Basic technical details about the Internet
Introduce
The Internet uses a set of network protocols called TCP / IP. This article we want to describe to you the standard protocols (Standard) and applications that have been developed to support these protocols. These protocols provide a standard method for transferring messages. They provide formats for messages and handle in the event of a transmission failure. These protocols are independent of the network hardware, which means it allows communication between different networks with different hardware as long as they use the same type of protocol. The diagram below provides a classification chart of the protocols.
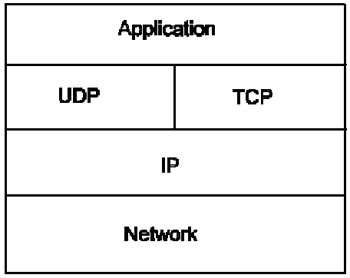
TCP / IP ( Transmission Control Protocol / Internet Protocol )
TCP / IP is used to easily communicate within a network including many different hardware. Information transmitted is divided into packets that are usually between 1-1500 characters to avoid the monopoly of a network. TCP is a transport level protocol that allows a process on one computer to send data to a processing on another computer. It is a connection-oriented protocol, meaning that there must be a path set up between two computers. IP gives a chart, the format of the data that exists during the transmission of the network and performs unconnected distribution. The disconnected distribution requires each chart to include the source address and destination address and each chart is treated separately. TCP retrieves information and divides it into several small pieces called packages, then numbers the packets and sends them.
On the receiving side, the packages are collected and rearranged to be in the correct order. If a data loss occurs, the receiving side will ask the machine to send the playback. The packet sent is included in it as a checksum, which is used to check for errors that may occur during data transmission. If the machine side finds an error when calculating and comparing checksum. It will dispose of this packet and ask the transmitter to play back. When everything is fully captured, the data will be reflected in the appropriate application (eg, e-mail).
UDP: User Datagram Protocol
UDP is simpler than TCP. Their basic concepts are the same except that UDP does not involve lost packets or keep their order. It is used for short messages. If it does not receive an answer, it will resend the request for retransmission of the entire data. This type of transport protocol is called a connectionless protocol.
Internet Addressing
All computers on the Internet must have a separate network address to be able to communicate effectively with other computers. The addressing method used within the Internet is a 32-bit address segmented according to a hierarchical structure. The IP address consists of 4 numbers smaller than 256, separated by dots (#. #. #. #). At the lowest level, computers communicate with other computers using a hardware address (on LANs, this is called a MAC address (Medium Access Control)). However, computer users handle at higher and more abstract levels to help visualization and computer recognition networks. The first level is the computer's IP address (eg 131.136.196.2) and the second level is the level of human readability from this address (eg manitou.cse.dnd.ca). This way of addressing is generally not used. ARP (Address Resolution Protocol) can be used by computer to analyze IP addresses into corresponding hardware addresses.
Connection types and connectors
There are two types of computers connected to the Internet: servers and clients. Servers (also known as servers) can be understood as an informant. Included in it are resources and data available to other machines on the network that can be accessed and used. The second type connected to the Internet is the client (also known as the client), which is interpreted as a person taking information. Clients will access the network and get resources and data placed on the server that will not provide any resources to the server.
Both servers and clients can be connected to the Internet with different methods, these different methods offer different communication capabilities depending on the overload of the network.
Connecting Direct : a computer directly connected to the Internet via a network interface will allow users to get the highest functionality. Each computer connected in this way must have a necessary Internet address. This type of connection is also the most expensive type.
Serial Connection : This type of connection can be either SLIP (Serial Line Internet Protocol) or PPP (Point to Point Protocol). Both of these methods produce the same services on a serial modem line (serial). Since this connection provides full TCP / IP and ICMP functionality, each computer configured in this case requires its own Internet address. This type of connection is on demand service, at lower speeds, so reducing the load and having the Internet vulnerability remaining when the connection is 'live'.
An important point of network security inspectors is to remember that most TCP dial-up connections, both SLIP and PPP, assign an IP address to a dynamically connected device. This means that, when a dial-up system arrives at an ISP (Internet Service Provider), the ISP will assign it an address at that point. It also means that dial-up addresses can change once or many times when the system is connected. This can cause some serious problems for security vendors when they are trying to track the access behind the firewall and router to write specific IP addresses.
Host access connection : the most restrictive type of network access is the user account on a host directly connected to the Internet. The user will then use an end device to access that host using a standard serial connection. This type of connection is simple in access.
Connect Sneaker-Net : this is an extremely simple connection, it has since the computers do not have an electrical connection. However, it is the safest type because hackers will not be able to directly access users' computers. Here, if information and programs are required on the computer, they must be transformed from a computer connected to a user's computer through a magnetic or manual environment.
All computers with direct connections, SLIP, and PPP must have their own IP addresses and security members must have knowledge of the vulnerabilities associated with these connections. With communication channels, it works in both ways: having users access to the Internet from which the Internet also has access to this user. Therefore, computers must be protected and ensure the Internet must also have a limited access.
In order to connect to different subnets, necessary hardware devices such as Repeater, Modem, Bridge, Router, Getway, Packet fillter, Firewall, Cyberwall . will be presented to you in detail. This hardware in the following article, invite you to read.
Pham Van Linh
Email: vanlinh@quantrimang.com
 HD DVD compared with Blu-ray
HD DVD compared with Blu-ray Handling unusual computer errors
Handling unusual computer errors Plus! Live - New vitality for Windows Live Messenger
Plus! Live - New vitality for Windows Live Messenger 'Monster' computers
'Monster' computers Top 10 webmail services today
Top 10 webmail services today Quantum technology will make data encryption more secure
Quantum technology will make data encryption more secure