Hardware in OSI reference model: Grade 7
 Hardware in OSI reference model: Grade 1
Hardware in OSI reference model: Grade 1
 Hardware in OSI reference model: Layer 2
Hardware in OSI reference model: Layer 2
 Hardware in OSI reference model: Grade 3
Hardware in OSI reference model: Grade 3
 Hardware in OSI reference model: Grade 4
Hardware in OSI reference model: Grade 4
 Hardware in OSI reference model: Grade 5
Hardware in OSI reference model: Grade 5
 Hardware in OSI reference model: Grade 6
Hardware in OSI reference model: Grade 6
Russell Hitchcock
TipsMake.com - This Part 7 will introduce you to layer 7 in the OSI reference model from a hardware perspective.
The seventh and final layer in the OSI reference model is the Application layer. This class can be said to be the most important layer in the OSI reference model, because it is said that because of not caring about network applications, there is no need to have a network. All the ways we interact with the network are through applications. For example, web browsers, email programs, IM applications, Voice Over Internet Protocol (VoIP) and many other applications are all network applications that interact with lower layers in the OSI reference model. and users.
The three common functions provided by these application class implementations are:
1. Ensure all necessary system resources are available.
2. Match the application with the appropriate application protocol.
3. Synchronize data transmission from application to application protocol.
Application layer protocols
Application layer contains both network applications and application protocols. Basic application protocols are rules about how to communicate with the application. Many application layer protocols are widely publicized like Hyper Text Transfer Protocol (HTTP). This means that any website that uses the HTTP protocol can transfer files from a web server that executes the HTTP protocol. Web browsers, web servers, and HTTP protocols work together to create network applications.
Some application layer protocols have proprietary rights and therefore are not available to the public; VoIP protocols are an example of this case. This is why you cannot use the same common interface to access your Skype account and you must use Skype's user interface.
Software and hardware
Most people think of application layer protocols like HTTP, SMTP or POP3, and think software applications are the interface of these applications. However, that is not always true. We can give an example where the interface for applications is hardware. For example, wireless phones are capable of connecting to VoIP accounts. In this phone system, the software in it makes it easy to assume that most of the work is done by hardware. In fact, however, your voice is captured by a microphone and the hardware handles it so that it is compatible with the VoIP application protocol by hardware next to the phone. This hardware might be the Application Specific Integrated Circuit (ASIC) or Field Programmable Gate Array (FPGA).
Another example of hardware implementation of the application layer protocol is inside Bluetooth. Bluetooth, in itself has many layers in the OSI reference model but we will focus on the application implementation layer. Inside Bluetooth devices, you can see many applications inside the application layer. One such application will be the application that will allow wireless headset devices, as shown in Figure 1, to communicate with a mobile phone in your pocket. In this case, the headset has a Bluetooth chip inside it, which converts the signal it receives from the phone into a headset in the headset through the hardware component. In contrast, the headset will receive an audio signal from the microphone and convert it into a form suitable for Bluetooth chips, which will then send signals to your phone. Here all are done through hardware.

Figure 1: Bluetooth headset
File transfer protocol
One of the most commonly used software applications within the application layer of the OSI reference model is File Transfer Protocol (FTP); or rather, FTP execution software applications are in the application layer.
FTP allows transferring files on the network. FTP requires two end points, one that acts as an FTP server and one that acts as an FTP client. FTP also requires two ports, one for data and one for control. The FTP control port is port number 21 and the FTP data port is port 20. Obviously the FTP client from the ports is randomly selected and not special ports.
There are two types of FTP; active and passive. In active FTP, an FTP client sends an FTP request to a control port of the FTP server. The FTP server then sends the requested data from its data port to the port specified by the client (on the control port). This is the original way FTP is designed. However, this may cause some problems. The problem is because, when the server starts sending data from its data port to a port on the client, it is very much like an intruder loading data from the client. With this method, many firewalls did not allow such data transfer.
Passive FTP has been developed to meet the security needs of the client. Passive FTP does not use standard FTP data port. The FTP server thanks to receiving a request from an FTP client that will reply with a normal port, on which port the data will be sent. The FTP client then sends a request to this port, then the port will reply with the requested data.
Voice over Internet protocol
As I mentioned earlier in this section, VoIP is also a network application within the application layer. VoIP is defined as a protocol used to optimize the voice transmission on packet-based networks. However, here we only mention the integrity of applications that implement such protocols.
VoIP is a good example of a family of applications that have many different implementations. Figure 2 shows the different types of VoIP implementations. All of these implementations can communicate with each other because they all rely on other classes in the OSI reference model. Whereas each implementation can use other implementations of different functions in other classes and each of these implementations is compatible.
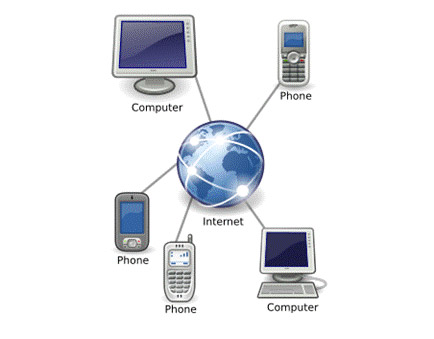
Figure 2: Implementation of VoIP
In general, the OSI reference model is a fairly abstract model, this model should be used as a guide for understanding how the network works as well as deploying network applications. By dividing each part of a design into classes in the reference model, designers will increase the usability of the application as well as make the application easier to maintain and upgrade. by the time.
The components of a design do not necessarily have to adhere to the OSI reference model, but in fact there are still arguments about which class will belong. However, there is one thing in practice that no matter which class it is, it doesn't matter because these functions work between classes. Other functions provided by classes may not be necessary and sometimes will not be present in the design; Encryption is a concrete example of this problem.