How to protect Google Chrome from Rust malware EDDIESTEALER
Rust is one of the systems programming languages used in the backend of Google Chrome . Recently, a Rust-based malware called EDDIESTEALER has started attacking Chrome users through fake CAPTCHA verification pages. This is not the first time, as similar incidents have been reported before. Here are some solutions to protect your Google Chrome browser from Rust malware threats.
Why is Rust malware in Chrome so effective?
Rust-based malware is effective in Google Chrome because it hides its code using social engineering while bypassing Chrome's application link encryption, introduced in version 127. Rust uses string and API obfuscation, self-destruction, and multi-stage payloads to sneak malware into web browsers. Chrome's widespread use and user trust make it a prime target.
EDDIESTEALER is a Rust-based information stealer recently analyzed by Elastic Security Labs on May 30, 2025. It targets Chrome users via fake CAPTCHA prompts on compromised websites, tricking Windows users into pasting a malicious PowerShell command into Run. It downloads an obfuscated JavaScript payload ('gverify.js') to the PC's Downloads folder.
Taking advantage of Rust's stealth capabilities, the malware evades Chrome's sandbox (similar to CVE-2025-2783) and self-destructs. Its payload steals data from cryptocurrency wallets like Bitcoin and WasabiWallet, password managers like Bitwarden and KeePass, and apps like Telegram Desktop.
EDDIESTEALER is following the pattern of previous Rust malware that have targeted Chrome, such as 'Fickle Stealer', which appeared in mid-2024, and 'StealC', which was discovered in early 2023. All three used social engineering like fake CAPTCHAs, phishing , and malvertising to launch multi-stage attacks.
Use Chrome's Enhanced Protection
On the Chrome browser page, click the three-dot menu in the top right, then Settings -> Privacy and security -> Security -> Enable Enhanced protection .
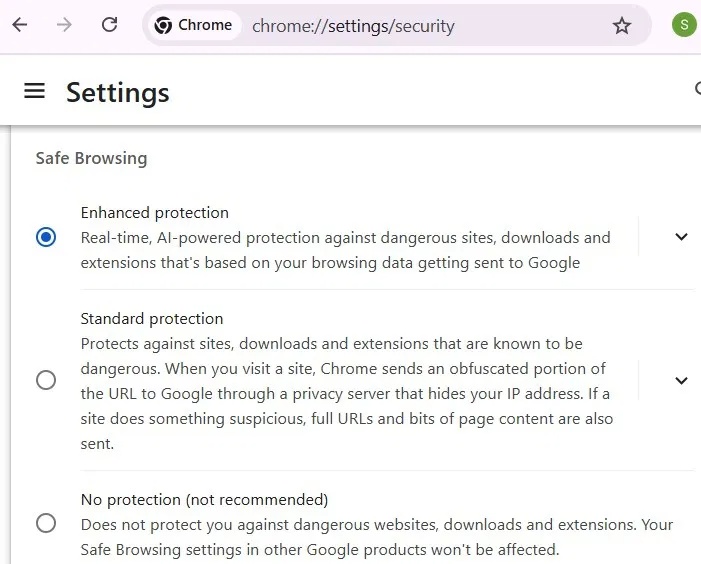
Enhanced Protection uses Machine Learning and AI to detect threats in real time. While Rust malware threats are user-initiated, enhanced mode is more effective at identifying fake CAPTCHAs and unverified websites, and displays an 'unsafe download blocked' warning. Also, avoid visiting Chrome sites marked as Not Secure for added peace of mind.
Disable JavaScript for untrusted sites (Optional)
This setting is optional for Chrome users who only visit a few websites or have separate Chrome profiles designated to block JavaScript entirely.
Go to Settings -> Privacy and security -> Site Settings -> Content -> JavaScript. Select Don't allow JavaScript . You can then add more trusted sites to the exceptions under this setting by clicking Add next to Allowed to use JavaScript .
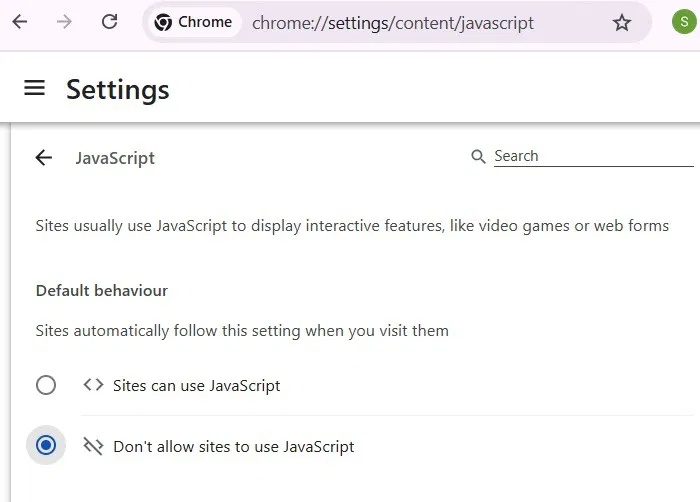
All of the Rust-based malware examples we've seen so far use JavaScript to push the payload to the Chrome browser. The minimal JavaScript setup above is an easy way to completely block it. However, it can be inconvenient to keep a whitelist for JavaScript sites. But then again, many modern sites, such as DuckDuckGo , offer JavaScript-free versions.
