Is Ransomware Annabelle scary with Annabelle movies?
While most extortion codes are created to make money, some people create them to show their skills. That's the case of ransomware inspired by the horror film Annabelle.
Discovered by security researcher Bart, Annabelle's e-money code offers everything to 'harass' a computer, such as stopping security software, disabling Windows Defender, turning off the firewall, encrypting files. , trying to distribute via USB, cannot run multiple software, overwriting Master Boot Record (MBR) with Boot Loader.
On the first run, Annabelle configured herself to turn on automatically every time she logged into Windows. Then stop running many software like Process Explorer, Msconfig, Task Manager, Chrome, Process Hacker .
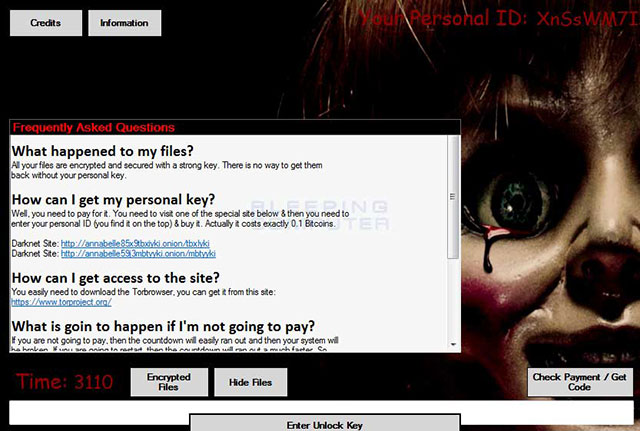
The lock screen is displayed every time the user logs in
Annabelle will then configure Image File Execution registry entries to not be able to open the above mentioned software and other software such as Notepad ++, Notepad, Internet Explorer, Chrome, Opera . Then the malicious code will spread itself. with the file autoru.inf. This is also quite useless because new versions of Windows do not support the autoplay feature.
When all is finished, it will encrypt the machine with a static key and add the .ANNABELLE extension to the end of the file name.

Encrypted files will be attached with the .ANNABELLE extension to the name
The computer will then restart and when the user logs in, the lock screen will appear with the developer name iCoreX0812 and how to contact them on Discord. Eventually it will run a software that replaces the Master Boot Record to display a screen with information about the developer every time the machine turns on.

Screen showing the developer information
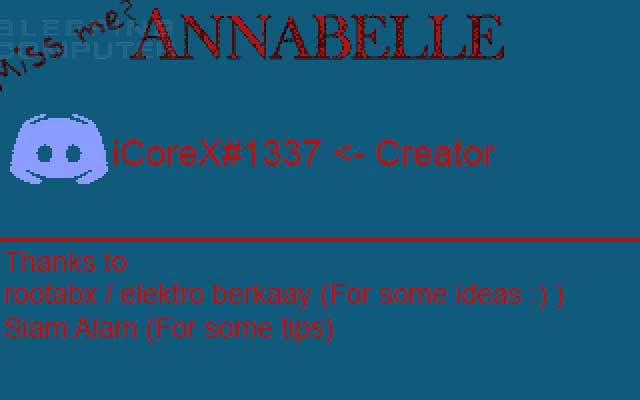
MBR lock screen
In general, this code only allows its owner to display his 'skills', not really to blackmail. It is also based on Stupid Ransomware and can be decoded. Because of the static key, Michael Gillespie can update StupidDecryptor to fake this variant code.
By replacing the MBR, run Rkill in Safe Mode to clean up the IFEO registry entries, use Michael's decryption tool to decrypt the file and security scans to clean up the remnants, you can put your computer in a state of normal if this is infected.
IOC information
Hashes
716335ba5cd1e7186c40295b199190e2b6655e48f1c1cbe12139ba67faa5e1ac
Related files
Copter.flv.exe
MBRiCoreX.exe
See more:
- How is GPT and MBR different when partitioning a drive?
- New ransomware appeared not to send Bitcoin, money, but . nude photos !!!
- MongoDB malicious code attacks more than 26,000 victims in a week
You should read it
- ★ Disable malicious HiddenTear Ransomware with HT Brute Forcer
- ★ How to handle the emergency WannaCry malicious code from the National Information Security Department
- ★ Lukitus Guide to preventing extortion malicious code
- ★ Ryuk Ransomware has added 'selective' encryption capabilities.
- ★ GIBON extortion code spread through spam