The spread of malware and how to prevent it
You often don't understand why viruses can infect your computer even though you have installed antivirus and are very careful. So which routes have they spread and how must they be prevented?
1. Spread via USB
Viruses usually create an autorun.inf file in the root directory of your USB or floppy disk. When it detects that a new storage device is plugged in (Windows, CD, Floppy Disk .), Window will automatically check the autorun.inf file in it, if it does, it will automatically execute the command line according to the structure. arranged in advance.
The usual autorun.inf file will have the content:
[autorun]
open = virus.exe
icon = diskicon.ico
The above command will automatically execute a file called virus.exe (virus file) and set the drive's icon to diskicon.ico . These files are all located in the root directory of the storage device. Assuming your USB drive is G drive, the file will be located in G: virus.exe . When plugging in the USB, the computer will automatically run G file : virus.exe if it has not been properly configured.
How to prevent :
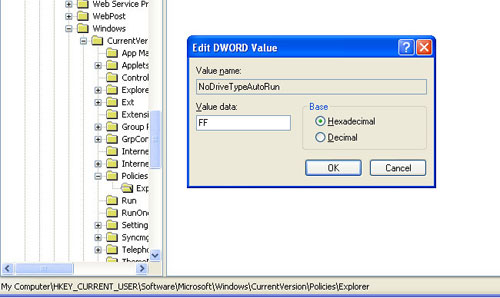
To disable autorun mode, go to Start - Run , type regedit and press Ok , on the left, you access the key:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionPoliciesExplorer
On the right hand side, double-click on the NoDriveTypeAutoRun variable and reset it to FF to disable the autorun of all drives. Click OK and restart the computer to take effect. You can visit here to see the clip that teaches how to disable autorun posted on QuanTriMang.
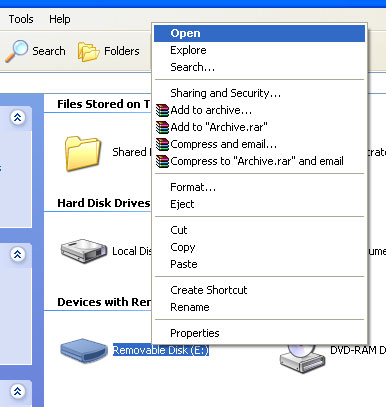
However, this only limits the autorun file's auto feature. If the USB has an autorun file that you double click on the drive, the window will still run. So you should use other methods to access the USB without double clicking, as well as fix this harmful access habit and instead of right-click, select Open :
If there is a virus in the USB (or autorun file), you can go to cmd and type the following 2 commands to delete (you must type both commands sequentially):
attrib -s -h [drive:] autorun.inf
del [drive:] autorun.inf
The first command is to remove the hidden attribute of autorun.inf, the following command works to remove autorun.inf. If you use the del command, cmd will not detect autorun.inf and the command will not be executed.
2. Spread through Yahoo! Messenger
Viruses of this type have been popular in Vietnam for a long time because of its high speed spread. Sometimes you come across some very interesting messages from friends and then a link to a strange website.
Something like: . click here, it's good http:/// [web link] .
And if anyone is not alert, they will accidentally click, suddenly your IE window will stiffen for a few seconds. The virus has been automatically downloaded to the computer and activated, only a few seconds later you will send unintentionally harmful messages to others like your friends.
How to prevent :
This virus uses a VBScript fragment attached to the sent web link that automatically downloads the exe file to the computer and activates it.
- Currently most browsers do not support VbScript, only Internet Explorer (the default browser of Windows) from version 6 and below still supports this type of code. It is best to download IE 6 or higher or use other browsers with more security like FireFox, Opera .
- Also before each strange link, you can look through its source to confirm it is not dangerous, you can use html code preview pages (www.viewhtml.com). Should pay attention to special keywords such as: vbscript, exe . However this method proved ineffective because in that website can embed some other url, and after a series of new embed urls to the link of the page web contains script.
3. Spread through the web browser
Like the way it spreads through Yahoo Messenger, when you access a link (a web page), you will accidentally visit infected websites (VBScript). The same solution as above, using good security browsers does not support vbscript to access the web.
4. Spread via Email, Outlook Express
Email utility is sure no one is strange, especially if you often check your mail, the job makes you contact with many emails. It is very difficult to distinguish which email has good or bad content or just spam. Hackers have taken advantage of email to "disguise" an e-mail with any address they want, with content as a card, an attached file or a link. These are all malware files that endanger the computer. So how to identify?
How to prevent :
This section is mainly based on your knowledge experience. You should be wary of general content mail. Suppose that at the beginning of the mail there is no Send / Hello section . Or do not specify the name: Please send me / Hello . the mail of this type with attached file or link, you should not download, Or you should scan the virus carefully before making sure to open it.
5. Spread into executable files
On a certain Sunday, you surf the web and search for software utilities to download. The websites you visit are clean websites (no malicious code, no viruses and possibly reputable websites). But even so, you still have the risk of getting infected without knowing when.
For some reason, the original application program after being transferred from one server to another . has been "attached" an additional virus (exchanged into a virus infected file). You have no idea whether it is dangerous or not, only to enable it, immediately, the virus has been added and executed on your computer from the application's installation file.
How to prevent :
Hacker after downloading an original application from the Internet, will use some 'exe joiner' software to be able to attach 2 exe files together. Then continue to upload other websites that distribute the virus-embedded application. The principle of attaching this exe can be easily understood as follows:
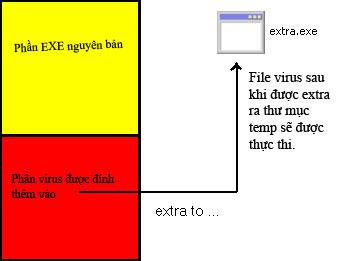
- The virus will be thrown at the end of the application file (or somewhere that does not affect the process).
- After running the application, the virus will automatically add extra to the temp folder (temporary folder of the window) and then automatically run the exe file with extra extra.
The way to prevent this is difficult, because hackers have hundreds of thousands of ways to cover our eyes. We can only 'review' the safety of the application.
If you already know through the structure of an .exe file, you should know the MZ section at the top of an .exe file, when it is attached to the application, there will be a certain identifier.

Normally, in an exe file with only one MZ phrase, if there are two clusters and in the foreground there is a strange sign, the setup file has been 'stuck with the virus'. You should delete the file and tell the provider or application store to not make many others infected.
In fact, the current antivirus software has the ability to identify the "sticky" virus types like this. But because defense and attack ability are always parallel, it is hard to avoid. This article helps you to grasp some of the causes of virus infection, giving you some knowledge of self-prevention & prevention.
You should read it
- ★ What is Crimeware? Is it similar to malware?
- ★ A new kind of malware is spreading through Messenger and Skype spam messages
- ★ [Infographic] 7 effective ways to protect businesses from Ransomware
- ★ Extremely creative room ideas around the world
- ★ Microsoft warns of new malware threat spread through Teams