Avoid becoming a victim of 'Free Wi-Fi' bad intrigue
At some point if you are looking for a wireless access point, you might find a free point somewhere like in a coffee shop with free wireless access, but we warn you. concerned about accessing free spots to avoid becoming a victim of the latest hot-spot scams.
An attacker can steal your information that you send it on the Internet including username and password. You can also lose your files or identify them or end up with a computer full of Spyware and also your computer is in a bad life with spam. This attack even opens your computer to hackers every time you turn on your computer or allow anyone to connect without your permission.
If you use Windows Vista, you may be vulnerable to this type of attack because Vista is difficult to identify. In this article, you will learn how this attack is done and how to protect yourself when you use Windows Vista or XP.
Learn about this type of attack
First, let's look at how these attacks are done. When you go to a cafe or anywhere with a hot spot and turn on your computer (here we are talking about laptops - computers that support wireless access) to Access free wireless networks at these locations.
Normally nothing will happen, but there are some articles we have written about protecting yourself from wireless access points. But in this article is another content. The problem is that if this is not a real access point but instead it is a peer-to-peer ad hoc network, this network can be set up as a trap by someone with a laptop. nearby. You can use the Internet because an attacker has set up his own computer to allow you to access the Internet through his own connection. But because you are using his connection, all your traffic goes through this person's computer. That's why he can see everything you do online, including the username and password you enter on financial websites or other sites.
In addition, by directly connecting to an attacker's computer on a peer-to-peer network and if setting up a computer that allows file sharing, the attacker can 'walk' in the computer. your files, file and data theft or you can install other malicious software too.
You probably won't know anything that's going on, so you'll become a victim of this attack. The attacker steals what he wants or plugs in malware.
However, it did not stop there. Depending on how you connected to that ad hoc network, at a later time when you turn on your computer, it can automatically promote the new free wireless network ID and anyone nearby. You can also connect to a special peer-to-peer mode that you don't know - and can hurt you further if you configure file sharing.
If you use Windows XP
If you use Windows XP, protection against these types of attacks is quite easy: never connect to an ad hoc network of this type unless someone you know has set up and asks you to connect. So it is not necessarily where if you see a special network of this type is not connected.
Be aware that someone can name an ad hoc network whatever they want, maybe even copying the name of a valid network. For example, if you are at a coffee shop and the name of the free hot spot is the name of the owner, someone set up a special network with the name exactly like the hot spot. You will then see that both networks have the same name, a valid one, and a fake one.
In Windows XP, you can easily distinguish these two networks (an ad hoc network and a regular Wi-Fi network). To connect to a wireless network, click on the wireless network icon in the system tray and select the connection network that appears on the screen. You will see a list of all nearby wireless networks.
You can see in the picture below, each network in the window has a name and a description. Look at the description. If it is an ad hoc network, it will be called a "computer-to-computer" network. In the figure, the free Free Airport WiFi network is a special network that you should avoid.
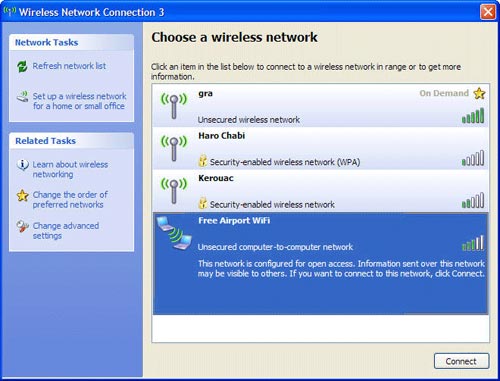
Windows XP displays nearby networks
There are a number of steps you can take to ensure that you do not randomly connect to this ad hoc network. For example, you can ensure that XP never connects to an ad hoc network. To do this:
1. Click the wireless icon in the System Tray.
2. Click " Change advanced settings "
3. Select the Wireless Networks tab
4. Click " Advanced "
5. On the screen that appears (shows nearby configuration networks), select " Access point (infrastructure) networks only "
6. Click Close and OK until the dialog boxes do not appear.
Note : If a wireless icon is not displayed in the System Tray, you can go to Start -> Settings -> Control Panel -> Network Connections . Then double-click the wireless connection icon to appear " Change advanced settings " link. Another link on some systems may be from Start -> Control Panel -> Network and Internet Connections -> Network Connections , then double-click the wireless connection icon.
