Is TLS or SSL a better web encryption standard?
With so many big data breaches happening lately, you might be wondering how your data is protected while you're online. When you visit a website to shop and enter your credit card number, you hope in a few days a package will arrive at your doorstep. But at the moment before you hit the order button, have you wondered how online security works?
Online security basics
In its basic form, online security - security that takes place between a computer and a website - is done through a series of questions and answers. You enter a web address in your browser, then the browser asks the site to verify its authenticity. The website responds with the appropriate information, and after both parties agree, the website opens in a web browser.
Between the questions asked and the information exchanged are data about the type of encryption that transmits browser information, computer information, and personal information between the browser and the website. These questions and answers are called a handshake. If that handshake doesn't take place, the website you're trying to access is considered unsafe.
SSL and TLS
SSL
- Originally developed in 1995.
- Old web encryption level.
- Lags behind the fast growing Internet.
TLS
- Beginning is the third version of SSL.
- Short for Transport Layer Security.
- Continue to improve the encryption used in SSL.
- Added security fixes for new types of attacks and vulnerabilities.
SSL is the original security protocol that ensures that web pages and the data transferred between them are secure. According to GlobalSign, SSL was introduced in 1995 as version 2.0. The first version (1.0) was never put into the public domain. Version 2.0 was replaced by version 3.0 for a year to address the vulnerabilities in protocol.
In 1999, another version of SSL, called Transport Layer Security (TLS), was introduced to improve the speed of the conversation and the security of the handshake process. TLS is the version currently in use.
TLS encryption
Advantages
- Encryption is more secure.
- Hide data between computers and web pages.
- Make the handshake process better with encrypted communication.
Defect
- No coding is perfect.
- Does not automatically secure DNS.
- Not fully compatible with older versions.
TLS encryption was introduced to improve data security. Although SSL is a good technology, security changes at a rapid rate and that leads to the need for better, more up-to-date security. TLS is built upon the SSL framework with improvements to the communication governing algorithms and handshake.
What is the latest version of TLS?
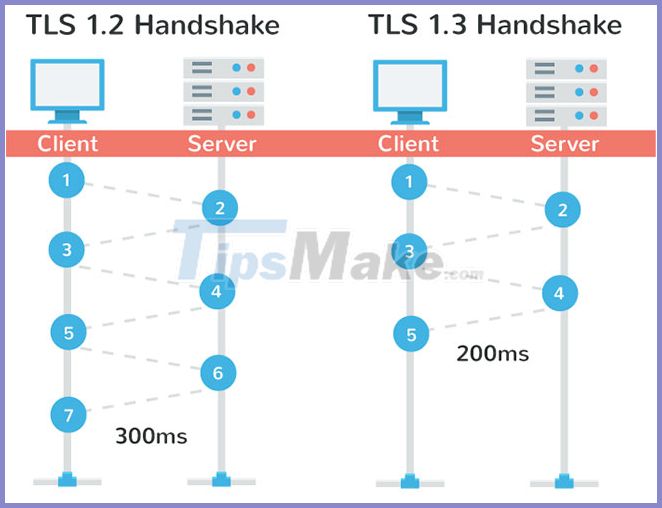
Like SSL, TLS encryption continues to improve. The current version of TLS is 1.2, but TLSv1.3 has been drafted and some companies and browsers have adopted this security standard for a while. In most cases, they revert to TLSv1.2 because version 1.3 is still being finalized.
When finalized, TLSv1.3 will bring a number of security enhancements, including improved support for more existing encryption types. However, TLSv1.3 will also discontinue support for older versions of the SSL protocol and other security technologies that are no longer strong enough to ensure security, as well as appropriate encryption for data. personal.