Prevent websites from automatically downloading multiple files
If you want to avoid whitelisting JavaScript, you can instead restrict uncontrolled downloads.
First, go to Settings -> Downloads -> Enable Ask where to save each file .
Then go to Settings -> Privacy and security -> Site Settings -> Additional permissions -> Automatic downloads. Select Don't allow sites to automatically download multiple files .
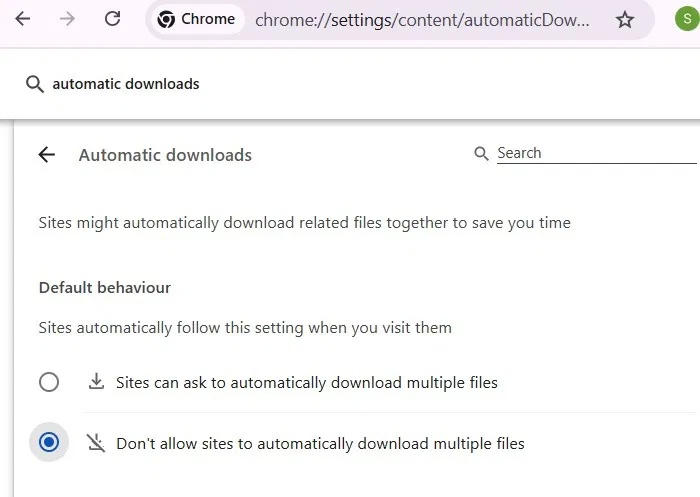
The above setting prevents malicious JavaScript payloads, such as "gverify.js" in EDDIESTEALER, from downloading in the background without your knowledge.
Prevent Rust malware with strict site isolation
In the Chrome address bar, type Chrome://flags and press Enter. Now, go to the flag named Disable site isolation and make sure that this flag is kept at Default .
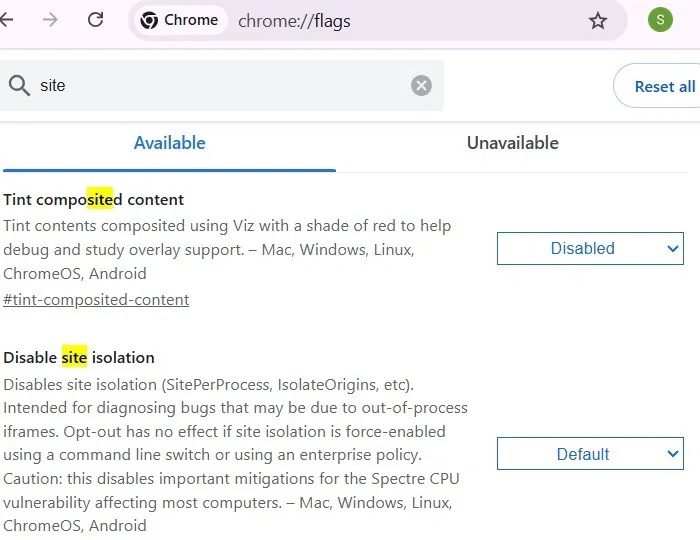
Set up isolation on web processes to limit memory-based exploitation of all web-based malware, including Rust malware. You can also achieve this isolation through other methods such as Chrome Properties in Windows.
Only download extensions from the Chrome Web Store
Chrome supports third-party extensions, but downloading them from the Chrome Web Store helps protect against malware that uses hidden APIs to launch attacks. EDDIESTEALER used this tactic, leveraging Rust's hidden programming to bypass Chrome's sandbox detection and other flags.
To increase security against Chrome-based malware, Google has begun phasing out SMS-based two-factor authentication. Instead, Google offers more secure alternatives like passcodes and authenticator apps, which should be enabled as soon as possible.
You should read it
- Warning: New malware 'Mamont' impersonates Google Chrome to steal information
- What is Goldoson Malware? How can you protect yourself?
- Microsoft 'paralysis' Chrome is malware
- Google updates Chrome to prevent Microsoft from mistaking it for malware
- Hacker attacks Chrome utility to install malware
- ChromeLoader malware rages around the world, attacking both Windows and Mac
 Instructions for commenting with photos on TikTok
Instructions for commenting with photos on TikTok How to mark Instagram messages as unread
How to mark Instagram messages as unread 6 Microsoft Excel formatting habits to break
6 Microsoft Excel formatting habits to break 4 Browsers with the Best AI Features
4 Browsers with the Best AI Features How to resize each page in Canva
How to resize each page in Canva How to change Messenger notes disappearance time
How to change Messenger notes disappearance time