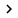Host-Based IDS and Network-Based IDS (Part 1)
In this article, we will talk about the difference between NIDS (Network Intrusion Detection System) and HIDS (Server Intrusion Detection System). Also give a comparison in part two of this article to support choosing the appropriate IDS for your organization. Important facts and considerations will be introduced to assist in selecting this system. This article will give you a better understanding of the difference between HIDS and NIDS and also the strengths and weaknesses of the IDS system.
Function of IDS
The IDS system is used to create security for incoming and outgoing packets in the network. IDS is often used to detect network packets by providing you with an understanding of what is really happening in the network. There are two main options when adding IDS on HIDS and NIDS. Some IDS have the ability to distinguish the different types of network traffic on the same port and it may show you whether the request is an HTTP request on port 80 or the user is using the system. Instant Message takes priority on port 80. IDS has the ability to remove dangerous codes that could harm your network. This is the latest technology enhancement in the firewall field, and because IDS has sample files, you can be sure that the most recent network failure issues will be addressed to LANs, WANs, and Your WLAN or PAN. HIDS can work if you turn on or off a LAN or connected network as it resides on a local computer.
Product
IDS type
Price
More information
INTRUST Event admin AelitaHIDS
$ 599 / server, $ 64 / workstationSee here
ELM 3.0 TNT softwareHIDS
$ 515 for TCP / IP servers, workstations and agentsSee here
GFI LANguard SELMHIDS
$ 375 for 2 servers and 10 workstationsSee here
Snort ISSNIDS
Free software packageSee here
Cisco Secure IDSNIDS
Over $ 1000See here
Dragon EnterasysNIDS
Over $ 1000See here
A brief introduction of products, detailed comparisons will be introduced in part 2 .
Statistics about IDS
• Over 90% of connected networks are using IDS to detect computer security vulnerabilities.
• July 4, 2, Computer Security Institute reported that 80% of the financial losses exceeded $ 455 million caused by intrusion and malicious code.
• Millions of jobs affected by intrusion.
• Only 0.1% of companies are spending an appropriate amount on IDS
• IDS is almost unknown and is thought of as a firewall product or an alternative component.
• If you use an antivirus software, you must consider adding an IDS for your security strategy. Most organizations use antivirus software without using IDS.
IDS is a major tool that contributes to security suites such as firewalls or antivirus software. Those tools will not be effective if used separately. Therefore we need to incorporate reliable and rigorous testing technologies, ensuring that the IDS application used for your organization is like meticulously tailored clothing.
Many network security experts know that firewalls are an essential component of a comprehensive security plan. They also found that IDS is an effective complementary product to well implement the company's security strategy. But what security experts don't realize is which IDS is best suited for their organization.
Intruders are able to adapt and, after understanding that there is a network IDS, they will soon find another path to bypass network IDS systems. With warning systems, no warning can prevent intruders from breaking into your system, a warning usually only informs the respective owner of the behavior trying to perform. infiltrate the system. The warning may serve as a deterrent but in some cases the intruder will continue to perform his behavior despite a warning. Some warnings (IDS systems) are capable of removing corrupted packages that it has identified in the same way that antivirus software manufacturers use to detect viruses. All packages that pass through the IDS are analyzed and compared to the sample file or signature file to confirm that it is not the attacker's file. If the packet is discarded, the IDS can be configured to record the event and immediately notify the security specialist so that the experts can act promptly against the attacker. Like an antivirus software, the product only works well if it updates the sample file or text file so your IDS is also advised to update in time.
Most intruders are very persistent and if they are unable to access through a separate road, other roads will also be tested one after another. Therefore, we must regularly read the logs and messages to update network issues. If you see any attempts to infiltrate from a particular source, you need to be aware of this action. Review the legal system to know what to do is right, quickly close gaps for deliberate acts that are quite destructive and soon resolve to avoid the complicated consequences caused by the attacker to organization.
A basic principle is to encrypt your entire network of data stores. Use passwords to protect all sensitive information and not allow users to browse insecure intranet sites because sensitive information can be stolen in this way.
