Ryuk Ransomware has added 'selective' encryption capabilities.
A new variant of Ryuk Ransomware has been found to have added IP addresses and blacklists of computer systems so that appropriate computers will not be encrypted.
This new Ryuk Ransomware variant was discovered yesterday by MalwareHunterTeam. Security researchers have found that the new variant is signed by a digital certificate. After this ransomware sample was thoroughly tested by security researcher Vitali Kremez, it was discovered that several important changes were applied to the new variant, which was not found in the previous version.
- The official GandCrab 5.2 decoder was released, ending the bad nightmare called GandCrab Ransomware
 Ryuk blackmail code
Ryuk blackmail code
Vitali Kremez has found that with the new variant, Ryuk Ransomware will be added with the ability to check arp -a output data for specific IP address strings and if these IPs are found, it will Do not encrypt the victim computer.
The localized malicious IP address strings include: 10.30.4, 10.30.5, 10.30.6 or 10.31.32.
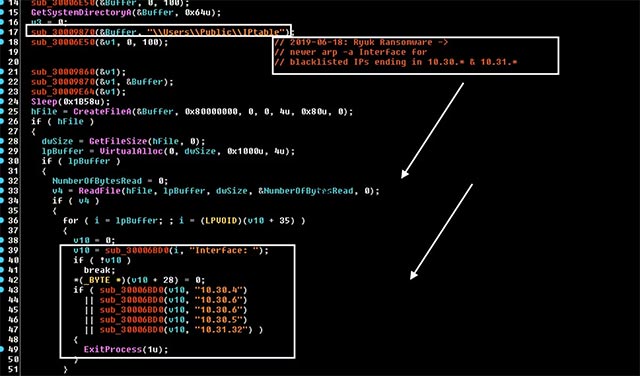 Local IP address string is found malicious code
Local IP address string is found malicious code
In addition to the IP address blacklist, this new Ryuk variant will also be able to compare the target computer name with the "SPB", "Spb", "spb", "MSK", "Msk" and "msk" strings. ". If the target computer name contains any of these strings, Ryuk will not proceed to encrypt the computer.
- Shade ransomware, the nightmare of 5 years ago is showing signs of returning
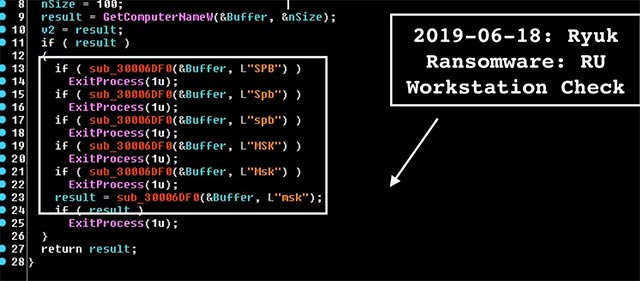 Comparative character strings
Comparative character strings
The real purpose for this new feature of the money-ridden Ryuk has raised a lot of questions for security researchers. The answer that received the most conclusive opinions so far is to avoid coding 'wrong' computer systems in a particular region or country, such as in Russia - where set the command and control servers (C&C) of this malicious code.
Although Ryuk Ransomware tried to 'ignore' Russian, Ukrainian or Belarusian-language computer systems, it did not rule out the possibility that Russian-based computers could still be infected. ' wrong '.
For example, an attacker may target computer systems based in the United States, but security expert Vitali Kremez said that after using the "EternalRomance exploit and the SMB spread method, they could use cobalt strike to attack Russian-based systems'.
- New ransomware detection not only encrypts files but also helps 'clean up' the system
By examining the "MSK" sequences (which may be short for Moskow and "SPB", meaning St. Petersburg), malicious code will avoid the possibility of infecting computers in National Community regions. Independent (CIS).
Encryption as usual
If the target computer system does not contain the same characteristics as the malicious code, it will still be encrypted as normal. Ryuk Ransomware will append the .RYK extension to the files that have been successfully encrypted.
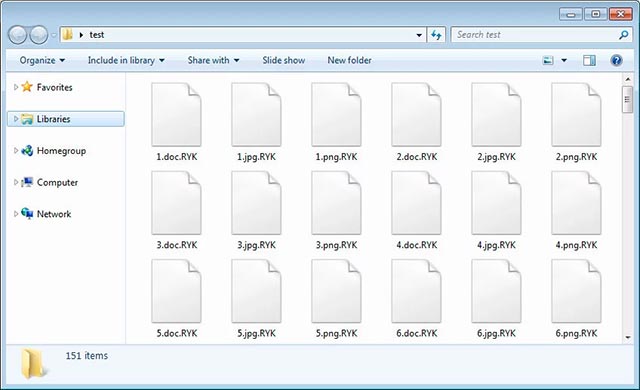 The file was encrypted by Ryuk Ransomware
The file was encrypted by Ryuk Ransomware
While encrypting the file, the malicious code will also generate RyukReadMe.html files with the contents of the ransom note containing the "balance of shadow universe" phrase, and some email addresses for victims to contact payment. ransom.
"Balance of shadow universe" sounds pretty cool, but security researchers have yet to really grasp what the meaning behind it is. Meanwhile, the email addresses currently used in ransom notes are sorcinacin@protonmail.com and neyhyretim@protonmail.com.
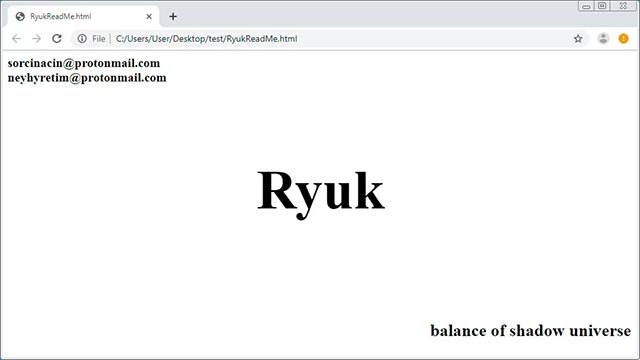 Ryuk Ransomware's notes
Ryuk Ransomware's notes
As always, we recommend that you do not pay a ransom if possible and instead restore important data from backups.
- [Infographic] 7 effective ways to protect businesses from Ransomware
Protect your computer against the spread of Ryuk Ransomware
In essence, extortion code is only really harmful in case you have absolutely no way to recover your encrypted data. Therefore, it is important to always have a reliable backup of important data, and build your own backup plan periodically so that it is most reasonable.
Besides, backups of important documents should also be stored offline and make ransomware inaccessible.
Although this ransomware software is not distributed via spam like many other well-known extortion codes, it is most likely being installed by Trojans. Thus, the next important thing is that all users in the computer system must be trained, as well as adding knowledge about how to correctly identify malicious spam and not open any attachments. but questions have not been clearly defined as they are sent from and why they were sent.
Finally, the most important thing is to make sure that your network does not make the Remote Desktop Service services publicly accessible over the Internet. Instead, you should place it behind the firewall and the settings are only accessible via VPN.
- The cybersecurity tools that every business should know
You should read it
- ★ Mexico's largest oil and gas corporation has been attacked by ransomware, presenting a cyber security disaster
- ★ Ryuk Ransomware stops encrypting Linux directory
- ★ Strange ransomware detection only attacks the rich
- ★ Shade ransomware, the nightmare of 5 years ago is showing signs of returning
- ★ PureLocker - a very 'weird' ransomware strain that can encrypt servers