GitHub's machine learning tool can detect vulnerabilities in code
Code hosting platform GitHub has just launched a brand new machine learning-based code analysis and scanning tool. This tool has the ability to automatically detect common vulnerabilities in code before they are introduced into the final stages.
Currently, the tool is in public beta testing in GitHub's JavaScript and TypeScript repos.
"With new analysis capabilities, the code scanning engine can display more warnings for four common vulnerability patterns: cross-site scripting (XSS), path injection, NoSQL injection and SQL injection," the experts said. Tiferet Gazit and Alona Hloibna of GitHub shared.
"Aggregate data shows that these four types of vulnerabilities are the cause of many recent vulnerabilities (CVEs) in the JavaScript/TypeScript ecosystem and improved code scanning to detect these vulnerabilities early in the process." development is key to helping developers write safer code."
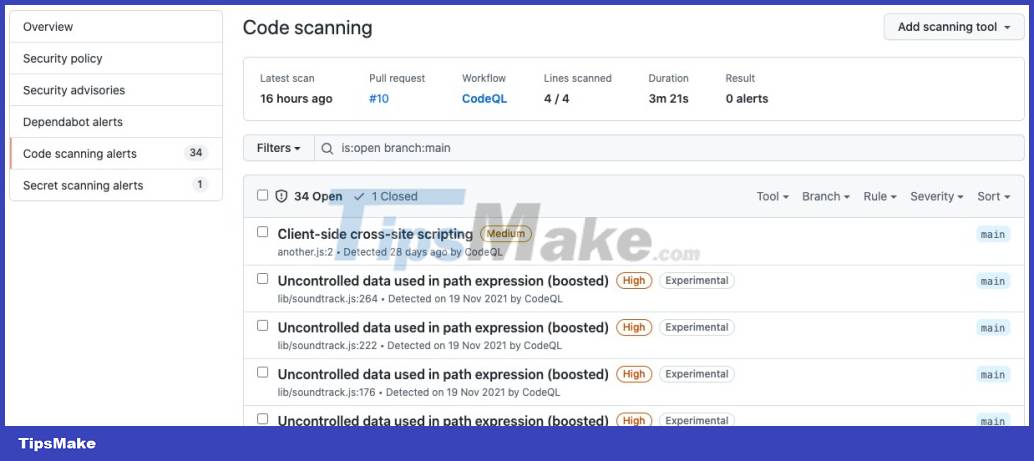
When a vulnerability is detected, the tool will display a warning in the "Security" tab of registered repos. The alerts are also labeled "Experimental" and are also available via the pull requests tab.
In fact, a code analysis tool called CodeQL was added to their platform by GitHub after acquiring code analysis platform Semmle in September 2019. The first beta of CodeQL was announced in May 2020 and available for everyone to test in September 2020.
During beta testing, CodeQL scanned more than 12,000 repos 1.3 million times and discovered more than 20,000 security issues, including remote code execution (RCE), SQL injection, and cross-site vulnerabilities. scripting (XSS).
CodeQL is free for public repos and available as an Advanced Security feature for GitHub Enterprise private repos.
Now, after adding machine learning, CodeQL's accuracy and code analysis capabilities will be further improved.