 Response time
Response time
All security companies' responses need to be fast, accurate and effective. Your data and intellectual property rights are the property of the company and they need to be protected from intruders, set up warnings to inform the intruder trying to break into the system. or prepare to steal your information. Many security experts do not deal with attacks, but merely cut off an attacker's attack path. This simply trapped the intruder and if the intruder is identified, this intrusion will create potentially vulnerable holes. Note that your network is very large and consists of multiple computers in a block system, so you should choose a reasonable HIDS for each computer. There is a great advantage to this especially when there is a user in the group that goes from one location to another or users who bring their laptop computers home. The reason for this is that if you have a HIDS on the Host computer like a laptop, the user will be protected at any time, even if he is traveling around the world and is Connect to remote control networks outside your control. This is a great advantage and it is easy to see that HIDS will help although users are no longer behind the security of large corporate network NIDS. The response will be quicker and less support is needed because of the HIDS on the user's computer and making sure the user becomes an IDS that can protect the system until the user returns to the corporate network environment. .
NIDS (Network Intrusion Detection System)
Using NIDS poses a big problem for networks built on switches if port expansion is not allowed. By designing a switching function based on the principle of high-speed direct access, it only transmits the packets directly to the recipient but not the entire network like the Hub-based network. Some security networks operate in such a way that it cannot extend the port and that requires sensors, 'signals or checks' to be installed on each segment that cannot extend the port. This is one of the points where HIDS is superior to the NIDS because the NIDS is based on the network and the HIDS is based on the server. If your network does not have a strict profile, it is possible to extend the port and make a copy of all traffic transmitted on the switch to the expanded port. Note, port expansion is not available for switch devices and is different for each manufacturer. Enabling port expansion mode may also be at risk if the extended port is intruded by this intruder. Only a few small actions, such as port expansion, can be captured by an attacker, which can then break into your network.
A NIDS must be described as standard devices capable of detecting network intrusion. The NIDS may also be a software package you install on a dedicated workstation, which is connected to the network or a device with embedded software and the device is also connected to the network. After such a connection, the NIDS can scan all traffic transmitted on that segment; The NIDS works in much the same way as in an antivirus application and must have sample files or signature files to compare with the transferred package. IDS works in a suitable way to increase packet throughput, because when checked, packets can cause slow network. It will then use the firewall method when checking the package by passing the packets that it thinks are not dangerous. This process is done by preprocessor filters.
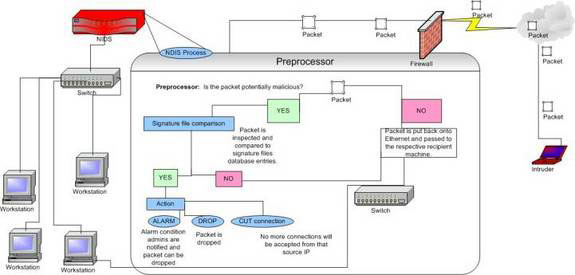
The above diagram describes the NIDS system;It shows the process of how the NIDS can compare the dangerous package with the list of signature files stored inside the database.The diagram also applies to HIDS, on the computer on which the HIDS is installed.