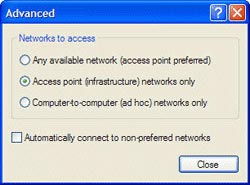
This screen will make your computer never connect to ad hoc networks
When you are on the ' Advanced ' screen you should also make sure that " Automatically connect to non-preferred networks " box is not checked. If this box is checked (checked), your computer will connect to any nearby wireless network without warning you, which can pose a serious security risk.
It is also a good idea if you are on the Wireless Networks tab to observe all wireless networks listed in the preferred network area (showing nearby configuration networks). If you see a network that is unsure, delete them. This way your computer will not try to connect to them anymore.
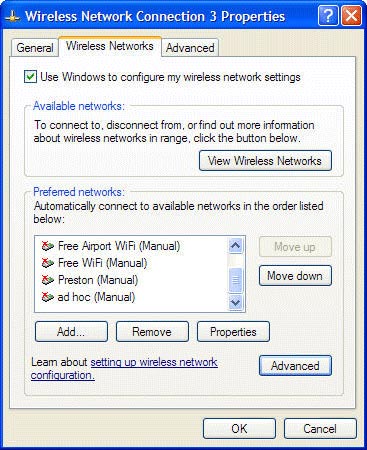
Delete any unknown network from the list of preferred networks
You should also configure preferred networks so you don't connect to them automatically. The question here is why to do so? Because that job says that your home network uses the default name transferred.
So in the preferred network area, select Properties then click the Connection tab, uncheck the checkbox near " Connect when this network is within range " and click OK until the dialog boxes are closed.
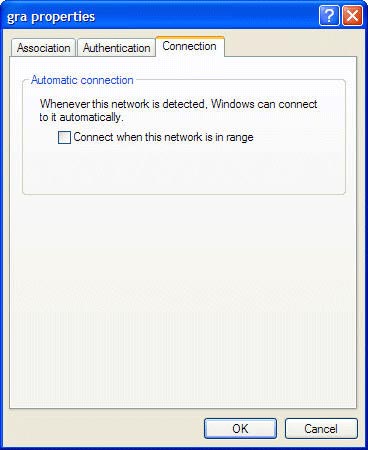
Make sure your computer does not make any automatic connection to the wireless network
Keep it safe in Windows Vista
Microsoft has put a lot of effort into building Windows Vista to make sure they are more secure than Windows XP, but when you have problems with wireless networks, you may be more at risk in Windows XP. That's because in Windows Vista, it doesn't easily distinguish an ad hoc network from a regular Wi-Fi network like in Windows XP. However, when you know the trick, you can do it easily.
In Windows Vista, you connect to a wireless network by first clicking on the network icon in System Tray, then selecting " Connect or disconnect ". The " Connect to a Network " screen is displayed with a list of nearby wireless networks. You will see whether the name of each network is encrypted or not; To get more details about any network, hover over it as shown below. However, these details do not indicate if this network is a real hot spot.
Before connecting to a wireless network, just by distinguishing an ad hoc network and the base node network, look at the network icon on the ' Connect to a Network ' screen. The symbol of a Wi-Fi network is a computer, while the symbol of an ad hoc network is many computers, that's it, and there's no other way to distinguish the difference between these two networks.
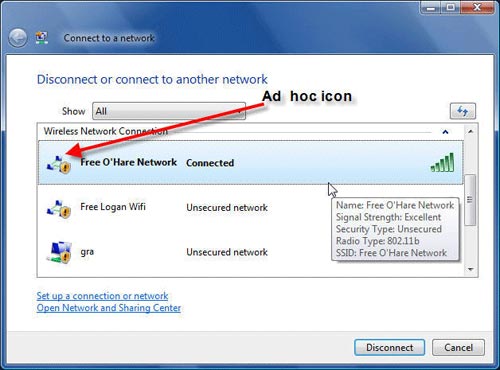
The only way to distinguish between an ad hoc and regular wireless hot spots is to look at the network icon on the screen
This is a special case: If you right-click a list of networks, one of them has a menu item selection and the others don't. Only networks that you have previously visited and saved in your network list will have the Properties menu selected. If you select Properties , select the Connection tab and look at the next type of network you will see as a good ad hoc network or a regular hot spot.
If you have never connected to any network (or you are connected but you do not save it), there will be no Properties menu option. So you cannot use this method to distinguish between ad hoc networks and regular Wi-Fi networks.