Russian Hacker is using Google's own infrastructure to hack Gmail users
Security researchers have discovered a sophisticated hacking and fake news campaign targeting more than 200 Gmail accounts.
Hackers in Russia seem to have figured out a way to bypass Gmail's censorship engine to infiltrate user accounts thanks to Google's own services.
On Thursday, researchers found a spying and fake information campaign from Russia using sophisticatedly designed email to trick users into "giving" passwords to hackers without knowing it. It is a phishing technique targeting more than 200 victims, including journalists and political activists of the Russian government, as well as those with links to the Ukrainian army and senior officials in the companies. energy in the world.

The Citizaen Lab team at Munk School - University of Toronto has identified the number of victims based on traces in two phishing emails sent to David Satter, an American journalist and researcher.
On October 7, Satter received a design impersonation email that looked like from Google content support that someone had stolen an account password. In the letter suggested you need to change the security code by clicking on the link provided.
Just like the phishing attacks on Hillary Clinton's campaign led to the e-mail leak of the Democratic National Committee (DNC) last year, that email didn't come from Google. In fact, they are products of hackers called Fancy Bear or APT28 from Russia.

The "Change Password" button is associated with a shortened URL from the Tiny.cc service, a Bitly competitor. However, hackers cleverly designed landing pages into legitimate links using Google's AMP (Accelerated Mobile Pages page). This is a service to create lightweight and fast-loading websites that fit the search giant's mobile device. Notably, they were made a copy on Google's server and acted as a landing page redirect.

According to Citizen Lab experts, hackers use Google AMP to trick victims into believing it is an email from Google. John Scott-Railton, senior researcher at Citizen Lab, said: " It's a chance game, you can't catch every fish targeted, but there is still a certain percentage of traps ."
If you move the mouse pointer over the link to test, the victim will see a URL in the form of Google.com/amp that looks very safe followed by the short form of Tiny.cc. For example: https://www.google.com/amp/tiny.cc/abcd.
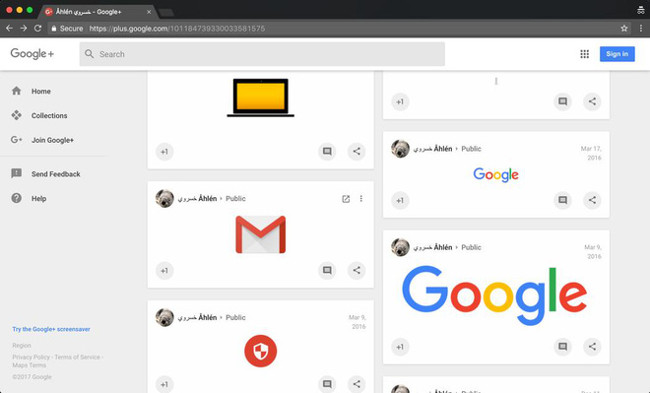
The trick to using Google's redirection service can bypass Gmail's filter. And yet, Citizen Lab also found the shortened address as Tiny.cc pointing to Google Plus page containing a security warning image that looks like Gmail. Chances are, hackers use to embed phishing emails to avoid Google's control.
Users should be wary of strange email or check the email address carefully to avoid being cheated. Recently, WannaCry "pandemic" also partially infects the way the link comes in the mail. It becomes an expensive lesson for those who lack vigilance in protecting themselves.
According to Genk
You should read it
- ★ Instructions for adding email accounts to Gmail on iPhone, iPad
- ★ Microsoft admits hackers may have read Outlook email and warned users to change their passwords
- ★ How to identify phishing emails
- ★ Leave Gmail as the default mailbox for many email addresses
- ★ How to add and delete Email accounts on Mac, iPhone and iPad