Comparative analysis between HIDS and NIDS
HIDS NIDS Function LAN Protection **** **** Both protect you when in LAN Network External LAN protection **** - HIDS only Easy to admin * *** **** Equivalent equivalent in general administration context Flexibility **** ** HIDS is a more flexible system Price *** * HIDS is a more economical system if selected right product Easy to add **** **** Both equivalent Equivalent short-term training **** ** HIDS requires less training than NIDS Total price *** * * HIDS consume less than you need Bandwidth required in LAN 0 2 NIDS uses wide LAN band, while HIDS does not Network overhead 1 2 NIDS need 2 network bandwidth requirements for any LAN Band should require (Internet) ** ** Both need Internet bandwidth to c p timely renovation sample files Requirements expansion port - **** NIDS required to enable expansion ports to ensure your LAN traffic is scanned upgrade cycle for the client **** - HIDS upgrades all clients with a central sample file Adaptability in ** **** application platforms NIDS is more adaptable in application platforms Local registers scan mode *** * - Only HIDS can perform these types of scans Logs *** *** Both systems have a log function Alarm function *** *** Both systems have scene functions for individual and administrators Scan PAN **** - Only HIDS scans your personal network areas Remove packets - **** Only NIDS features have this method Expert knowledge *** **** Need more knowledge expertise when installing and using NIDS for your entire network security issues Centralized management ** *** NIDS is more dominant Ability to disable risk factors * **** NIDS has more risk factors than Update HIDS *** *** Obviously the ability to upgrade software is easier than hardware. HIDS can be upgraded via a centralized script. The nodes detect multiple LAN segments **** ** HIDS can detect more comprehensive network segmentsHIDS (Server intrusion detection system)
HIDS are installed locally on a computer, making it much more flexible than NIDS. HIDS can be installed on a variety of specific computers such as servers, workstations and notebook computers. HIDS allow you to flexibly perform network segments that NIDS cannot perform. Traffic sent to the host is analyzed and transferred to the host if they are not potentially dangerous. HIDS is superior to NIDS in changing local computers. Meanwhile, the NIDS focuses on the large network that hosts those hosts. HIDS is more specific to platforms and powerful for the Windows market in the computer world, although there are still products that work in the UNIX and many other operating systems.
Questions for NIDS or HIDS?
Perhaps you are thinking about needing a NIDS or a HIDS? The answer here is HIDS for a complete solution and NIDS for the LAN solution. When managing an HIDS solution it requires less in-depth knowledge, while NIDS requires a lot of attention.
However, it should be emphasized here that if you install antivirus software not only on your firewall, but it is also installed on all clients. This is not the reason why both NIDS and HIDS cannot be used combined into a strong IDS strategy. It is quite possible to see that the NIDS is easily disabled in the context of an attacker. It is better to install multiple detection nodes in your enterprise network with HIDS than just having one NIDS with a few detection nodes that only scan one segment. If you are interested in specific computers, fear that an attacker will attack, you should use HIDS, as it will be a safer and equivalent decision to install a security warning for you.
IDS supports detailed records, many events are recorded daily, ensuring only the appropriate data is selected and you are not flooded with unnecessary data. HIDS has more advantages in this issue than NIDS when using an account to write to all machines on the network. If you are considering HIDS or NIDS, you have to make sure that there is a specialist that offers backup templates and techniques when there are new vulnerabilities. If you have a limited LAN band, you should consider HIDS. If price is an issue, you should also consider solutions. NIDS solutions are often more expensive than HIDS.
The diagram above shows the typical NIDS scenario, on which an attack is attempting to route traffic through the NIDS device on the network.The red device indicates where the NIDS is installed.
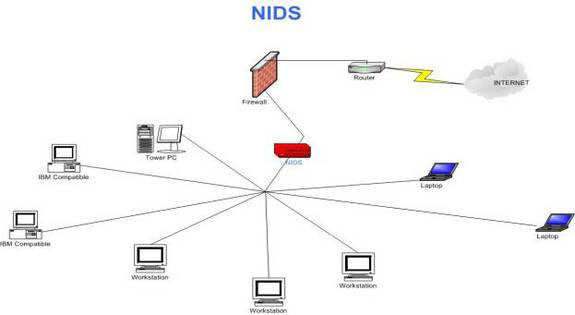
HIDS are a more comprehensive solution and show more robustness in network environments.It does not care where the computers are located and is protected at all times.Yellow machines indicate where the HIDS is installed.
Conclude
If you are not one step faster than an attacker, the attacker will quickly discover your weakness and attack. NIDS or HIDS can be fully protected in case you miss this important step, which is something you don't know, but the attacker knows very well. Finding the right app is not an easy task and we will provide documentation on this topic so that you can know when to choose the right product for your organization. . Today's computer network contains a lot of dangers, countless bad guys are fighting security security strategies. The only way to deal with them is to know what kind of attacks they are testing and resist those attacks. Strategy is the key and choosing the right strategy will be a good way to ensure that your network is kept safe. The information we shared in this article will help you make the right decisions when choosing NIDS or HIDS for the network.
Host-Based IDS and Network-Based IDS (Part 2)