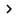How the botnet works (Part 2)
How the botnet works
An actual C&C - Agobot
Now is a sample attack, allowing us to see and understand how a Command and Control program is executed. Two computers will be used. The first machine runs an IRC server based on UnrealIRCd 3.2.3 and two virtual Windows XP SP1 operating systems based on VMware Workstation (two target computers are vulnerable). The second machine is for the host, controlling the botnet via Irssi, a text IRC client.
To make it difficult to create reverse engineering programs, Agobot does a number of protection routines in front of debugger like SoftICE or OllyDbg and before virtual machines like VMware, Virtual PC. It is necessary to hack the source code to bypass VMware's protection program, before you can install the bot on our sample virtual machines.
Configuration
The first step is to configure the bot via its simple graphical interface (see Figure 3). The information entered includes the name, the IRC server port number, the channel name, the user list with the master password (the master controller), and finally the file name and the bot installation directory. Some additional components are also enabled such as support for sniffing and status mechanisms. The result of this stage is the file config.h, the background file during the compilation of the bot created.

Figure 3 : Agobot configuration interface.
Command control (Command and Control)
After the bot is compiled, the other two systems will attack in a 'manual' manner. The server (master) connects to the IRC server and links to the channel to be able to issue a command to control the bot (see Figure 4).
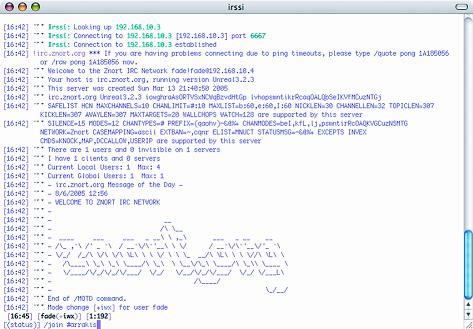
Figure 4 : Server and channel connection
To gain control over bots, an authentication mechanism is needed. This mechanism is created simply by sending a command to the channel (see Figure 5).
.login FaDe dune
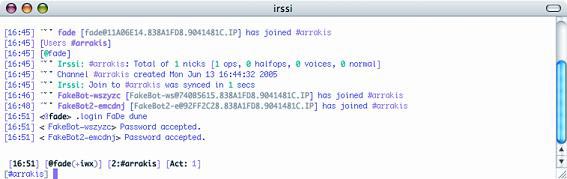
Figure 5 : Verify the username and password
After that, the first bot was asked to list all the programs running on the hijacked computer (see Figure 6):
/ msg FakeBot – wszyzc .pctrl.list
Figure 6 : The server issues a request for the first bot
After that, the second bot is asked to give the information and key cdkey of the applications installed on the machine (Figure 7):
/ msg FakeBot2 – emcdnj .bot.sysinfo
/ msg FakeBot2 – emcdnj .harvest.cdkeys
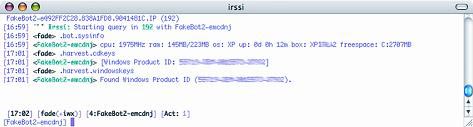
Figure 7 : The server makes a request for the second bot
In this example we use very simple features. In fact, Agobot provides a very rich set of commands and functions. One of them you can see in Table 2:
Command Descriptioncommand.listList all commands that can usebot.dnsHandle an IP address or hostnamebot.executeRun an .exe file on remote machinebot.openOpen a file on the remote machinebot .commandRun a command with system ()irc.serverConnect to anirc.joinIRC serverEnter the information of a specific channelirc.privmsgSend a private message to anhttp.executeuserDownload and execute the file via HTTPftp.executeDownload and execute the file via FTPddos.udpfloodStart a UDP program overflowddos.synfloodStart a Syn overflowddos.phaticmpStart a PHATicmp overflowredirect.httpStart an HTTP proxyredirect.socksStart one SOCKS4 proxypctrl.listGive a list ofpctrl.killprograms Remove programs
Table 2 : Some Agobot commands
How to protect your computer
Now we will look at some methods of protection against intrusion and vandalism of bot attacks, from the perspective of both users and administrators.
