'evading' most anti-virus software
- ★ Thousands of images on Google are infected with malicious code
- ★ Bkav software is mistakenly recognized as malicious code
- ★ Why shouldn't there be more than one antivirus on a Windows PC?
- ★ Malware Judy attacked more than 36.5 million Android phones