The most dangerous places on the Web
Internet is a dangerous place and you can easily 'fall into the trap' of hackers if you do not know how to protect yourself. However, whether you are equipped with all kinds of defenses and are still infected with malware, online scams, or infiltrated into private data, read the following article to learn about some possible dangers, the level their danger and what to do to cope.

Flash websites
Flash files containing malicious code can infect your computer.
Adobe's Flash graphics software has become an attractive target for hackers in recent years, so Adobe must always update security patches. But other dangers that you don't know are Flash cookies. These cookies are small pieces of data that their creators use to store Flash settings. Like regular cookies, Flash cookies can also record the websites you have visited. However, when you delete browser cookies, Flash cookies are not lost but still stored on the computer.
Response: To avoid Flash-based attacks, always update Flash plug-ins in your browser. And you can set Flash plug-ins to always show notifications every time you download Flash cookies.
Twitter
Shortened links can lead you to dangerous places.
Internet scammers love Twitter because it has many shortened URL links, meaning that long Internet addresses will be shortened for users to remember. This makes hackers easily hide malicious code or phishing sites behind shortened URLs. A shortened link can lead users to attractive programs and services on the Internet but hidden inside can be Trojans.
How to respond: Simply don't click on links. Instead, you can use the Twitter client application, specifically TweetDeck and Tweetie for Mac that let you preview the entire URL before deciding to open the link or not.
Some services shorten links, for example Bit.ly, help filter links that contain malicious code, but you must perform the operations yourself. TinyURL is also a link preview service (tinyurl.com/preview.php).
E-mail mailbox
Ad-form e-mail or malicious attachment.
Although phishing attacks and malware infections via files (files) attached to e-mail are not new, they still cause many people to trap, and in some cases It is difficult to identify real content. For example, in the spam box, you see an e-mail with order confirmation content from Amazon. But if you pay close attention, you can recognize the e-mail address is not from Amazon, and this is a phishing email.
How to respond: Don't believe anything in your inbox. Instead of clicking on the link in the e-mail, you should go directly to the store's official website.
Torrent sites
Malicious code hidden in video, music, or downloadable software.
Torrent websites (such as BitTorrent) are a place to share 'pirated' music, video, or software, and also distribute malicious code. Since no one censors downloaded files on these sites, malicious code can disguise inside.
Ben Edelman, a security researcher and alternate professor at Harvard Business School, says websites that offer torrents are the most dangerous places because they are not based on a business model or a company's reputation. to protect (compare with porn websites that are believed to be reliable). Another point is that site users who offer torrents don't want to pay.
How to respond: If you need to access torrent sites, use another computer that doesn't matter, so if you have a virus you can reinstall it. Use antivirus software and keep it up to date. Scan downloaded files and wait a few days before opening them. Because at the time of downloading the file, anti-virus software sometimes does not update the new virus database.
Websites that allow peer-to-peer video or network sharing
Trojans camouflage under the decoder, infecting computers with malicious code.
If you watch or download videos online, the site requires you to install a codec (codec) - a small part of the software that provides video file format support - at least once. Typically, decoders are safe (for example, DivX is popular), but some download services or lesser-known video sites automatically transfer links to other places and ask you to download the solution. code, but the actual code is malicious. You can refer to how Trojan attacks are hidden in the decoder now, provided by security software company Trend Micro.
How to deal: The safest option is to access reputable video watch sites like YouTube, Vimeo. And if you want to watch the latest favorite TV shows, visit Hulu, TV.com, ABC.com, and iTunes; will be safer than peer to peer sharing model.
Smart phone (smartphone)
Positioning function (Geolocation) on smartphones and other devices can indicate where you are.
The smartphone market is not really stable. The concern here is that users use or abuse the positioning function. Although the use of locate data is legal, it is also possible to use this data for bad purposes. For example, a game listed in the Android Market list is actually spyware.
Figure 1: Some applications for smartphones, such as Yelp for iPhone, use location data to provide you with shops or entertainment near you.
Recently, Apple has updated its privacy policy to change the way data management is located on iOS 4. This policy aims to provide location-based services on Apple products. Apple, its partners and licensees may collect, use and share location-determining data (www.apple.com/privacy). You can read Apple's new privacy terms for further reference.
