10 hackers are welcomed by technology firms
Hiring hackers to work is a wise strategy that many major technology firms have adopted.
Florian Rohrweck
Florian Rohrweck accesses Google applications' source code and reveals interesting information about Google+ before the social network is officially announced. Florian Rohrweck is invited by Google to work in a position to enhance the security of the company's Web services.

Nicholas Allegra "Comex"
Nicholas Allegra is the founder of the JailBreakMe website to help jailbreak iPhone and iPad users (intervene) on their device to run software that has not been approved by Apple. Recently, on his Twitter account, Comex announced he was admitted to an internship at Apple.

Peter Hajas
Peter Hajas is the author of Mobile Notifier - notification application for jailbroken iOS devices. A week before the announcement of iOS 5 operating system, Apple recruited Peter Hajas to work.

George Hotz "GeoHot"

George Hotz was not the first hacker to intervene for the Sony PlayStation 3 to run other operating systems and unauthorized games, but he provided instructions for others to hack the Sony PlayStation.
Since May 9, 2011, George Hotz, at the age of 21, has become Facebook's software engineer.
Steve Kondik "Cyanogen"
Steve Kondik is the author of the custom ROM version CyanogenMod is very familiar to Android users. In mid-August 2011, Samsung recruited Steve Kondik to work as a software engineer.

Jeff Moss "Dark Tangent"
Jeff Moss is the founder of DEF CON, the world's largest hacker conference and security conference for black-hat haker, bad hackers and intending to break into the system to steal information or sabotage.

In May 2011, Jeff Moss was appointed vice president and chief security officer of ICANN, a nonprofit organization that manages Internet domain names and a number of infrastructure. Jeff Moss's admission to ICANN can be seen as a 'poison poisoning ' tactic.
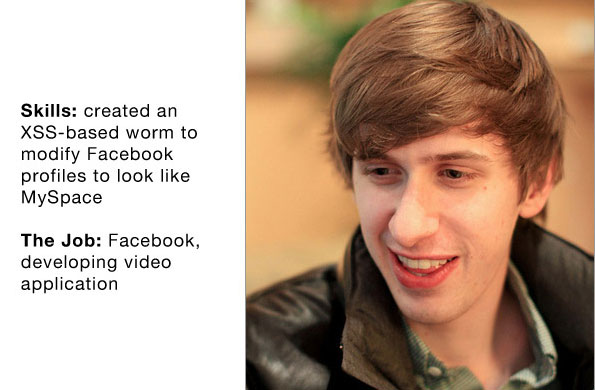
Chris Putnam
Chris Putnam is the author of some ' jokes ' on Facebook: Along with his two friends, Chris Putnam writes a worm based on XSS that spreads through Facebook pages. The infected Facebook page will have the same interface as MySpace personal page. Instead of being sued and arrested, Chris Putnam was invited to participate in social networking after going through an interview.
Peiter Zatko "Mudge"
Peiter Zatko was a member of the hacker group " The Cult of the Dead Cow " since the 1990s. At the DEFCON hacker conference in 1996, Peiter Zatko performed the unlocking of Microsoft software.
He is currently the program director for the Defense Advanced Research Projects Agency (DARPA).

Sven Jaschan
Sven Jaschan is the author of two viruses that are ranked among the top 10 most dangerous viruses of all time: Sasser and Netsky. In the first half of 2007, NetSky infected about 70% of computers worldwide.
Sven Jaschan was not imprisoned but received a 1-year and 9-month punishment because he was under 18 years of age at the time of the crime. Currently Sven Jaschan is a security programmer for German security firm Securepoint.

Kevin Mitnick
Kevin Mitnick is ranked among the most famous hackers in the world. The ' rogue ' achievements of Kevin Mitnick include entering the internal government system of the United States, some large banks, software stealing from reputable companies such as Sun Microsystems, Motorola, Novell, Fujitsu.
Kevin Mitnick currently runs Mitnick Security Consulting, a security consulting firm that hires their computer systems from other companies and notifies them if they discover a vulnerability.
