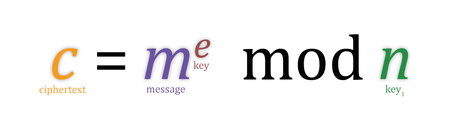How to Create an Encryption Algorithm
Part 1 of 2:
Creating the Encryption Method
-
 Design the algorithm. A general algorithm is the backbone of all encryption methods. RSA uses mathematical properties of large prime numbers to quickly and safely encrypt private data. Bitcoin uses a version of RSA to safely secure payments and ensure that the sender actually wants to send bitcoins to another user. You should do research on various types of encryption algorithms, like private and public key encryption. It should be noted that no encryption, if you plan on retrieving the data, is unbreakable. Encryption can only discourage casual snooping, and delay serious attacks. It is recommended that you learn what binary is, it will make creating your algorithm much easier and more relevant to data encryption.
Design the algorithm. A general algorithm is the backbone of all encryption methods. RSA uses mathematical properties of large prime numbers to quickly and safely encrypt private data. Bitcoin uses a version of RSA to safely secure payments and ensure that the sender actually wants to send bitcoins to another user. You should do research on various types of encryption algorithms, like private and public key encryption. It should be noted that no encryption, if you plan on retrieving the data, is unbreakable. Encryption can only discourage casual snooping, and delay serious attacks. It is recommended that you learn what binary is, it will make creating your algorithm much easier and more relevant to data encryption. - Test your algorithm. Once you think you've got a good algorithm, you should try encrypting a very short message by hand. This should take more than a few minutes for good encryption algorithms. A good rule of thumb is that, if you can encrypt the message in your head, then it is not safe for serious encryption. If the final message looks similar, in any way, to the original message, then it might not be safe.
- Consider decryption. There needs to be a way for authorized parties to access data encrypted by your algorithm. You should make sure that you can easily decode the data if you know the key, and make it hard for attackers to accidentally stumble upon the key through trial and error.
- If you do not want the data to be retrievable at all, consider creating a hashing algorithm instead. A hashing algorithm takes an input and creates a one-way value based on this input. It's possible to go from source input to a hashed value, but it is ideally impossible to go back to the source input from the hashed value. This is particularly viable for password protection. When you create an account on a website with a password, ethical websites will hash your password before storing it. This has many benefits, such as delaying attackers from cracking your password. However, if you forget the password, you'll be forced to create a new one.
- Draft the pseudocode. This should be relatively easy once you have your algorithm created and tested to prove that it works. The pseudocode should read like simple and instructive English, being readable enough for a normal person to understand, and instructive enough for a programmer to easily implement the algorithm into a language like C, Java, etc.
Part 2 of 2:
Publish the Algorithm
- Share your algorithm with other data encryption enthusiasts. This will allow you to discover possible trapdoors in your encryption, and get feedback on the security and viability of the algorithm. If your algorithm is so complex that no one can understand it, then no one will use it. But the same goes for if the algorithm is so easy that anyone can decode a message with minimal effort.
- Post a challenge on a forum. There are forums dedicated to solving and decoding data, try publishing a short message you encrypted along with hints about the algorithm used. If you're feeling confident, you can even give them your algorithm and see how long it takes for others to crack it through brute force.
Share by
Isabella Humphrey
Update 05 March 2020