Protection strategies for PC users
As mentioned above, bot attacks are mostly done through worms, surfing the web to search for vulnerabilities. Therefore, the first step is to regularly update, download patches and system updates for both the operating system and Internet access applications. Using an automatic update program is a good idea. You should also be careful when opening suspicious attachments in e-mail. It would also be wise to remove support for scripting language forms such as ActiveX and JavaScript (or at least control their use). Finally, the basic factor is that you must use at least one program to remove viruses and trojans and always update their latest version. Even so, many bots are configured to avoid starting control of antivirus programs. Therefore, you should use more personal firewall software, especially when using a computer connected to the network 24 hours a day.
The main sign of bot presence is the speed of the device and the network connection speed is extremely slow. A simple and effective way to check suspicious connections is to use the netstat tool (see Figure 8):
C: /> netstat -an
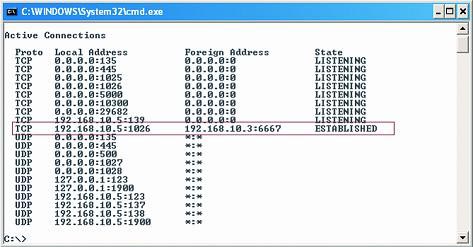
Figure 8 : Netstat on a compromised machine
Netstat
Netstat is a flexible, compatible tool both on Windows operating systems and * NIX systems. Its function is to control enabled ports. Netstat checks the listening process on TCP and UDP ports, then provides detailed information and network activity. On * NIX systems, netstat displays all open lines. It also uses external selection filters.
The connection status may be on Netstat including:
- ESTABLISHED - all hosts are connected
- CLOSING - Remote host is closing the connection
- LISTENING - the host is listening to the connection
- SYN_RCVD - a remote host is required to start the connection
- SYN_SENT - host is starting a new connection
- LAST_ACK - host must send report before closing connection
- TIMED_WAIT, CLOSE_WAIT - a remote host is terminating the connection
- FIN_WAIT 1 - The client is ending the connection
- FIN_WAIT 2 - both hosts are ending the connection
Observe ESTABLISHED connections to TCP ports in the 6000 to 7000 range (usually 6667). If you find yourself compromised, disconnect it from the Internet, clean the system, reboot and check.
Protection strategy for administrators
Administrators often have to constantly update information on the latest vulnerabilities, as well as read regularly about security resources on the Internet every day. Some tools that support Bugtraq, offering a brief list of mailing lists are a good idea. Administrators should also try to propagate, raise awareness for their users about security issues and security policies.
Researching the logbook (log records) created by IDS and many firewall systems, mail servers, DHCP, proxy servers is also necessary. This can help detect abnormal traffic, a sign of bot presence and thus timely preventive measures. After the abnormal traffic is noticed, a siffer will come to identify the subnet and the computer to create it. All measures seem to be familiar and not difficult, but people often forget, or ignore them.
You can also use some more complex techniques like honeybot. Honeybot is a machine built with the purpose of attracting attackers. Their role is to become a victim computer, helping administrators locate the source of the problem and studying the attack method.
But the final conclusion, no matter what support tools are, the best defense and protection against botnet attacks is the users themselves and their perceptions.
Something about the author
How the author of " Robot Wars - Botnet Works " that we have just reviewed part of its content is a group of three: Massimiliano Romano , Simone Rosignoli , Ennio Giannini . If there are conditions and readers who want to learn more about the interesting content in this book, you can buy on eBay or search from rich Internet sources. And below are some things about the author of this book:
Massimiliano Romano : His hobby is computer science and networking. He works as a freelance employee in one of Italy's largest mobile phone companies. He spent a lot of time in Ham Radio, investing in researching and decoding digital radio signals.
Simone Rosignoli is currently a student at La Sapienza university in Rome. He is pursuing with Computer Science (security and system) technology at school. The interest of this student is computer security programming. Indeed, 'talent is not waiting for age'!
Ennio Giannini works as a systems analyst. He spent a lot of his free time on tests in the GNU / Linux environment. He is a strong and open source support and organization.