Hidden patterns of malware
 Do you really understand the patterns of Malware? The malware hidden methods are often very complicated, are you sure after a long time using the machine you do not exist any harmful guys? Here are some of the hidden patterns of malware that make it very difficult to detect their existence on your computer.
Do you really understand the patterns of Malware? The malware hidden methods are often very complicated, are you sure after a long time using the machine you do not exist any harmful guys? Here are some of the hidden patterns of malware that make it very difficult to detect their existence on your computer.
DLL Inject
Hackers write a DLL (capable of injecting) with main DllMain function (will be automatically executed first when loading memory). Then, the malware injects this dll into one or more processes running on the machine. Especially injecting into the default Windows processes, such as winlogon.exe, explorer.exe . makes it very difficult to find and destroy these dangerous "parasites". Typical of them is W32.Kavo virus:
After being infected with kavo, it will create 2 files,% SystemRoot% System32kavo.dll (or some other names) and % SystemRoot% System32kavo.exe .
Next, kavo will inject the file kavo.dll into the process explorer.exe.

Kavo.dll after being injected is even more 'dangerous' than exe files. It is capable of executing commands like an independent process and can also mask the face by its own 'parasitic' method. Although you deleted the kavo.exe file, it quickly grew back. For these types of malware, you can use tools like Task Explorer, LordPE . to see the images loaded into the process.
Rootkit
Rootkits are essentially using a driver file (* .sys) that is capable of deep impact on the system, these driver files are written & used in the same way as DLLs with higher purpose and performance.

The most striking feature is that it has the ability to control the window to the highest level (ring0).
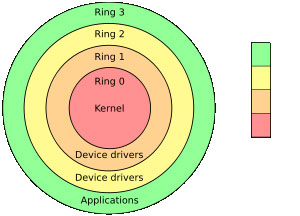
Ring levels ( Photos: Wikipedia )
The intruder's task is to create a service for these drivers by writing to the registry (for persistent malware types). The driver after being loaded into the service will not depend on processes like the dll inject method, we can only terminal service to control it when the object is correctly identified. The example of that is Rootkit.Win32.Agent.pp, after infection, it will create a file in% System% driversctl_w32.sys and create a key to automatically upload to the service:
[HKLMSystemCurrentControlSetServicesctl_w32]
"Start" = "dword: 0x00000003"
"Type" = "dword: 0x00000001"
"ImagePath" = "% System% driversctl_w32.sys"
Often these drivers conflict with the system so it often causes your computer to have a dump phenomenon (the local hardened machine with a blue screen indicates an error). Because of the deep interference of rootkits, it quickly became popular. The most typical functions of rootkits are: setting backdoor (back door), hiding process, and log intervention (when the highest level is available) .
For these types of malware, to destroy the requirement you must have a high level of system knowledge & rootkit. In addition, you can use some free rootkit detection tools such as Sophos Anti-Rootkit, RootkitRevealer, Panda Titanium, GMER or IceSword .
Hide Process & hooking
Like rootkits, hide processes are a powerful form of using hooking kernel mode and running processes. The 'super hidden' methods are difficult to identify, although you have used the view process quite strongly, but hooking is a seemingly varied problem, you can never be sure that there is no process Which is hiding on your computer .
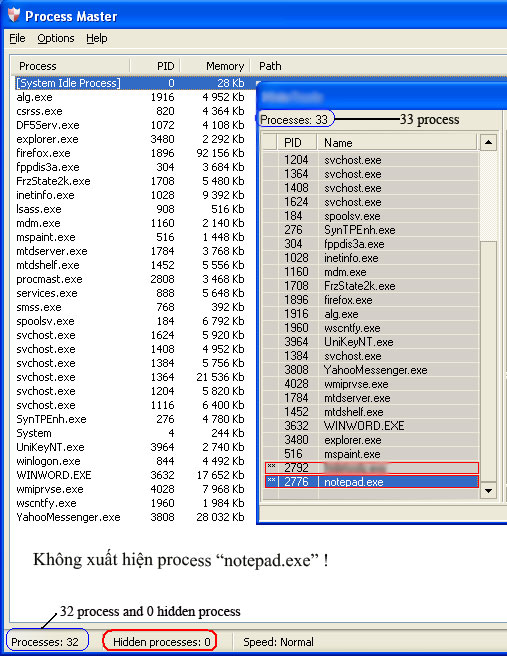
Test results when using Process Master to scan a process that has been 'hidden'
Infect PE
The potential danger when one of your familiar applications is infected with malware in a dynamic code way. This means that the attacker will insert a piece of code before the OEP (Original Entry Point) or change the original code of a familiar executable file running on the machine, such as YahooMessenger.exe, firefox.exe, UniKeyNT. exe & Vietkey.exe .
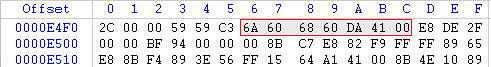
Original file (orginal)
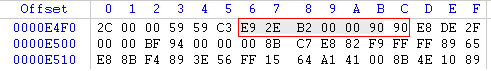
File Infected (code inserted)
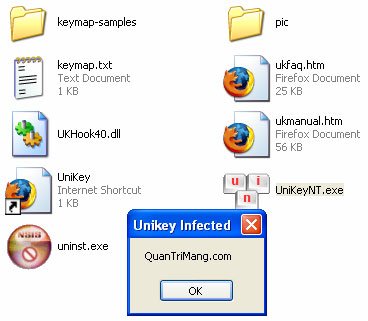
After modifying the code structure at the entry point (starting point of the program's code), every time it starts unikey will perform a dialog box then jump to the main program window. This is just one example of how to infect a pe file.
The above methods are just a few familiar patterns that senior malware can use to hide themselves on computers. Hope it will help you understand more!