Malware reconciliation design (part 3)
Malware reconciliation design (part 1)
Malware counterpart design (part 2)
Uncover the tricks of the spammer, the internet social guys and some others with the covert content, hide the real malware inside .
As learned in part 2, you can see that not everything is the same as our eyes see. Spammers, people at the bottom of cyber-society and others are always trying to cover up the real malware with very fake fake covers. In the next part of this series, we will continue to strip and unmask their behavior patterns.
In Part 2, we are stopping at the time of realizing that the downloaded malware is in fact not a harmless zip file, but a PE executable format. We have confirmed this by opening the malware in the Hex editor. This editor allows you to check the contents inside without executing the file. The 'MZ' character in the file indicates that this is actually the type of PE file format mentioned above.
 You should also remember that this information is completely clear, nothing is magic or mystery about it. It is not a valuable cumulative experience from government organizations, nor is it a theoretical system of theorists. What we have here is a deeper digging design and applied experiment to learn about underground art in the virtual world. Reference material is very rich and completely free. You can find out about PE format on Microsoft or Google website. The system of comparative design theory and its tools can be easily found on some websites such as OpenRCE.
You should also remember that this information is completely clear, nothing is magic or mystery about it. It is not a valuable cumulative experience from government organizations, nor is it a theoretical system of theorists. What we have here is a deeper digging design and applied experiment to learn about underground art in the virtual world. Reference material is very rich and completely free. You can find out about PE format on Microsoft or Google website. The system of comparative design theory and its tools can be easily found on some websites such as OpenRCE.
Malware packages
Why does the malware file need to be compressed again? Is it really just that you want to reduce the actual size, or more importantly, to avoid virus scanners. There are many anti-virus programs that will remove malware even if it is custom written. Size is a weakness of malware against antivirus software. So the black-hat hacker world decided to use many other loops, such as creating packers.
There's a saying that 'creator doesn't create everything the same', and so does the hacker. Each person has a different type or level of skill. Some write custom packages like Yoda, while others simply use UPX to package malware. Review the illustration below, the malware section is open in the Hex editor, notice that you will see ASCII characters 'UPX'.
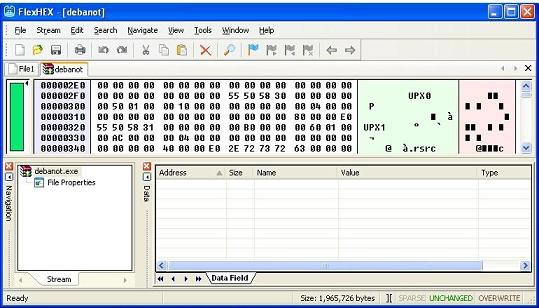
Figure 1
If you haven't found it yet, look under the characters 'MZ'. As mentioned, MZ is an expression for PE file format. Below it is a bit of UPX string. This string tells us that the executable file is packaged by the UPX package. Often, opening a packaged file is not easy, but it is not difficult with UPX. You can open the package easily with the tool itself. But be aware that some files can be packaged with UPX, but are encrypted or perform some tricks that make it difficult to open packages.
Let 'party' be started
To open the UPX file package, start by downloading a copy of the UPX program and installing it into the root directory of drive C. Then invoke the program itself and insert the command line information. Usually, it is also useful to copy malware to drive C. See the help menu illustration provided by UPX below after calling the program.
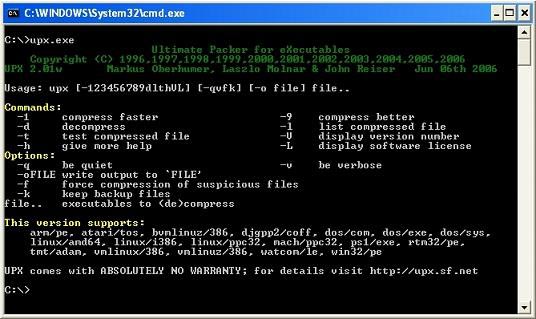
Figure 2
Now, see the command line information on the picture.
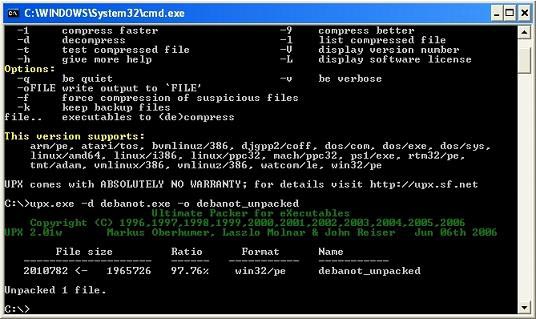
Figure 3
As you can see, opening the UPX package is quite normal, nothing special called difficult. The problem is that you have to determine what kind of packing the malware file is. That's what makes even experts have headaches.
Where are we stopping?
We have started and are stopped at the time when malware analysis can begin. This is done in many different ways, but most commonly in two ways: static analysis and dynamic analysis of malware executable files. What is dynamic but what is static? Static analysis is the process of opening malware programs but not actually executing them. This type of analysis is primarily used in the Hex editor as you saw in the previous section. It can be done through a number of separate components.
These components allow you to securely view executable code without worrying that they will "act impersonally" on your computer. At the same time they also allow you to write some space (offset) for interesting break points. Breakpoint, basically the address of the command computer in the program. From there you can perform step-by-step executable commands at each time. Maybe the problem is a little bit advanced, but it is also an appropriate platform for a deeper understanding of comparison design.
Dynamic analysis is the process by which you run the actual malware file and monitor the impact that will take place later. Dynamic analysis is not as difficult as its name suggests. There are many smart tools that allow you to observe changes on your computer after the malware is executed. One of them is filemon and regmon.
Summary
So far, we have gone into quite a bit of detail on some external factors before considering the malware reconciliation problem. Simply because they are very important. Understanding malwere collation design means understanding the specification of file formats, file packages, using the Hex editor, and so on. When approaching difficult issues such as counter-design, slow but firm, short but steady is the best method. Reverse engineering information is no less on the Internet. What you need to do now is 'digest' gradually mass small bytes of knowledge. In the following section we will continue to meet again with the process of package details of malware files. See you again!
Malware counterpart design (part 4)