Malware counterpart design (part 2)
Malware reconciliation design (part 1)
Analyze a real malware
 Through part one of this series, we have prepared some background and tools for later analysis. In this part 2, we will be exposed to a very interesting new material: real malware analysis.
Through part one of this series, we have prepared some background and tools for later analysis. In this part 2, we will be exposed to a very interesting new material: real malware analysis.
In the previous section we ended with the question of whether your downloaded malware was shown with the symbol of winzip or winrar. Why is this question? In the past, there was a case where a student used trojans to attack his teacher's computer. The student camouflaged the trojan with a familiar icon like winzip, and the teacher caught his trap. The procedure is quite simple, certainly not able to bypass IT experts. But for those who are not as knowledgeable about security as most of us, it's not surprising to catch a trap.
Real or fake?
As mentioned above, we can't be sure whether the downloaded malware is really a winzip file. One way to check is to double click on it to open it with the Hex editor as shown in the figure below.

Figure 1
As you can see, the actual malware is represented by the winzip icon, but not by the class as in winrar installed on the VMware image. Before opening the file in the Hex editor, you must pay attention to the following important points. File formats like winzip, winrar, or even PE format all have their own byte symbols. We can recognize them by byte level and view them easily via the Hex editor. That's why we have to open the file in Hex. The editor allows you to search for specific byte sequences in the file itself. It will tell you whether the downloaded malware as shown in the above illustration is really a winzip file. You don't need to worry about whether or not I accidentally caused this malware to be effective. Simply because in the Hex editor, you can only view the contents without being able to activate the executable file.
Bit or byte
You can see in the picture below that the malware file was opened in the Hex editor as selected. The end of the screen has the characters 'MZ', shown in Hex as '4D 5A'. 'MZ' is the open string of bytes found in the PE header format. In other words, 'MZ' tells us that this file is an executable file, not compressed in the format of the winzip file. Very good! Learning about malware, you probably guessed that most files are disguised. But what if you don't learn about it now? Surely everyone will be curious to click on the file to extract and see what the content inside it means, that is to call malware into the system.
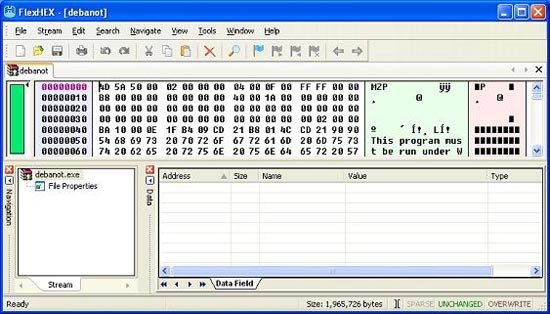
Figure 2
The question is whether the winzip file format looks like a byte level. Good question and we will check to see if there is a difference between them. When the PE format has an open byte sequence of 'MZ', the winzip file format will have the open byte symbol of 'PK'. On this message, consider the format of a valid winzip file.
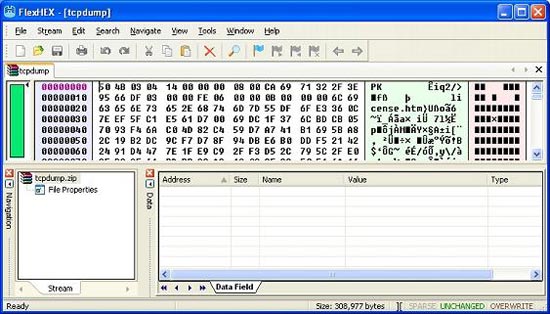
Figure 3
You can see, on the actual picture there are two 'PK' characters, or can be expressed as '50 4B 'bytes. It can be proven that the malware file is an executable type that is not a winzip compression. You should note, ASCII characters will be represented by two alphabetical numeric characters as seen on the Hex editor page. Specifically, the number '50' bytes represents the character 'P' and '4B' represent the character 'K' in ASCII code. This is a very important detail, it is possible to understand the type of packet analysis although in packet analysis we often see units expressed in bits, not whole bytes.
File format and important points
Surely everyone is anxious to 'dig' the most crucial points when they want to learn about a certain problem. But patiently considering the concepts and information around, then contacting the key of the new process is smart learning. So is reverse engineering. What is the information here, are the notable winzip file formats above or the PE header format. When doing the reverse design, you need to verify what the download file format is. To do that, you need to understand the information about it, how to test it. It is the open file in the hex editor as above, and furthermore, the copy information of the specific file format must be in hand.
The Portable Executable (PE) - is actually a natural format of Microsoft Windows. Details about this type of format are interesting and worth watching. In order to improve and sharpen computer security knowledge, you should increase the synthesis of related issues. Learning about this file format will help you mount and understand how a program on physical memory (such as a hard drive) is mapped to logical memory (RAM). It is even more interesting to read a real article about it without anything remaining in your mind.
Summary
In this article, we have reviewed a piece of malware downloaded. It is shown as a compressed file with the winzip icon. But actually after checking with the Hex editor, instead of the compressed content of the Zip file on the outside, inside the file is the PE format of the exe file. We also learn some important information about different file formats in terms of unique byte sequences. This component helps you to determine with certainty the actual format of the file. In the next section, we will look at the type of malware package used and package it. As you can see, the analysis takes place quite quickly. Simply because we only implement the simplest steps of reverse engineering.
Malware reconciliation design (part 3)