How to deal: You should find out about location-based services, applications, and websites. Services like Yelp are useful applications to locate. On the other hand, users should consider privacy policies when using services like Foursquare or Facebook Places feature on Facebook.
Search tools
Results from 'poisoned' search engines may carry malicious code.
The poisoning of search engines is a fact because there are websites or websites that are designed and 'trained' to achieve high rankings on a certain topic of search. For example, according to recent research by security firm McAfee, 19% of Diaz-related phrase search results and "Cameron Diaz and screensaver " screens contain links to malicious code. Topics that appear in the news section and on Facebook are also targets for online attackers.
How to deal: Select the sites to visit. Do not click on the link in the search results in a "blind" way, first check each URL to make sure this link will lead to the correct website. Although every website is at risk of being attacked, if you need to see the latest information on information technology, please choose the link to visit www.pcworld.com.vn for example, because this is the choice Choose smarter than clicking on a link to a strange website that you don't know.
Web sites are hacked or in e-mail inboxes
The malicious PDF document seeks to trick you into installing malicious code.
Malicious PDF files are files that have been inserted into malicious programs. These files will trigger errors in Adobe Reader and Adobe Acrobat applications; they are uploaded to websites that have been taken over. Taking advantage of these maliciously infected PDF files, hackers will take control of the computer and access your files and personal information.
A newer variation is that the PDF document looks harmless but has been inserted malicious code into it. Normally, Adobe Reader will warn you if you open a file with malicious code, but hackers can edit the content of this warning to 'lure' users to open the file. How serious is this problem? According to Symantec, in 2009, attacks using malicious PDF files accounted for 49% of web attacks.
How to deal: First, always make sure you run the latest version of Adobe Reader. You can use another PDF reader like Foxit Reader. This is a way to protect you from Adobe Reader vulnerabilities, but this is also difficult to ensure that you will be immune to all other PDF attacks, such as new variants that embed malicious code in PDF documents. As a precaution, you should update Adobe Reader 9.3.3 or later (for Reader 8 users should update version 8.3.3 or later). These updates change the way Adobe Reader handles non-PDF attachments and reduces the risk of attacks.
You can turn off the non-PDF attachment opening of Adobe Reader by going to Preferences , clicking Trust Manager , and removing the check box from the Allow opening box of non-PDF file attachments with external applications .
The next version of Acrobat and Reader will provide a new protection mode ('protected mode') to prevent attacks in this way.
Video download sites
Video files containing malicious code are used to exploit vulnerabilities in music player software to take control of the computer.
Last time, hackers often through holes in the video viewer such as QuickTime Player to attack users' computers. The virus transforms into regular video files, similar to PDFs with malicious code, taking advantage of errors in the video viewer, hackers infiltrating the computer and 'sowing' the malicious code.
How to deal: Regularly update the video player. Apple and Microsoft released periodic patches for QuickTime and Windows Media Player. Avoid downloading movies on lesser-known websites. Visit trusted video sites like YouTube, or download from services like iTunes.
Legitimate websites are attacked
Hidden installation code (Drive-by downloads) when you visit the website .
Malicious codes download and install offline without your knowledge. Some websites are built to attract people for the purpose of installing malicious code on computers that they don't know; however, the popular attack method is that hackers will attack legitimate websites and insert malicious code; When users access this site, malicious code downloads itself to the computer and installs.
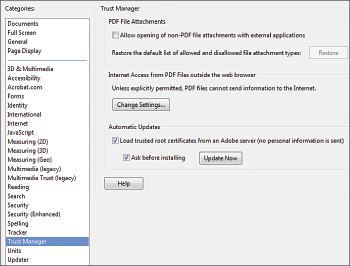
Figure 2: Uncheck the 'Allow opening of non-PDF file attachments with external applications' box to avoid PDF file attack.
How to respond: The first thing to do is update the security software and scan the system regularly to detect malicious code. Many security software can alert suspicious download programs.
E-mail mailboxes, legitimate sites were hacked
Fake antivirus software will 'steal' money and steal your credit card information.
The fake antivirus programs have the interface and the way they work like real programs and have the same warnings. However, you can easily identify fake programs through misspellings on warnings.
Most of the fake antivirus software are usually 'free': If you are using a trial version of the fake antivirus software, this software will continue to urge until you buy anti-virus software. fake virus. Once you trap, hackers can get your credit card information and use it for other purposes, such as buying high-value items in your name.
You may be infected with fake antivirus software for a variety of reasons, for example due to malicious installation of malicious code like the previous one, downloading of costly software has been infected and installed; unable to react when he realized the trouble etc.
How to respond: If you receive a message that you are infected, but this message does not come from an antivirus software that you know and intentionally install, then you should immediately stop any activity on your computer. Try booting in Safe Mode and run a scan of the system by using antivirus software from reputable security vendors.
However, the above method does not necessarily wipe out all malicious code, or scan but has not detected the malicious code, because the virus has now changed into another form. And if even using the behavioral virus detection method, finding malicious code based on how it works on the system, it is useless, you should look to a security specialist.
Advertising support website
Ads that are too hype on the web can lead you to phishing sites or malicious code.
Advertising is not wrong, this is a commercial form that helps the website survive and grow. However, hackers take advantage of advertisements on reputable websites to 'lure' users, such as last year, the New York Times page contained fraudulent ads, and earlier this year was a chapter-related case. Ads from Google with placing ads that look like links to websites of big companies.
A security expert from Sunbelt Software said attackers on the Internet are becoming more sophisticated in exploiting online security vulnerabilities and using tricks to bring malicious content into advertising.
How to deal: Most reputable websites such as PCWorld.com or PCWorld.com.vn will have advertising business department with the task of communicating regularly with a group of top advertisers. Therefore, you can rest assured to click on Microsoft advertising on the New York Times page. However, with Google 'accident', you should note that there is nothing absolutely safe.
Facebook
Suspicious applications on Facebook.
Security issues on Facebook applications have always existed so far. On Facebook, you cannot know who developed those applications, what they intend to do with the data collected. Although Facebook also lets you choose to use certain applications before they appear on your profile, your data has been in the hands of developers since then.
How to respond: Select the applications you plan to add to your profile - don't play all the puzzles. Check your privacy settings on Facebook apps: Click the Account drop-down menu in the upper right corner of the Facebook page, select Privacy Settings, and then click Edit your settings under 'Applications and Websites . From there, you can control applications that access your data. You can also turn off Facebook apps.
Social Network
Excessive sharing - 'exposing' too much personal information in your profile on social networks.
Over-sharing is no longer a personal problem, it can make your private data public to the community. However, users can avoid it completely.
Figure 3: Take a few minutes to check the application settings in Facebook to ensure the application privacy settings you want.
AVG security company said, there are unpredictable dangers on social networks that few people pay attention to. Users, especially teenagers, often leave all the real information they do not know that not only friends but also many others are viewing their information.
Excessive sharing can cause serious privacy problems, out of control. Today, young people can access credit cards through online registration forms, and disclosing this real information will easily lead to stolen personal data.
How to respond: This threat is relatively easy to avoid, just note what information you should register, what information is not like your home address and phone number, on your Facebook profile.
Finally, check out the privacy settings to make sure you don't disclose too much personal information, the most private secrets to 500 million people using Facebook.
5 safe ways to surf the web
Here are some tips from security experts to help you protect your computer from malicious code and hackers.
1. Always update the patch
Make sure you run Windows Update as well as software update features in other programs you use every day.
2. Use passwords smartly.
Do not use only one password for many different applications. You should use long passwords to hackers that are harder to 'break'. If you have multiple accounts, use the password manager.
3. Use security software.
This helps you prevent malicious programs and suspicious software. And in fact, security software companies also find it difficult to provide timely support for your computer to avoid infection before malicious code enters your computer. Please refer to reputable security and anti-virus software, regularly update the latest security products.
4. Don't be too gullible
Do not believe in a complete stranger, maybe half a world away from you, naturally offering you millions of dollars. Those are just typical online scams.
5. Be suspicious
Don't think that a computer with security software is absolutely safe. That is paranoid. You should remember that no security software is guaranteed to be completely safe for you and no secure website. Therefore, you should not rely entirely on links or download files and even email your friend.